Why CVSS Fails Defenders
Every vulnerability scanner can output a list of “critical” CVEs. But CVSS severity isn’t defense — it’s categorization. The result: endless backlogs, patch queues that never shrink, and executives who don’t see value.
85% of known exploited vulns (KEVs) remain unpatched after
30 days.
55% of teams admit missing critical alerts due to ineffective prioritization.
It takes organizations an average of 55 days to patch just 50% of their critical vulnerabilities.
The Three Questions That Matter
The real challenge isn’t just ranking CVEs by score. It’s answering:
- Is it actively exploited in the wild?
- Who is exploiting it?
- What would it cost my business if they succeed?
When these questions drive vulnerability prioritization, remediation becomes risk reduction — not just hygiene.
A New Definition of “Done”
- Exposure windows shrink because exploited vulnerabilities are fixed first.
- Executives see remediation as financial ROI, not a compliance chore.
- Security and IT work from the same list instead of fighting over patch queues.
- Analysts focus on adversary tradecraft, not manual deduplication.
How ThreatConnect Delivers the Answers
ThreatConnect unites known exploited vulnerabilities, threat actor context, and financial risk into one view.
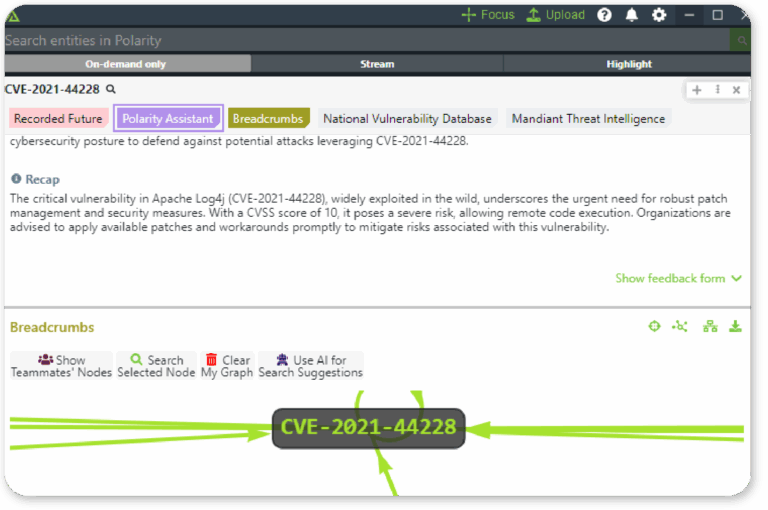
Contextualize
Enrich scan results with live intel, separate KEVs from “scored criticals,” and correlate to adversary campaigns.
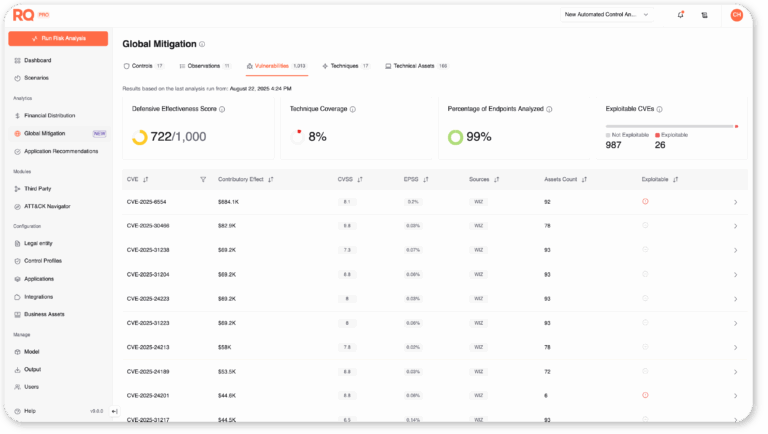
Prioritize
Combine exploit likelihood with modeled financial loss to rank what really matters.
Act & Adapt
Automate deduplication, ticketing, and workflows across ServiceNow and Jira. With Polarity, deliver intel overlays into SOC, IR, and vulnerability management workflows.
Transform Vulnerability Management with Intelligence
From centralizing data to prioritizing by financial risk, empower your teams to turn endless CVSS lists into actionable, context-rich strategies.
Getting Started
Centralize vulnerability data
- Use TI Ops to aggregate scan results with threat intel. “We help you replace endless CVSS lists with intel-driven context.”
