Unleash Efficiency Through Automation
Change the game by automating the mundane, creating more time to focus on high value analysis and collaboration. With playbook automation and AI-powered threat insights, you’ll unlock efficiency and effectiveness for CTI and SecOps teams.
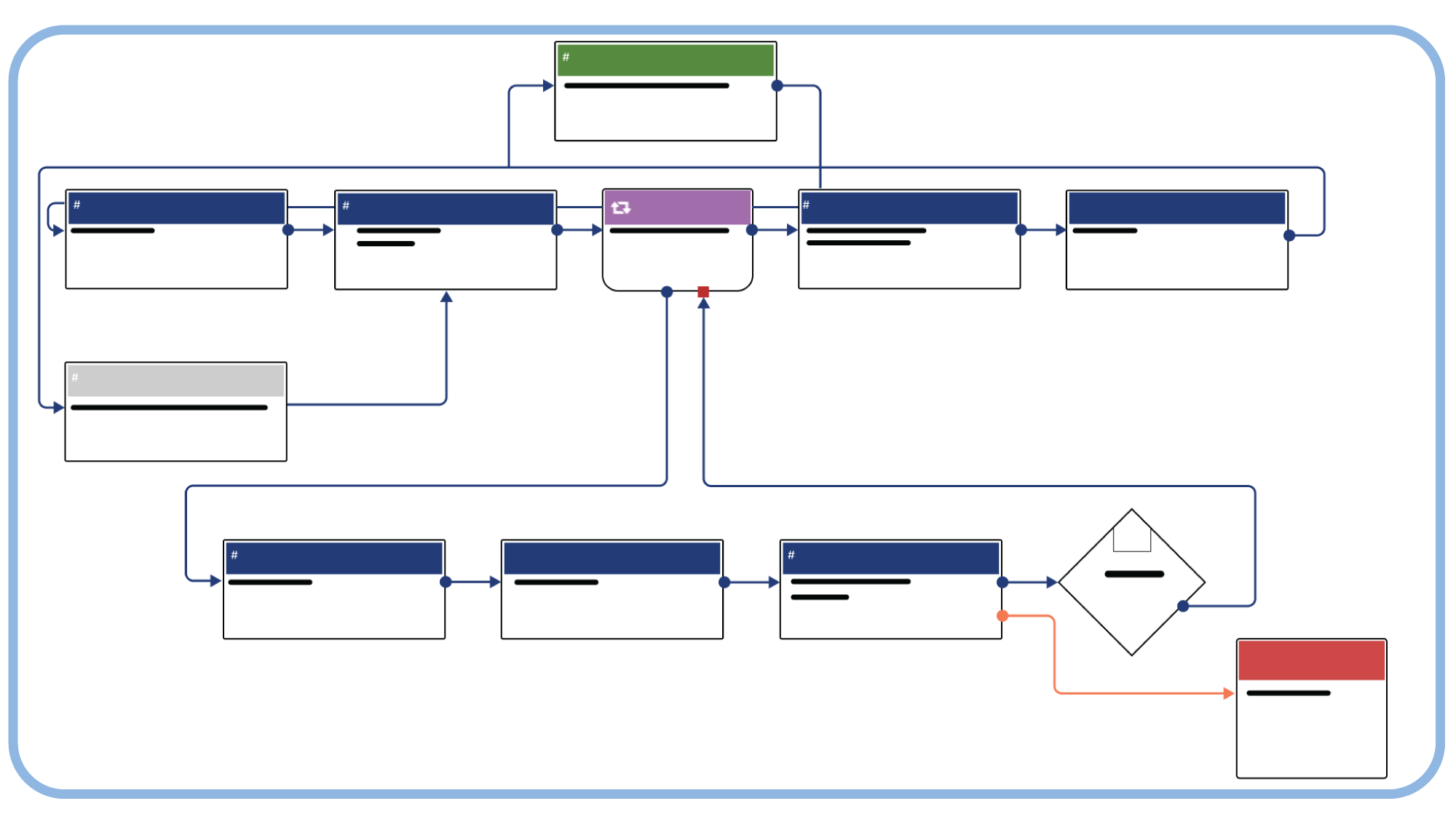
Build Playbooks with Ease
Quickly automate your custom processes. Playbook automation reduces the need to be a coding expert through our easy-to-use, drag-and-drop interface.
Save Hours with AI and Automation
CAL™ Automated Threat Library (ATL) aggregates and analyzes more than 60 authoritative sources of open-source intel. Save time and effort with automatic detection of ATT&CK tactics and techniques, CVEs, indicators, and AI-generated summaries. Analysts love CAL ATL because it saves hours of manual effort every day.
