In order to evolve a threat intelligence function from a nice-to-have to an essential component of a security team, we need to unpack two key weaknesses of the threat intel lifecycle.
Join us in this on-demand webinar were we explain why TI Ops requires an Evolved Threat Intelligence Lifecycle, one that emphasizes the planning and requirements and the use of threat intel by the consumers to:
- Create a complete view of what threat intel is needed to align and focus on the critical risks to the business
- Support other security operations functions in a collaborative manner
- Identify how TI Ops teams can best deliver intelligence to the right teams, in the right format, at the right time
Click to Show Transcript
00:05
Arpine Babloyan
Thank you everyone for joining us. We are having a few more people joining and we’ll start our presentation in one minute.
01:14
Arpine Babloyan
All right, welcome everyone to our webinar, the need for an Evolved Threat Intel Lifecycle. We are excited to hear from our fantastic speakers today – Dan Cole and Toby Bussa. Just a few reminders before we get started. If you have any questions throughout the webinar, please put them in the Q&A box. We will be answering them during the Q&A session after the main presentation. If we don’t get to your question during the allotted time, we will reach out to you separately after the event. And also this session will be recorded. We will send out the recording so you could share it with your colleagues or watch it back. And thank you again for joining. I will now turn it over to Toby.
02:04
Toby Bussa
Welcome everyone and thanks for joining our webinar today. Today we’re going to be discussing the need for an evolved threat intelligence lifecycle. I’m Toby Bussa, VP of Product Marketing at ThreatConnect, and I’m joined by my colleague and partner in threat intel operations, crime, Dan Cole.
02:19
Dan Cole
Happy to be here.
02:22
Toby Bussa
So we’re going to talk about the Cyber Threat Intel lifecycle during this webinar and the process has been around for decades now. And I for one, being a Six Sigma green belt, love a really good process. It’s just, yeah, you gotta love a good process. And if you’ve done CTI activities or you’ve been on a CTI team, then you’re likely familiar with this lifecycle. You’ve seen it before. However, we’re gonna spend a few minutes going over this because it might have been the first time you’ve seen it. If you haven’t done CTI work, or if you haven’t done CTI work in a while, you may have not seen this. So we’re gonna spend a few minutes going over it. So Dan, over to you.
2:58
Dan Cole
Thanks, Toby. Now, my favorite way to explain any cybersecurity concept is Star Wars. If you’ve seen our write-up on the Battle of Yavin explained using the Diamond Model of Intrusion Analysis, or you’ve read Adam Szostak’s excellent book on what every engineer can learn from Star Wars, you know that Star Wars is really just a series of cybersecurity parables. And so what I’d like to do today is explain the intel cycle and also highlight some of its flaws by looking specifically at the Battle of Hoth from the Empire Strikes Back. So a quick refresher: The Battle of Hoth was an engagement where the Galactic Empire defeated the Rebel Alliance and drove them from their hidden base.
And the reason this works so well is that throughout the Empire Strikes Back, you see the Empire make a series of excellent intelligence-driven decisions, starting with the lead up to this battle. So let’s take a look. Our cybersecurity journey in the Empire Strikes Back starts at the very very beginning. And I love this opening crawl because it paints Darth Vader as a very effective manager. The Rebel Alliance is a specific and highly-relevant threat to the Galactic Empire. And so Darth Vader sets clear, very specific objectives for the team’s intelligence activity. Basically, find the Rebel base, find Luke Skywalker. These are extremely well-aligned priority intelligence requirements. So we are off to a great start.
The next phase of the cycle – collection – kicks off when the Imperial Fleet dispatches a series of probe droids out into the galaxy to go looking for the Rebel Alliance. One of the probe droids actually finds the base, and then prior to being destroyed, it manages to successfully beam its data back to the Imperial Fleet, where it’s presumably decrypted and processed for analysis by a human. As part of that analysis, they discover the Rebel Alliance’s shield generator, they discover the presence of humanoid life forms on a lifeless ice planet. And then finally we get to the final step of the intel cycle – dissemination – where the results of the first four steps are shared with the intent of taking action. Because if we call back to the actual definition of threat intelligence, threat intelligence is knowledge that you can use to take action.
So in the Empire Strikes Back, the Empire uses knowledge of the Rebel Alliance, gained from this probe droid to take action. That action being the actual Battle of Hoth. But it’s in this dissemination step where we start to see things go off the rails. So if we look at the actual dialogue from this scene, what we’re really looking at is a conversation between a threat intel analyst and someone maybe more on the operational side. Could be an IR manager, could be a SONC lead. And what we see is the intel analysts presenting their findings. You know, we found this shield generator, we found humans on this planet, but then the operational lead shoots back, shuts them down. It’s a very siloed, toxic work environment. And it makes sense. You know, the Admiral here, the actual operational lead, has genuine concerns about false positives.
