Posted
Cyber threat intel (CTI) teams, and organizations looking to stand up a new CTI function, face a variety of challenges. Many organizations jump into CTI without enough (or any) planning, which leads to a host of issues, like knowing what type of data sources are needed, what kind of intelligence needs to be produced, how it will be shared, and ultimately how will value for investments in CTI be measured and demonstrated.
From a technical perspective, many CTI teams face big-data challenges like their peers in threat detection teams. The sources and volume of cyber threat intel data and information is continually growing. There is an increasing variety of intel ranging from indicators to tactics and techniques across the clear, dark, and deep web. The speed at which intel is produced is accelerating. And CTI teams need to determine the veracity of all this data.
How do cyber threat intel teams at various degrees of maturity address these challenges? People and processes are important elements, but having the right technology to support the people and enable the processes is critical.
I like to frame the maturity discussion and required platform in the context of the Pyramid of Pain.
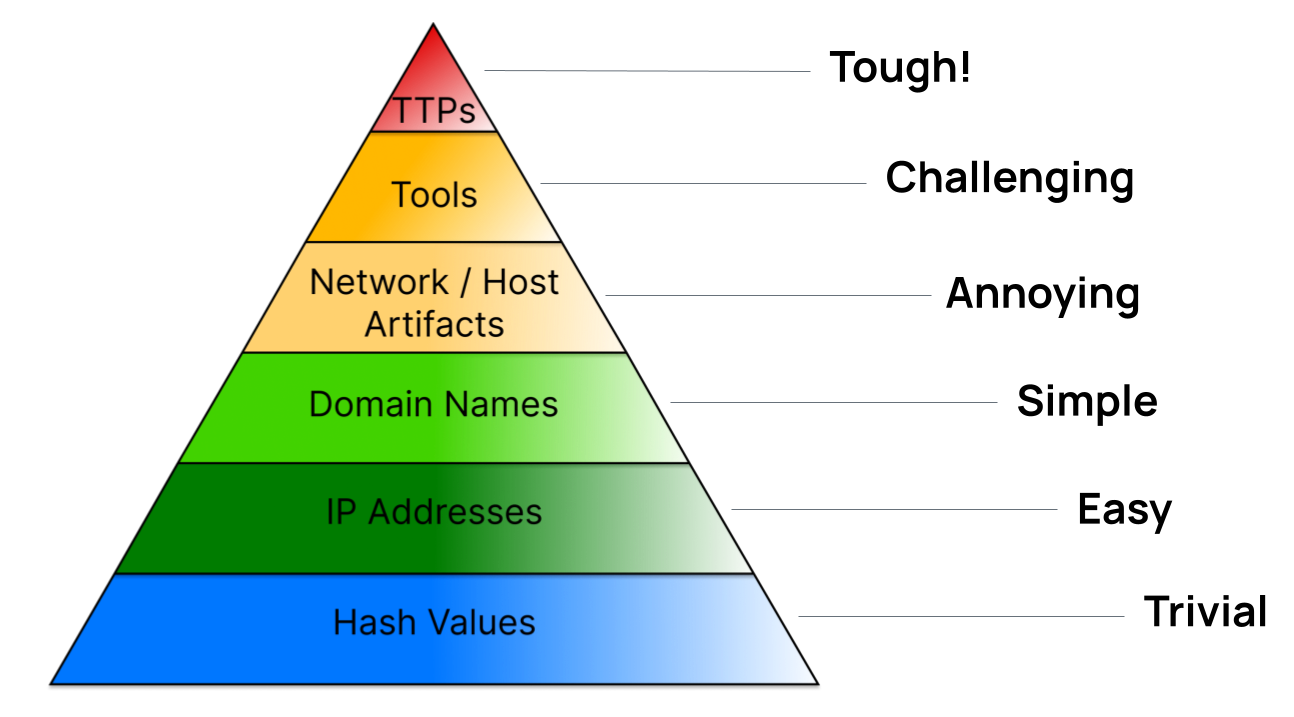
The Pyramid is a convenient method for assessing the value and application of cyber threat intel and the effect it has on a threat actor achieving their objectives against an organization. For example, the lower sections of the Pyramid deal with indicators like file hashes, IP addresses, and domain names. These are common indicator types that have utility in detecting and blocking threat actor actions. However, the level of utility, i.e., the amount of pain it inflicts on an attacker during an attack, isn’t that great. Attackers can easily change the hash of one of their tools. They can use fast flux techniques to change IP addresses. They use hundreds of domains to facilitate an attack. As you go higher in the Pyramid, the focus shifts towards less dynamic and more static indicators, such as the infrastructure used by attackers, and at the top is understanding the behaviors of the attackers by tracking and analyzing their tactics, techniques, and procedures (TTPs). The maturity of CTI teams generally aligns to the type of intel they are producing (operational, tactical, and strategic) and the type of threat intel data they use.
