Buyer’s Guide for Cyber Risk Quantification Solutions
This guide equips CRQ solution buyers with the knowledge to assess and determine the appropriate solution across a variety of use cases when implementing or evolving a CRQ program.

Define business priorities. Identify critical assets and systems. Ingest asset inventories, control performance data, and vulnerability context from across your security stack.
Simulate real-world attacks with MITRE ATT&CK and data from your control environment. Quantify financial exposure based on control performance, threat likelihood, and business impact.
Surface your most financially significant risks. Create board-ready reports. Defend budget and investments with dollar-backed metrics.
Trigger remediation workflows via tools like Jira or ServiceNow. Track measurable risk reduction over time. Continuously refine based on evolving threats, assets, and controls.
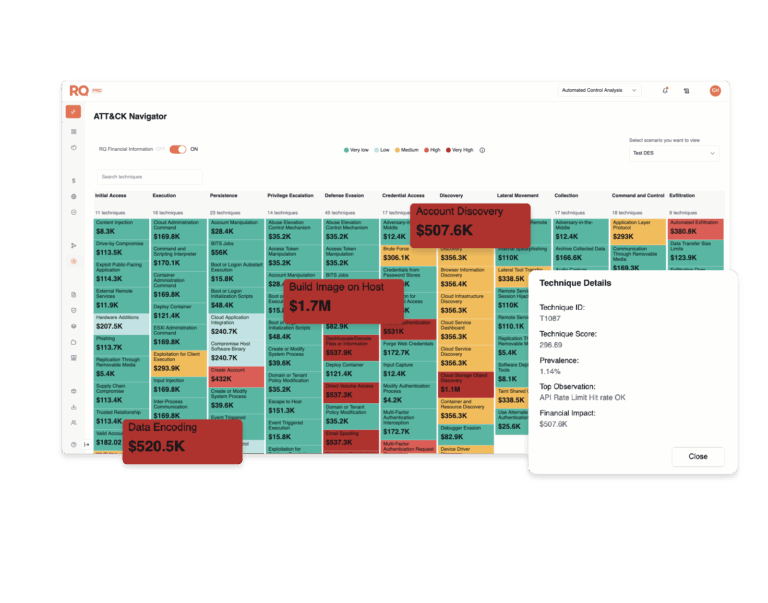
Start Fast with ROI-Driven Prioritization
Show value fast. Cut through noise. Operationalize your CRQ program with clear priorities rooted in your attack surface and financial relevance.
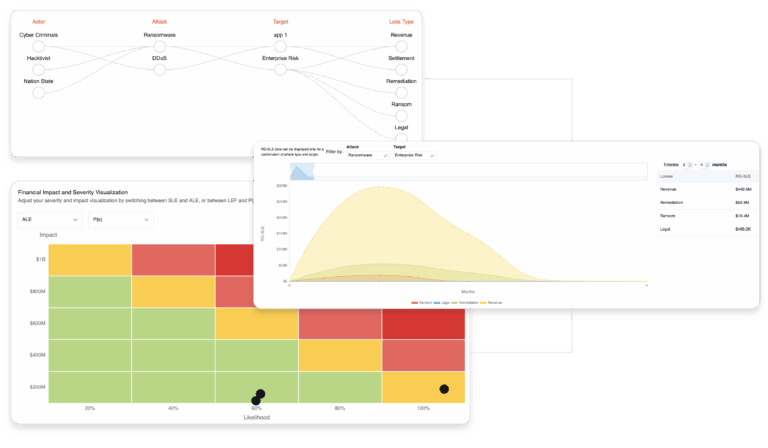
Scale CRQ Across Workflows, Scenarios, and the Boardroom
As your cyber risk quantification program matures, RQ empowers you to scale enterprise-wide, modeling exposure across business units, third parties, and M&A activities.
Pull identity data from platforms like Okta and Entra to associate users, devices, and assets.
Uncover access-related risk paths and quantify user-centric threats.

Connect to EDR and vulnerability tools like CrowdStrike, SentinelOne, and Qualys.
Surface asset health, known exploits, and control gaps in one view.

Ingest firewall and NDR data from Palo Alto, AWS, GCP, and others.
Model exposure based on known traffic patterns and threat behavior.

Pull from tools like ServiceNow CMDB/IRM and SureCloud.
Assess how controls apply across services, apps, and operational workflows.

Power CRQ with telemetry from across your stack.
Ingest from ThreatConnect TIP, Zscaler, Snowflake, and other data lakes.
Feed modeling logic with enriched intel, telemetry, and asset metadata.


Customer threat-driven risk models based on live MITRE-mapped TTPs and control data
Financial impact built into every output-not hypothetical, always tied to real assets and threats
Automated scenario modeling without requiring deep FAIR or quant expertise
Real-time integration with tools like Wiz, CrowdStrike, and ServiceNow
Enough flexibility for boardroom metrics and daily triage workflows
A unified Intel Hub that connects threat, risk, and SecOps decisions in one platform.
85% annualized savings across dozens of OT risk reduction projects
Quantified cyber risk across 250+ applications and 30+ entities within the first 3 months
Reduced risk analysis turnaround from four weeks to just 1–2 days
Benchmark financial risk across 40+ business units

This guide equips CRQ solution buyers with the knowledge to assess and determine the appropriate solution across a variety of use cases when implementing or evolving a CRQ program.

Explore how GPC optimized their cybersecurity strategy using ThreatConnect's Risk Quantifier, transitioning to data-driven analyses for better risk management and investment decisions.

Understanding Cyber Risk Quantification with ThreatConnect’s Risk Quantifier Click here to show transcript Tim Wynkoop: Is we want to be able to show you, um, our risk quantifier product. Um, and the goal of this product is really just to help you report risk, um, and we’re gonna use this terminology from the board […]
To map threats, vulnerabilities, and TTPs to financial impact using live intelligence
By aligning alert triage and response workflows to the business risks that matter most
To surface risk scores and priority context directly in analyst workflows – no integrations needed
By turning technical exposures into board-ready metrics, driving better planning, prioritization, and budget justification

Trusted By Leading Companies
ThreatConnect Risk Quantifier has revolutionized our approach to security investment decisions by shifting from generic industry benchmarks to precise, environment-specific threat intelligence. RQ empowers us to allocate resources strategically, reduce organizational risk effectively, and provide the accountability and clarity our board has been seeking for years.
ThreatConnect has a vision for security that encompasses the most critical elements – risk, threat, and response. The RQ solution strengthens their offering and increases alignment to our core strategic objectives with one platform to assess our risk and automate and orchestrate our response to it.