You know, this could be a wild goose chase and he might end up committing thousands of starships, wasting fuel, wasting resources, to something that’s nothing. So that fear of false positives, the silos between teams, really highlights the lack of trust, the lack of confidence that the Admiral, the operational leader, has in this threat intelligence. So we had the team walk through the full cycle. They started with clear PIRs, they had a successful collection effort. The analysis was spot on. But it ends when it comes time to the point of taking action. And if this is all the Empire did, the movie would be over, the Rebel Alliance would have escaped, and that would have been the end of it. But we know that’s not what happened.
8:06
Toby Bussa
So, Dan, it seems like the Empire had a pretty well-functioning threat intel function here. So they viewed it as a must-have function. How did they do that? How did they make that a must-have function?
8:21
Dan Cole
You’re absolutely correct. And we’ll see later on how they’ve ingrained threat intelligence throughout everything they do. And to understand what the Empire did correctly, we need to take a look specifically in depth at some of the limitations of the current cycle in order for us to look at how the Empire leaked beyond that.
So again, if the operational lead, the Admiral, had been successful in shutting down that threat intelligence, the movie would have been over. And that’s because the current TI life cycle has three key issues. The first is a lack of accountability. It very much functions kind of in a threat intel vacuum where the threat intel team could produce and disseminate intelligence, but there’s nothing really holding them accountable to the quality, relevance, or actionability of that intelligence. Now, to be fair, the cycle does have as part of it a sort of umbrella feedback element, but it’s kind of nebulous and it doesn’t really truly call out who that feedback needs to come from and what form it needs to take. And that leads us into the other issue, and that is a lack of stakeholder involvement. Nowhere in this cycle does it explicitly talk about who the intelligence is actually for. It doesn’t talk about the actual consumers of the intelligence who are actually taking it to take action. So you end up with a situation where it’s really sort of siloed and looking specifically at the intel team, not actually their stakeholders. And the stakeholders are really where we get to the third point, which is value realization. So as teams spin through this cycle over and over and over again, is the broader security organization and the broader enterprise actually getting value from the intelligence that they produce? And that’s not just for the sake of the stakeholders, it’s for the intel team also. You know, we all want to feel like we’re doing work that matters, that has an impact.
You know, we’ve seen in surveys that intel analysts, they want to be the heroes here. And by not getting that feedback, by not understanding the value they’re providing, they’re missing out on that key element. And so the end result of not involving stakeholders, of not holding the intel team accountable, of not communicating that value, is that threat intelligence itself begins to be seen at best as a nice to have and at worst, as in the case of the admiral pushing back, as a nuisance.
11:18
Toby Bussa
And Dan, I think one of the things that we’ve seen as well is in the 2022 SANS CTI survey, right, 65% of organizations don’t actually define their requirements. So there is that loop back to the accountability, getting the stakeholders involved. And as you said, ultimately getting that value realization doesn’t seem to happen if you don’t have the requirements in place.
11:41
Dan Cole
Exactly. And even if you have requirements, fundamentally those requirements need to flow from the stakeholders because they’re the ones that you’re accountable for.
12:14
Toby Bussa
Absolutely.