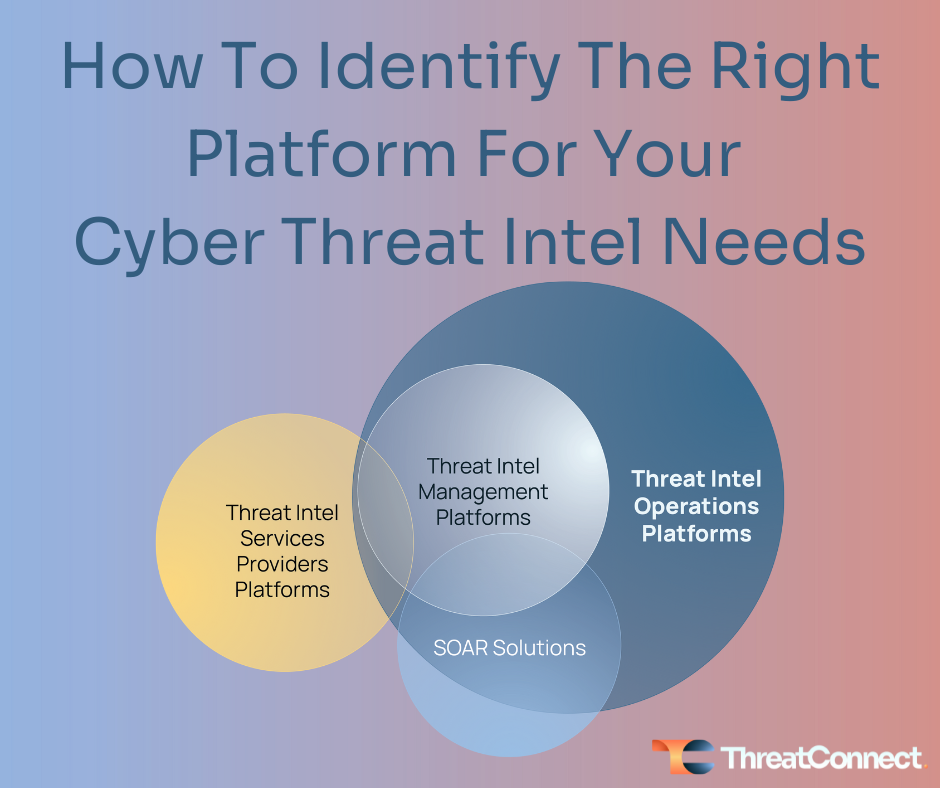
Depending on the specific needs of the threat intel team, and broader cybersecurity team, there are different available solution paths – threat intel data services providers (some with their own platforms), threat intel (management) platforms, security orchestration, automation, and response (SOAR) solutions, and threat intel operations platforms (TI Ops). There can be a lot of variation between these platforms. One thing is common: they can help manage threat intelligence, but most struggle to operationalize it.
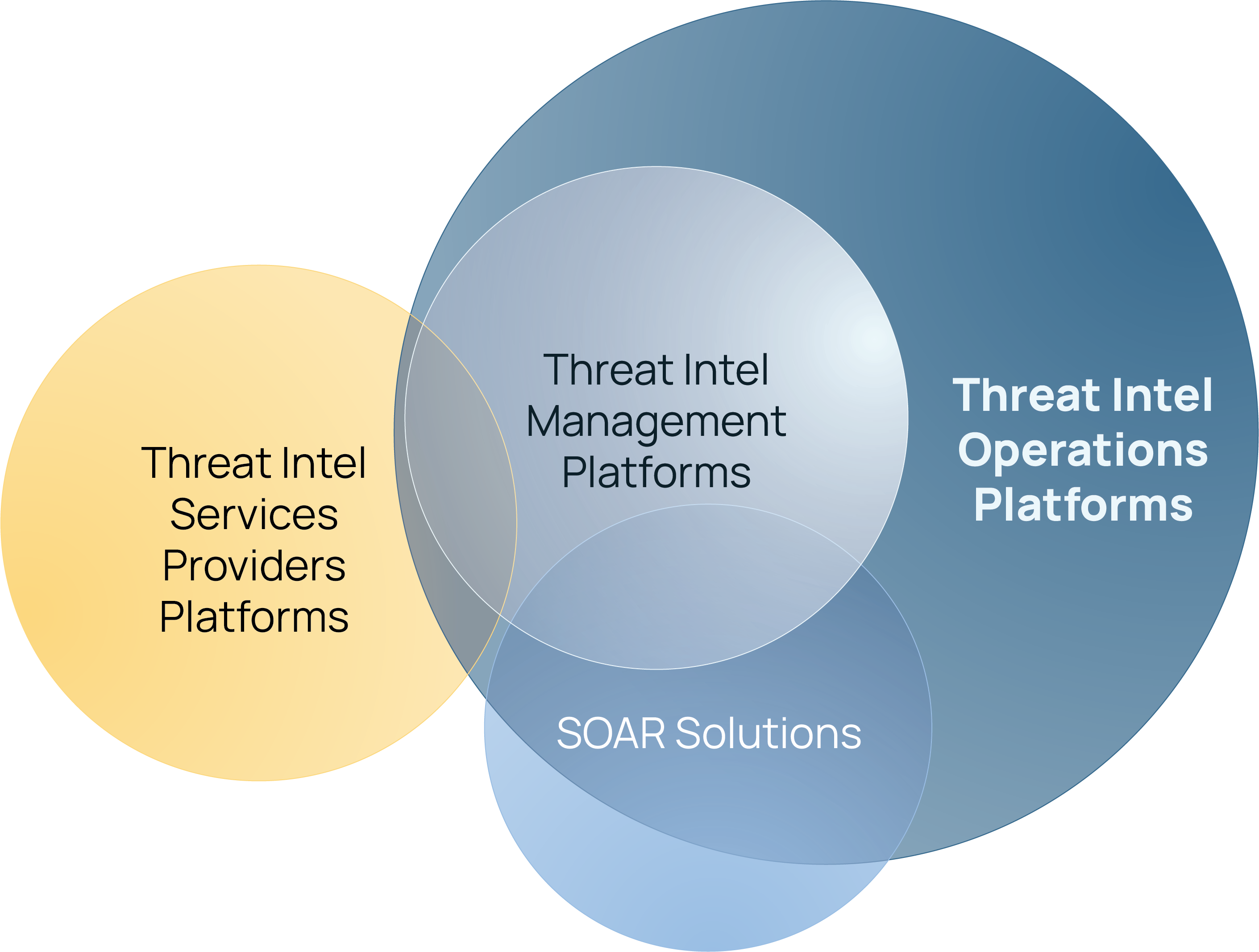
Low-maturity organizations commonly choose to use a single source of threat intel, such as from commercial threat intel data service providers. This is a completely valid approach that aligns with their requirements, use cases, and CTI investments. The use cases here are likely to focus primarily on using operational threat intel (the lower levels of the Pyramid of Pain) to enhance threat detection and prevention use cases, e.g., improve the ability to defend against threats through detecting and blocking indicators via their security tools like SIEM, firewalls, endpoint protection, EDR, NDR, SSE, CNAPP, etc. In this scenario, the platforms provided by commercial threat intel data providers that enable the providers’ intel to be pushed to downstream security tools is sufficient for the CTI team. The reports and alerts they provide can be manually consumed and actioned using other tools whether it’s collaboration tools (O365, Google Workspace) or ticketing systems (Jira, ServiceNow).
Organizations going up the maturity curve who are adopting more threat intel from a wider set of sources, such as multiple commercial intel data services, open source intel sources, and trusted partner sources, are going to need a platform that can handle more intel data and distribute it to a wider variety of sources. They may still be primarily focused on operational intelligence, but