Once you find yourself drowning in a sea of vulnerabilities flagged by countless scans, the pressing task at hand becomes which deficiency to fix first. This complex concern transforms into a far less daunting task when you master the concept of vulnerability prioritization with the utilization of threat intelligence operations.
Lara Meadows, VP of Sales Engineering, recently gave an insightful demo about this imperative process. She shed light on how to connect vulnerability management and threat intelligence to create an effective vulnerability threat library.
Building a Vulnerability Threat Library:
Click here to show transcript
Arpine Babloyan
Hello, everybody, and welcome to our June monthly demo, ThreatConnect. We are going to get started in just about a minute as we have more people joining. Um, in the meantime, I’m going to just give you a couple of logistical, uh, notes for today. You can control, um, how you see your screen using the control buttons at the bottom of where the presentation is. Um, you can see the button on the very bottom right that says toggle full screen mode. So you can press that to be able to see the screen bigger, and then you can also control how you see the presenters versus the screen. Um, we do have a chat option, which you can switch. Um, and when you see, I will actually put a message there. You can put your questions in the chat throughout the presentation, and we’ll try to answer them all at the end or as they come up. And if you have any questions to us after, you can message us directly, private message to myself, I run demand generation tier, so I’m on the marketing side, or Lara, who is our presenter. Um, so while we give it one more minute to wait for more people to join, you can test out the chat and put something, like, where you’re calling in from, for example, um, if you want. You don’t have to.
Lara Meadows
Um Or let us know what you’re doing this weekend, what fun you have planned this weekend.
Arpine Babloyan
Alright. Okay. Alright. Well, we just had a couple more folks join, so I am going to introduce Lara. Lara runs our sales engineering team. Lara Meadows is one of the most knowledgeable people in the industry. You’re really in for a treat to have her present, um, during this demo. She doesn’t do these often, so we’re very lucky to have you here do this today. And you’re very lucky to hear from her directly. So definitely soak in and, uh, don’t be shy. Feel free to ask your questions, and, um, we will get started in just about a minute. Um, I see there are awesome. Um, people joining. Perfect. So I think we’ll get started. And if anyone joins late, they’re always welcome. So you can invite your colleagues. With that being said, I am going to hand it off to Lara.
Lara Meadows
Thank you. Our point, uh, you have set the bar way too high and expectations way too high. Let’s lower them and just hope that we get through this. No. Um, thank you all. Thank you for joining on a Friday morning, early for this, or Friday afternoon depending on where you are. What we wanna talk to you today is really about, um, bringing together vulnerability management and, uh, threat intelligence. So what I’m gonna do is go through. I have a few slides, um, a couple of marketing, but really just, uh, more to talk about the overall solution and to get into the details of what we are doing here with ThreatConnect when it comes to vulnerability management and, um, threat intelligence. So we’re really gonna talk about building a vulnerability threat library. So with that, let’s go. Maybe. There we go. Okay. Marketing slide, obligatory marketing slide. We’re great. We have a lot of customers. Um, we’re all over the world. And one of the greatest things is we co-developed the diamond model. Our leaders come from the government, actually, and our founders, um, is one of the original developers and founders of the diamond model. So threat intelligence is really in our blood and in our bones, and that’s that. So okay.
So what’s going on in the world? We know that risks and attacks continue to rise. Um, the attack surface continues to expand. Right? And this only means more and more work for vulnerability teams. If you look at the attack surface that they have out there that they have to protect and they have to keep up with, it’s really getting bigger and bigger and broader and broader. And it’s a really daunting process that vulnerability management teams have to go to secure and to ensure. Uh-oh. Is somebody if you guys are hearing an echo. Okay. Good. Good. Um, okay. So there you know, this attack surface is really expanding, and it’s a really tough challenge, um, for vulnerability management teams. So if we look at a traditional the lifecycle that vulnerability management teams have to go through, it’s pretty straightforward. Right? They’re discovering vulnerabilities. They’re prioritizing them. They’re assessing which are most important to their organization, maybe building reports, maybe sending things out to different teams to remediate, you know, whether it’s the desktop team or it’s the forensics team. Right? Having people help with remediation, very verifying that the remediation took effect, and then repeating the entire cycle. Right? So constantly assessing what’s new vulnerabilities, how do I handle those.