12:18
Dan Cole
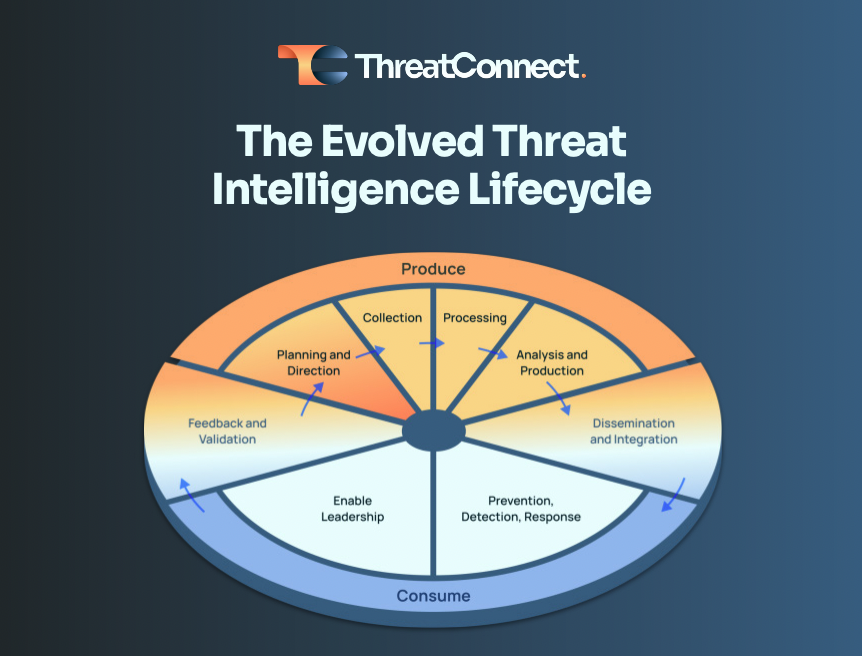
And so we’d like to discuss an evolved intelligence cycle, one that really addresses these issues. And this evolved cycle really has two key differences from the traditional cycle. The first and perhaps most critical one is that it actually brings the stakeholders into the fold, not just as recipients of threat intelligence, but as key participants in its development. So you can see we’ve taken the cycle and we’ve divided it into the two main personas that participate in threat intelligence. At the top, you’ve got your traditional steps, you know, planning, collection, processing, analysis. We call that production. So these are the threat intel teams, the ones actually producing the intelligence.
On the other side, we have the consumers of intelligence, the ones that are taking that intel and actually taking action, whether it’s action for prevention, detection, response, you know, sort of the boots on the ground, tactical operational activities, or whether it’s intelligence that’s more strategic, designed to enable leadership to best make policy decisions, make investment decisions, guide PIRs, that sort of thing. The second thing that we’ve done here, beyond just splitting the cycle in half to bring the consumers in, is we’ve made dissemination and we’ve made feedback bridge steps. So they are the connecting elements between production and consumption, and between consumption and production. And there needs to be formal hand-offs, there needs to be formal quantitative and qualitative feedback elements. And over the next few slides, we’re going to talk a little more in depth about what those are.
So what we saw in the Empire Strikes Back was this sort of siloed, adversarial relationship between the intel producers and the intel consumers. And there is, there’s nothing worse for an intel producer to have their hard work, their hard analysis end up on the floor, on the wastebasket, or you know, cause false positives, cause slowdowns in the SOC. So the key element here with bringing consumers in is the importance of collaboration. So they’re not just passive recipients of threat intelligence. They are active participants in its creation and helping to guide the direction of things like priority intelligence requirements, policy. They need to be part of the process. And it’s not just about telling the intel team what to go do. They also need to be doing things like validating true positives, providing feedback and accountability, saying, hey, this intel report helped me produce a successful alert, or this intel alert to help guide the threat team to uncover a net new threat. So that feedback getting back to the intel team can really only come from the intel consumers.
So if we look specifically at what the consumers are actually doing with intelligence, it really becomes clear why bringing them to the fold is so critical. So on the leadership side, you know, I talked earlier about, threat intelligence is not just there for operational tactical uses. It helps them make effective management decisions. It helps them decide what tools to purchase, what organizations to belong to, what processes to implement. And it’s only by putting that intelligence directly in front of the leaders and getting feedback on it that the process can truly iterate and improve over time. Then if we look at the sort of operational tactical element, you know, the SOC, incident response, threat hunters, red teams, blue teams, you know, they need to be able to take this intelligence, do things like reduce false positives, find more true positives, detect breaches, and on an ongoing basis continue to use tools like automation to weave that threat intelligence directly into their processes where it can benefit them in the moment. And the only way that can happen is if they are working closely with the intel producer team to help define things like relevance, recognize true positives, identify issues like false positives, so the intel team can take that feedback and continue to iterate on their approach.
And that brings us to sort of the next element and that’s the importance of incorporating feedback. It’s not just a cycle where the intel team, you know, sits in a room producing intel and churning it out. They need to be taking in that feedback from the operational teams. You know, if we think about intelligence as knowledge that can be used to take action, was the intelligence used to actually take action? Did that action have a positive effect on the defensive posture of those consumer teams? This is also an opportunity for the consumer teams to bring net new insights to the production team. We had a customer once tell us that their SOC team was their most valuable intel feed because getting that live data from boots on the ground directly back to an intel team is critical to helping them make hyper relevant decisions. And when we talk about TIOps, a big element of that is how can we bring some of that real time data from the intel consumer team to bear to make the intelligence better, more relevant in the long term?