are starting to invest in producing tactical and strategic intel too (the upper layers of the Pyramid of Pain). There is more analysis happening, but the focus is still heavily centered on use cases where intel is primarily shared in a machine-to-machine manner, e.g., sending indicators to a wide variety of security detection, prevention, and response tools. This is where threat intel platforms, and SOAR tools with threat intel capabilities, are popular because they can generally handle the aggregation, processing, and dissemination of machine-readable intel and support basic intelligence analysis needs.
Operationalizing intel requires the ability to:
- Benefit from AI-powered analytics to deliver insights difficult to uncover through manual effort and analysis
- Actively support intel consumers by ensuring their requirements are captured and being actioned
- Automate analyst work to make them more effective and efficient
- Standardize processes and activities to ensure consistency across analysts and teams
- Capture knowledge and insights to improve collaboration and improvements
Threat Intelligence Operations Platforms include all the features that TIPs and many that SOARs include, but in a highly integrated way that enables CTI teams to operationalize their threat intel across a wide set of intel producer and consumer use cases.
Identifying the right platform for your cyber threat intel program is critical. A TI Ops platform should be your solution in order to achieve the most efficient and effective aggregation, processing, analysis, and dissemination of your threat intelligence whether you’re at the beginning of your CTI journey or you’re maturing your CTI function.
Take the next step
To learn more about the differences between the platform options available to CTI teams, download our Identify the Right Platform for Your Cyber Threat Intel Needs eBook to learn more, or reach out to one of experts to learn more about the ThreatConnect TI Ops Platform.