What we are doing at ThreatConnect is, um, threat intelligence operations is what we call intelligence operations. And what we’re doing is it’s really talking about infusing threat intelligence into all aspects of your security operations. So whether we’re talking about cyber defense teams, whether we’re talking about incident response teams, whether we’re talking about your analyst teams, right, your tier one SIM analyst type things. Um, threat intelligence becomes a really critical component of these teams, understanding what their day-to-day operations and understanding what the greatest risks are. Right? So I like to say that threat intelligence teams are kind of the library in the back of the, um, office. They’re the ones who are pulling together all of that intelligence to help enable all of those different teams. So what we wanna talk about today specifically is the vulnerability management team.
But before we do that, uh, let’s take a look at our intelligence, um, lifecycle. And what you’ll see here is it’s very similar to what we just showed with the vulnerability management lifecycle. You’ve got the collection and the processing of intelligence at the top, and then you’ve got the dissemination, right, and the reporting at the bottom. What we like to do is take it a step further, and we look at the top of intelligence lifecycle really as the production of intelligence. And, again, it’s that curating. It’s pulling all that relevant information, making it useful, making it accessible so that we then disseminate it down to the bottom, the consumers. So in this case, if we look, um, we’re talking about CTI teams, and we’re talking about vulnerability teams. Right? How do we make this intelligence useful, rich, and relevant to, um, vulnerability teams? And that’s what we’re gonna be talking about today using this lifecycle.
So what’s the challenge that we see with vulnerability teams? You know, this is pretty straightforward for what you all know. Um, vulnerabilities are just increasing. Right? They’re getting bigger and bigger. They’re getting more and more impactful. Um, there are thousands. And I think I heard a stat or not a stat. I heard, um, a customer recently said they had something like 900,000 vulnerability. It was a ridiculous amount. How do you possibly get your arms around a scan that produces that many vulnerabilities? Right? And especially a lot of times when you see that the CVS score might not be relevant or might not tell, is it something that’s important or not important. Right? So how do we take all these vulnerabilities that are out there and make them relevant, prioritize them, and help that vulnerability team be able to do their job in the most impactful and effective way?
So where do I start? There’s a lot of vulnerabilities like we talked about out there, um, and even critical vulnerabilities. But what we like to recommend to our customers is starting with the ones that are being exploited, the ones that we know are actually being active and out there. Um, if you have a vulnerability that hasn’t been exploited in a while, it’s probably not a top priority for you. So, again, focusing on the vulnerabilities that are being exploited, the ones that are gonna, um, are critical, um, that are gonna exploit critical assets and the ones that are gonna impact financial you financially. Right? That’s where we recommend you focus, and that’s where we come into play. Being able to pull in that intelligence and being able to, um, provide that useful intelligence then over to the vulnerability management team to be able to do their work.
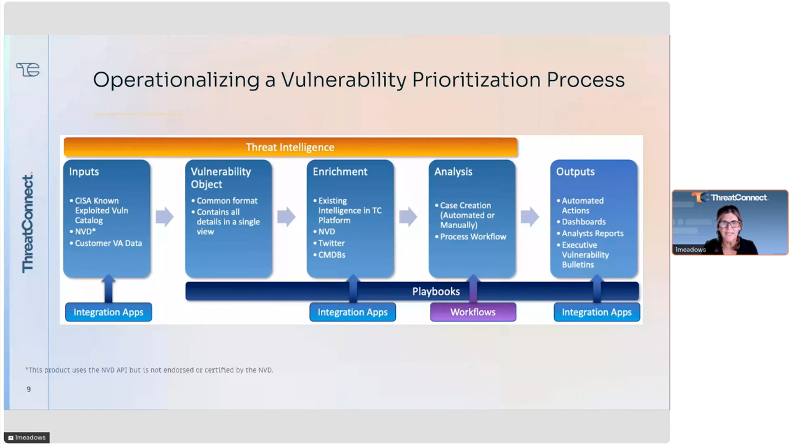
So how do we do this? So if we look at the process of what happens and this is what we do as we’re going through. We’re actually gonna do a demo of this, and we show each of these steps. If I receive a CVE, um, from a scan or from a team, uh, you know, the vulnerability management team, or I’m just reading about one. I’m gonna pull it into our, uh, threat, uh, our our tip and be able to pull in known associated information, whether it’s coming from CISA, whether it’s coming from NVD or other sources out there. Right? I wanna pull in as much information around that CVE as I can. I then wanna put it into a single view. So is NVD saying something different a little bit bit different than CISA? Is you know, there’s project zero, there’s vulnerability, um, phone check. There’s a bunch of different tools out there that have information. I wanna be able to pull that into a central view. Then I wanna actually be able to enrich it a little bit more. Maybe there’s blogs and reports. You know, maybe dark reading or somebody out there, Microsoft has put out a report about some sort of vulnerability. I wanna be able to pull that in. Twitter. Twitter is a great source for vulnerability and up-to-date information, or I guess we’re calling it X now. Um, and then I wanna be able to analyze it, pull in any remediation information, any detail that’s gonna help the vulnerability management team, and then I wanna spit that out and send it over to them. And that could be in the form of a report. It could be in the form of, um, details. It it just could or it could actually be triggering something automatically. Um, and that’s where we come to third party tools, having the ability to integrate with third party tools, like your network tools, like your, um, SIM, other things like that. And that’s really where the output comes into play.