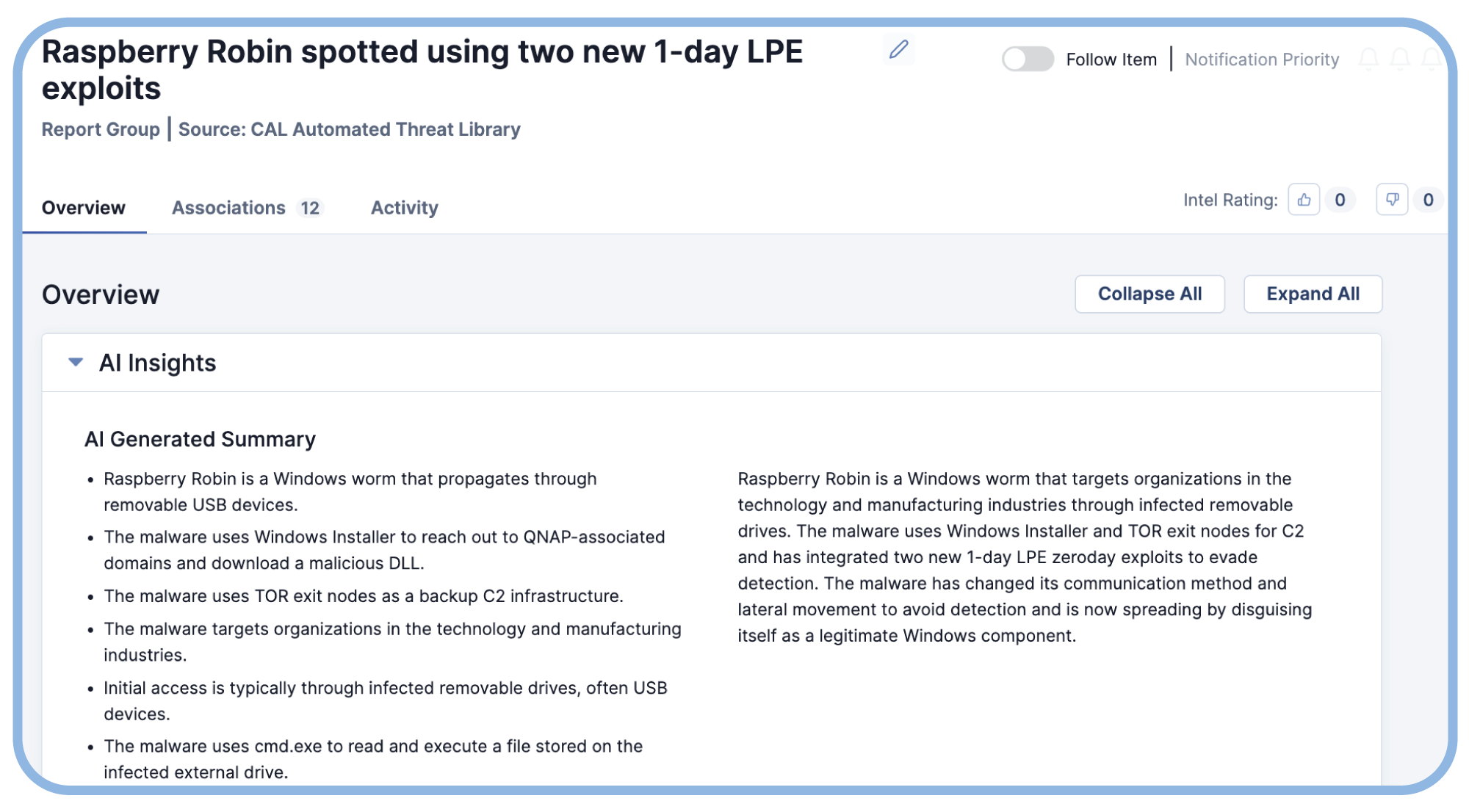
Get Automated Intel Context
Streamline your threat intelligence analysis with automated intel enrichment. Built-in, automated enrichment leveraging third-party sources like Virus Total, Shodan, DomainTools, URLScan.io, and more removes manual effort and provides actionable insights for analysts.

Learn how Automation is a force multiplier for TI Ops
Global Fortune 400 Company Harnesses Automation
Learn how ThreatConnect’s automation capabilities reduced the complexity, and operational and financial impact from manual processes.
Buyer’s Guide for Threat Intelligence Operations
A valuable resource for understanding and evaluating threat intelligence platforms (TIPs).
Why Threat Intel is Critical For Supply Chain Security
Stay ahead of attacks against your supply chain partners with high-fidelity threat intelligence.