Map vulnerabilities to adversary behavior
- Align exposures to MITRE ATT&CK TTPs. “Which techniques are your weaknesses tied to?”
Kick off remediation workflows
- Automate ticket creation in Jira/ServiceNow. “That vuln? It’s linked to an active ransomware campaign.
Grow With Us
Prioritize by financial risk
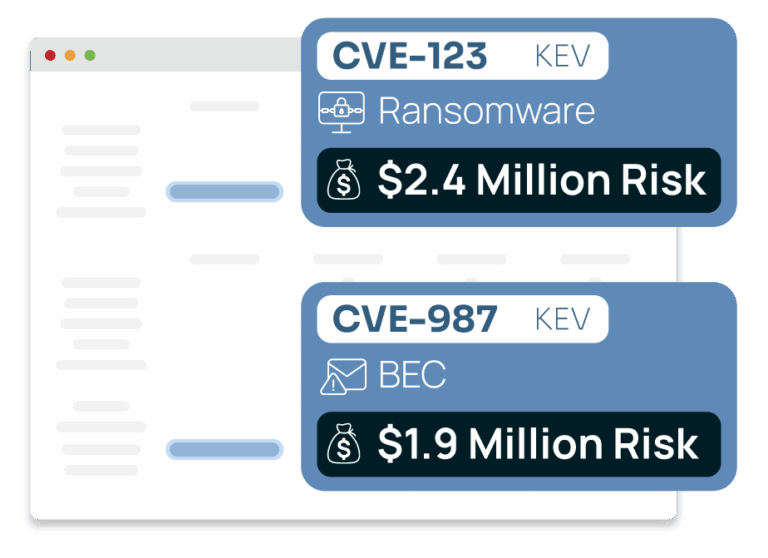
- Quantify vulnerabilities by business impact. “Which exposures could actually cost you millions if exploited?”
Continuously measure exposure gaps
- Visualize risk trending across adversaries, assets, and controls. “Are you shrinking the attack surface, or just patching blindly?
Only in ThreatConnect
Prioritize vulnerabilities by financial risk and known exploitations, not just CVSS scores
Tie exposures to live adversary exploitation data
Translate vulnerabilities into business impact executives understand
Provide real-time overlays linking alerts, assets, and threats in analyst workflows
Automate ticketing and remediation playbooks across IT and SecOps tools
Continuously measure and visualize exposure reduction over time
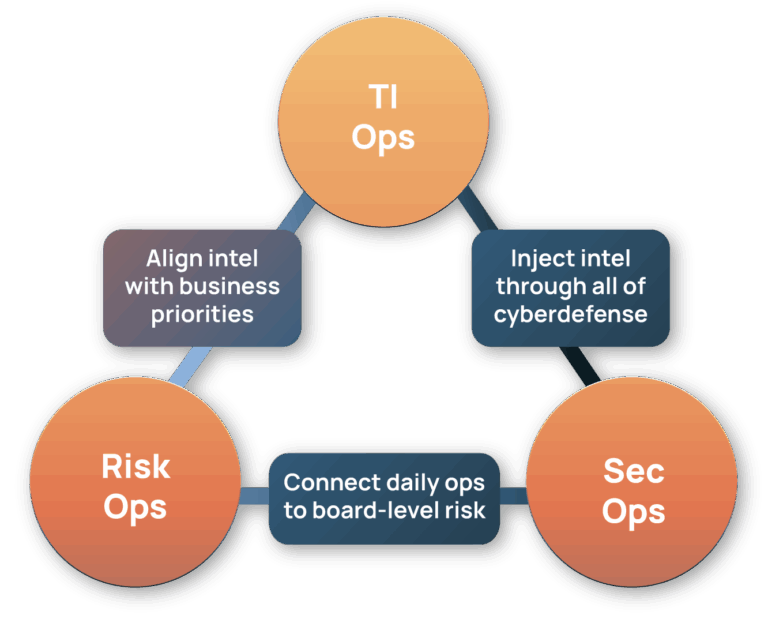
Powered by the Intel Hub
TI Ops
Enrich and structure vulnerability data with live intel and ATT&CK mapping.
Polarity
Overlay KEV and actor context in any workflow, without switching tools.
Risk Quantifier
Translate vulnerabilities into financial exposure and prioritize by business impact.