So let’s take one more slide, and I promise this is the last one. Um, visually, what this looks like. So, again, in the middle is ThreatConnect. This is what we are doing. We are an aggregation. We’re an enrichment. We’re an analyzed tool that gives you the ability to pull in intelligence from all these different sources and be able to build a huge library that then gets, uh, used and has the ability to actually take action. And that’s one of the big differences when we talk about a tip. And as we go through the, uh, demo today, you’re gonna see that we do have the ability to take action using this enriched intelligence. So, again, um, stepping through what happens, I’ve got all these different intelligence sources out there. So there’s companies like Flashpoint that have awesome vulnerability, um, intelligence. Um, BoneCheck is a new one that we’ve seen up and coming. They’re doing this really cool prior to day day zero or right when day zero happens before CBD or NISA NIST or CISA, um, ends up doing their scoring. BoomCheck actually has the ability to pull up scoring ahead of time. Um, there’s open source intel. So like we talked about, CISA, NVD, you know, Project Zero. These are all open source places that are providing intelligence around vulnerabilities. We also have the ability to pull in your scans from your, um, vulnerability management solution. So whether you’re using Tenable or Qualys or even Rapid7, um, there’s a bunch of different ones out there, ServiceNow, um, CrowdStrike. Uh, we have the ability to pull in those scans and, again, start matching it with that information that we see over to the left, all those intelligences sources. From there, you can actually feed into a third party, um, ticketing tool. So if you’re using Jira, if you’re using ServiceNow, or if you’re using actually the case management built within our tool, which we’re gonna show today, you have the ability to actually automate and pull all the relevant information that’s gonna help that vulnerability team take an action. And then the last thing I wanna point out, we’re not really talking about this today, but I do think it’s relevant. Um, and it’s important to note that we have a second product that we don’t, uh, that we’ll do demos. I think every three months, we’ll do something around this. And this is our our our queue, our risk quantification tool. And what our queue has the ability to do is actually pull in those CVE scores and associate a financial, um, number with them, a risk number score and a financial number. So a lot of times when we’re talking about risk, we talk very figuratively. You know? Oh, it’s very risky. It’s a risk it’s a high risk item. With this tool, it actually pulls out a dollar value and says, yeah. This is a high risk. And, oh, by the way, you’re gonna lose a million dollars if you don’t patch this. So it gives you some monetary numbers so that you can actually start prioritizing financially, um, based on high dollar values. So, again, I’m not really gonna talk too much about that today, but did just.
In the video, Lara explores what it looks like to assist the vulnerability management team using the threat intelligence lifecycle. Every vulnerability management team is very familiar with the need to deal with the rapid increase in threats and this approach tackles that head-on.
Lara recommends starting with the vulnerabilities that are being exploited, especially the ones that could exploit critical assets or financially impact the organizations. This focused approach is to ensure threat intelligence is useful, rich, and relevant for the vulnerability team.
The conducted demo illustrated the step-by-step process of working with a CVE. You start by pulling it into your system, collecting known associated information from credible sources, consolidating that data into a single view, enriching it, analyzing it, and then dispatching it to your team. How you convey this information to your team could range from reports to automated triggering, depending on your specific needs.
ThreatConnect is an aggregator, enricher, analyzer, and action caller. There is an array of sources to feed into ThreatConnect, including companies like FlashPoint, open-source intel feeds, and scans from vulnerability management tools like Tenable and Qualys.
This aggregated, enriched, analyzed intelligence could then be used to perform single or multiple operations. You may want to integrate with your existing ticketing tool or automate it through built-in case management.
Lara explained the process of using ThreatConnect for an efficient, effective, and needed approach to vulnerability management. Prioritizing vulnerabilities based on real-world threats significantly reduces the time to remediate, ensuring a robust cyber defense. Additionally, associating a financial risk score with each vulnerability offering quantifiable insights, further streamlines the prioritization process. Thus, bridging the gap between threat intelligence operations and vulnerability prioritization is the way forward in current threat landscapes.