Accelerate Threat Hunting
Empower threat hunters with enriched, high-fidelity intel, real time visualizations, and automated workflows. Uncover hidden threats, reduce dwell time, and respond to adversaries with precision.
Intelligence-Led Threat Prioritization
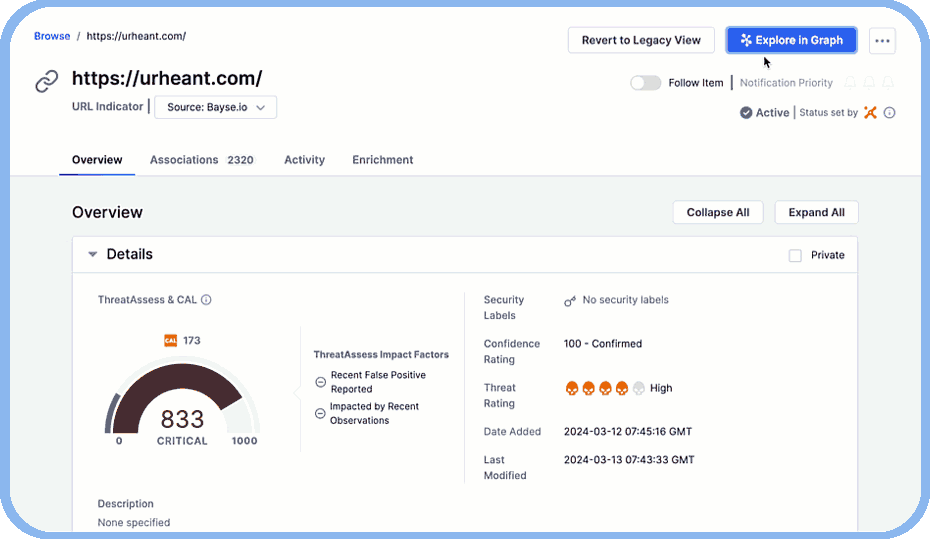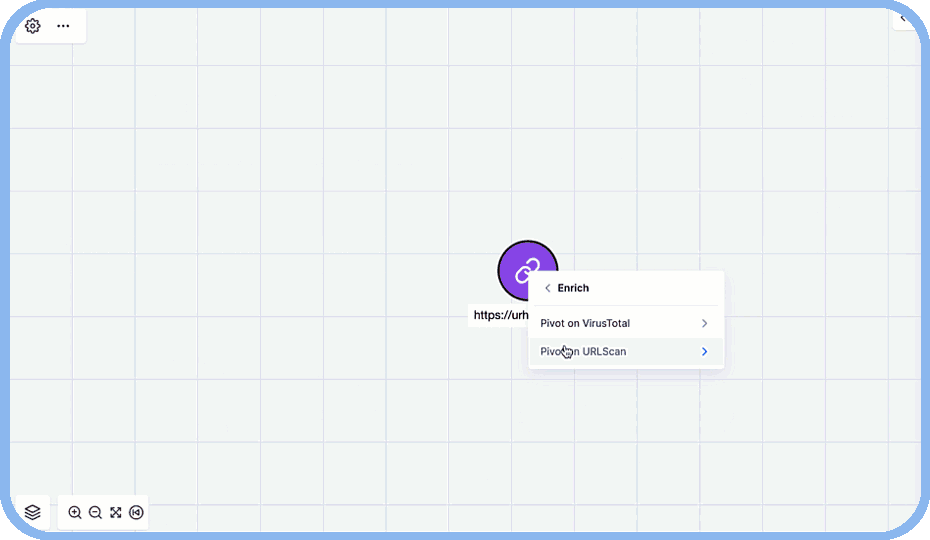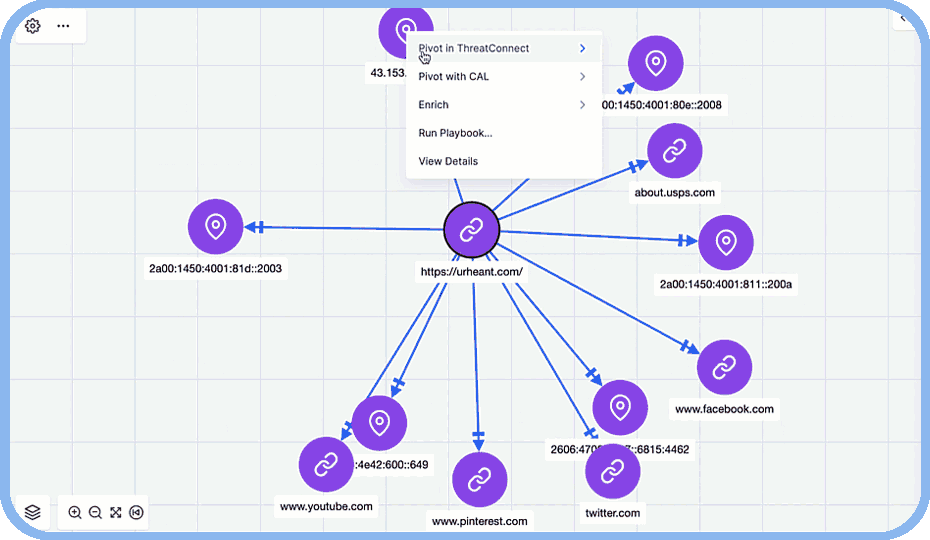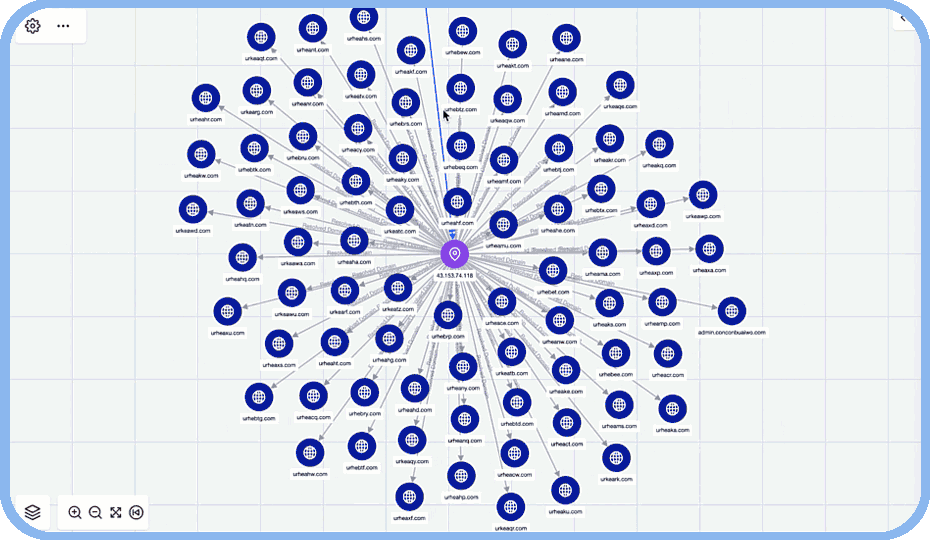
With a centralized source of truth and the context to make decisions, threat hunters can quickly surface hidden connections and prioritize the greatest threats to their organizations.
Key Capabilities:
- Single Source of Threat Intel Truth: Consolidate internal, external, and community-based intelligence into a single authoritative view.
- Connecting the Dots on Attackers: Surface patterns in adversary behaviors to reveal hidden connections between threat actors, tools, and techniques.
- Tactical and Strategic Insights: Align long-term threat actor patterns with immediate operational needs.
Enable Your Threat Hunters with Threat Graph
Take Interactive TourAutomation as a Hunting Force Multiplier
Automation accelerates threat detection and response, ensures consistent triage, and frees analysts to focus on strategic threat hunting.
Key Capabilities:
- Automate Detection and Response: Playbooks automate detection tasks and responses, correlate new intelligence, and activate defense mechanisms.
- Real-Time Threat Scoring: Continuously assess threat indicators and provide dynamic prioritization.