So what does this look like in action? Well, it’s a mix of quantitative and qualitative insights. And of course some of these, especially quantitative insights, might be challenging to measure at first, but over time, by starting small, you can truly grow and develop a solid feedback and validation program for your intel team. So this could mean things like looking at false positive ratio. It could mean things like looking at detection efficacy. You know, what is my rate of false positives to true positives? It could mean looking at a specific piece of intelligence and identifying what actions were taken based on this or conversely, what actions were not taken and sending that back to the intel team. It’s also about the production team sitting down with their stakeholders to learn what are their top concerns, how good is the intel, how relevant is it? And at the really expansive, highly impactful set of the spectrum, you’ve got things like cyber risk quantification. So did this intelligence help you proactively block an attack that would have exposed your organization to a particular dollar value of cyber risk? And again, this doesn’t just help improve the value of the threat intelligence overall, it also helps the intel producers themselves understand and feel like they are making a much stronger impact.
19:55
Toby Bussa
Yeah, I was going to say, Dan, I think this is one of those areas where now we finally, using the bridge metaphor, we’ve made that connection from: How do you make this go from a must from sorry, nice to have to a must have function in the security operations team.
20:05
Dan Cole
Exactly. And that element of making TI essential is really what we want to look at. And what I’d like to do now is go back to the Empire Strikes Back and show what this evolved intel cycle looks like in action. Because it’s by applying this cycle that the Empire manages to consistently and repeatedly throughout that film, manage the threats that they face.
What does it look like in action? So instead of the movie ending, because you had siloed teams, you’ve got Darth Vader, who’s a key intel consumer. You can think of him as the CISO or, you know, the director of the SOC. He’s the one who was initially involved in defining the PIRs, and so he gets directly involved in understanding and validating what’s going on here.
So as the leader, as the CISO, as a powerful Sith Lord with access to the Force, he’s got the big picture and he can take the intelligence that was produced and use it to make effective decisions. But he immediately recognizes that the intelligence actually shows the Rebels base. He gets his team working together, he smashes silos and shuts down the Admiral’s power play. Not only that, but he brings leaders from other departments into the fold to take action. So it’s not just the Navy, he brings in the Army, he gets everybody working together based on his high level view of the intelligence. We also see the intelligence brought to bear on the actual response, the actual attack on Hoth. So based on the intelligence that the probe droid collected, action is taken. The fleet is deployed to Hoth for the attack. They prepare for a ground assault, and ultimately they are victorious in the battle. But one important thing to recognize with the intel cycle, including the evolved intel cycle, is it’s not one and done. It is a continuous loop that ultimately produces, over time, better intelligence and gets the defender closer to victory over the adversary. So we see this happen throughout the film. So as the fleet closes in on Hoth, they receive new intelligence that the rebels have put up a shield. So they pivot their attack, they pivot their response, they change their tactics to a ground assault based on that new intelligence. And they could only have done that if the consumers were actively involved in the process. As the battle is won and Luke Skywalker and the Millennium Falcon escape, they readjust the priority intelligence requirements.
So it’s not just about looking for Luke Skywalker, it’s about looking for the Millennium Falcon in order for them to create a trap later on. And that could only happen if the Imperial Fleet received intelligence about where these people were and adjusted the response accordingly. Next, when they struggle to find the Millennium Falcon, so they’re missing some intelligence. So something is missing from the collection effort. They bring in a third party threat hunting team in the form of various bounty hunters. So again, the consumers are constantly responding to intelligence. And finally, at the end, the entire security organization sets up what is essentially a honey pot to lure Luke Skywalker to Cloud City. Although maybe we could consider that ransomware.
So that could only happen if you had a truly collaborative setup between the intel consumers and the intel producers, where the consumers were constantly and consistently providing clear feedback to the intel team so they could adjust. And I can’t stress enough how much all of the wins that the Empire had throughout the film was because of that constant feedback cycle. So, for example, here we see Darth Vader again being a good, effective manager. So he had someone on his team who was still putting up silos, still being resistant to taking on this evolved intel cycle approach. And what does he do? He essentially fires him. Not only that, but as a good manager, he promotes from within. He rewards productivity and competence and he is,
he creates what is essentially a fusion center by taking his former threat intel lead and putting him in charge of the entire operation. So this is someone who has demonstrated that he’s able to close the loop between the intel consumers and the intel producers. And thanks to Darth Vader’s excellent leadership and the Empire’s adoption of the evolved intel cycle, the Empire ultimately achieves victory by the end of the film.