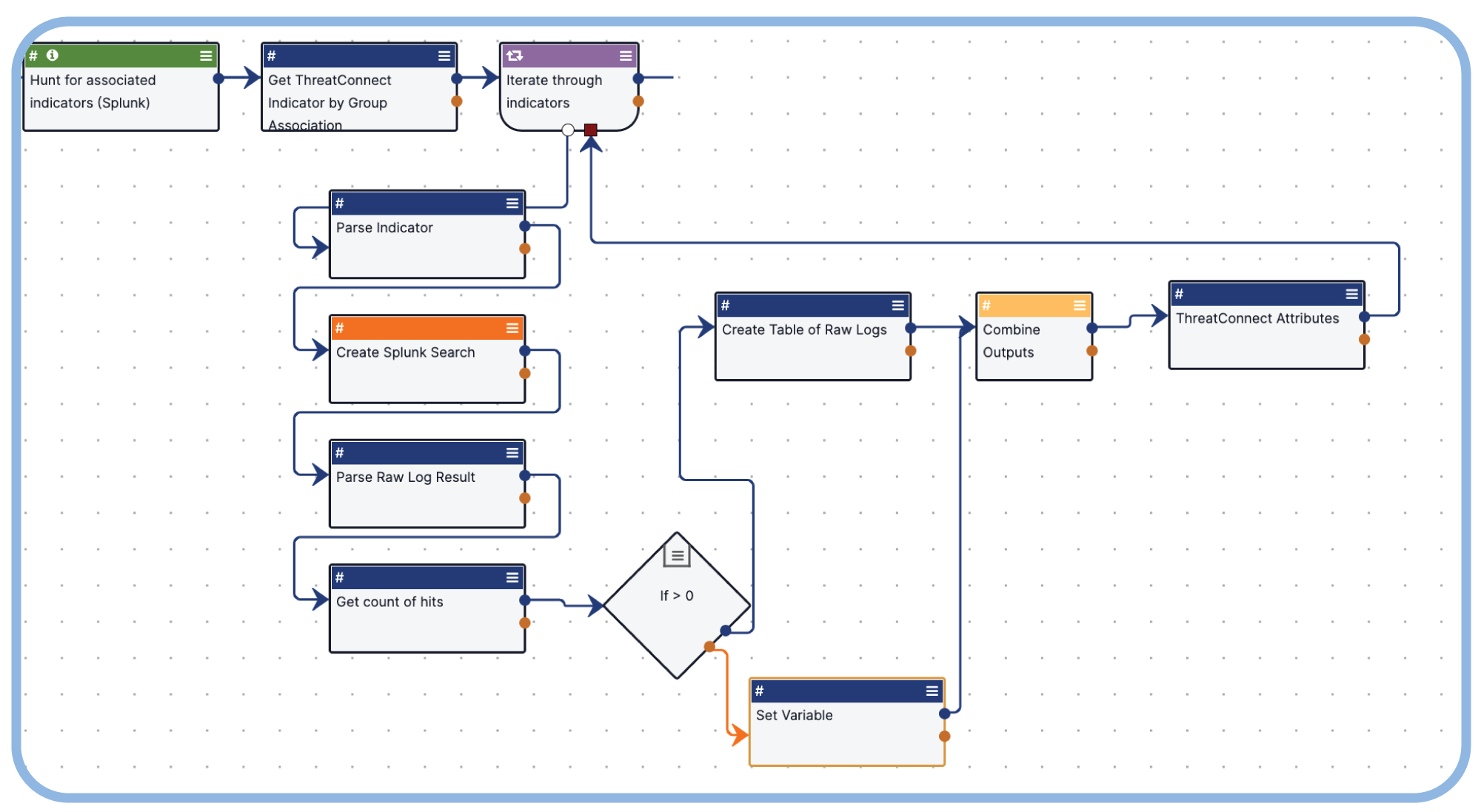
Visualize Threat Actor Behaviors in Real-Time
Accelerate threat hunting with real-time overlays, reducing cognitive overhead, and enable faster, more comprehensive analysis.
Key Capabilities:
- Uncover Connections: Intelligence overlays reveal hidden relationships between attacker infrastructure, exploited vulnerabilities, and critical threat indicators.
- Threat Graph Visualizations: Map out the relationships between attacker techniques and victim networks to see the bigger picture.
- Contextual Intelligence Integration: Access relevant intelligence in whatever tool hunters are working in.
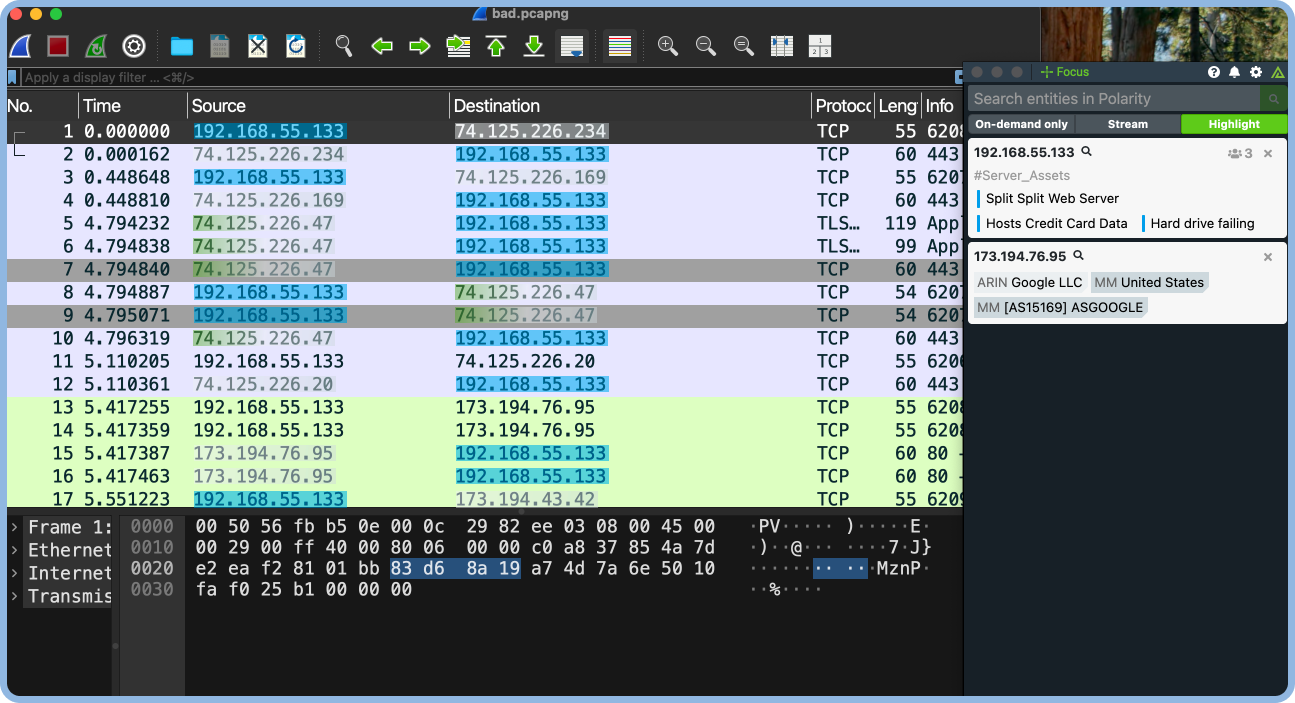
Enhanced Collaboration and Reporting
Enable real-time collaboration, clear reporting, and knowledge sharing to accelerate decision making.
Key Capabilities
- Customizable Reporting: Tailor reports with clear insights for faster action.
- In-Workflow Collaboration: Share annotations and insights in real time.
- Knowledge Transfer: Capture tradecraft to onboard analysts faster.
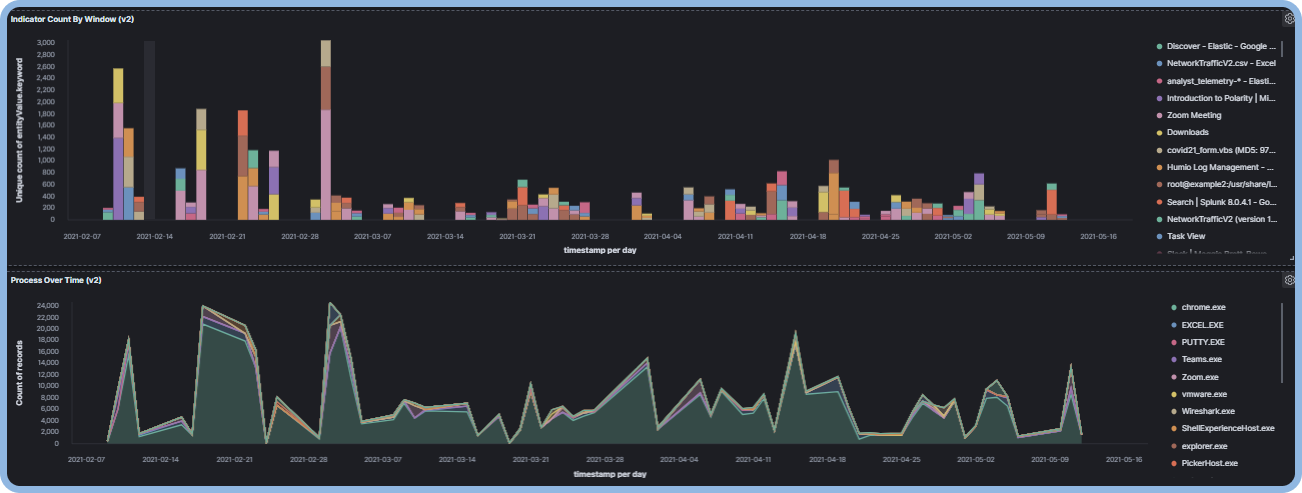
Make Threat Hunting More Productive
Make Hunters More Effective
Tools don’t hunt, analysts do. See how to accelerate hunters’ work.
Operationalizing Threat Hunting Guide
This guide provides a framework for approaching threat hunting in a structured, hypothesis-driven approach.
Get in the Mind of the Attacker
ATT&CK Visualizer makes it easy to see and understand threat actor behaviors.