25:15
Toby Bussa
Thanks, Dan. I think that’s a very apt parable that you provided there. So we do have some additional resources if you’d like to read more about threat intelligence operations and the evolved threat intel lifecycle. And we have a couple of blog posts and white papers where we dissected The Diamond Model and applied it to the storage battle of Yavin, as Dan showed, and then also a really great YouTube video discussing how metrics can help threat intel. And so with that, we’ll stay around for some questions if you have them. And we want to thank you for your time and we’ll take questions now.
26:04
Arpine Babloyan
Awesome. Thank you so much, Toby and Dan. This was great. We did get quite a few questions, so I’m going to start and right into it. So the first question we got from Sharif, how to fit intel lifecycle into maturing security operations?
26:17
Tony Bussa
Yeah, I’ll take this one. Arpine. So it’s a great question. We actually call that intel-powered security operations because we believe that one of the acts that you can follow in order to mature security ops is to put threat intelligence operations at the core of your security operations functions. And so it actually becomes, you know, you could call it like a cornerstone or keystone type of capability inside the team. And what it does is removes a lot of the potential silos that may exist. If there is a TI team or, you know, if you are building a net new function or you’re trying to mature your security operations function and you don’t have a TIOps function, it gives you a great starting point of saying, look, we’re just going to put it front and center because that intelligence that the TIOps team or the CTI team is getting does need to be pervasive across the other security operations functions. Or if the TIOps function is primarily supporting your security operations center, for example, then by elevating it up out of the SoC, you position it to actually be the producer to not just one consumer, but to multiple consumers across the security operations, sorry, security operations function. So it now supports threat detection and response in the SoC. It can support your vulnerability management program, it can support other places in that security operations function. So that’s really, you know, what we believe the goal is. Put it front and center in your security operations team and that makes it again, more applicable to a wider set of consumers.
28:13
Arpine Babloyan
Awesome. Thank you. All right, next question is how do we loop through the lifecycle as more context about intelligence unfolds? For example, from announcement of a vulnerability to exploitation to commodification.
28:28
Dan Cole
I’ll take that one again, Another really great question. And you know, that sort of situation where you have new context coming in is hopefully happening fairly regularly. A lot of intelligence really does have a shelf life. So it’s important to kind of stay on top of that. And we actually see a lot of that looping, that iteration happening in the film. As the Empire learns that the shields are up, they deploy ground forces, as they learn that Luke Skywalker has escaped, they change their approach. And so a vulnerability is a really good example because whether that vulnerability is actively being exploited out in the wild, whether it’s fully commodified, that’s going to really change your approach to how you address that vulnerability. And we talk about intel consumers, certainly the vulnerability management team, it is a big stakeholder in that consumer bucket.
So just like we talk about you know, looping in the SoC, looping in the incident response team. You know, it’s critical to make sure that the vulnerability management team is also getting the types of intelligence that they need. And in terms of the iteration piece, you know, we’re already talking about one loop, you know, the intel cycle, the evolved intel cycle. Then fundamentally you can boil every loop like that down to the OODA loop. For those not familiar, OODA – observe, orient, detect, act comes originally from, I believe, naval aviators. And it’s really just a method for taking in active new intelligence and regularly pivoting. So you can imagine bringing in lots of little mini OODA loops into the broader intel cycle so that you can constantly keep up with that new context as it comes in. But fundamentally, it really boils down to just getting in those stakeholders, getting those consumers involved in the process so they’re reporting back that context in real time.
30:47
Arpine Babloyan
Awesome. Thank you. Thank you, Dan. All right, next question or more of a question from Kevin. This concept for this webinar is great. I love connecting threat intel into the plot of Star Wars. Will the slides be made available after the webinar? So thank you, Kevin. This is music to our ears. We’re all big fans of Star Wars here at ThreatConnect. And yes, the slides will be made available. We’ll be sending the recording of the presentation and the slides along shortly after this webinar concludes. All right, next question or more of a challenge from Christopher. This seems like a model for improving communication between intel teams and their stakeholders. Do we really need to call this a new threat intel model? Don’t you think this will just confuse people in the long run?
31:40
Toby Bussa
Yeah, I’ll take that one. Arpine. So I think we just want to be clear, right? We love the threat intel lifecycle, full stop. I think it’s just as we’ve observed it over many years. We just believe it’s not as prescriptive as it could be and should be. And that’s why we believe it actually needs this evolution, because it needs more focus and needs to be more obvious that there are actually two parties to really be successful, to really bring value to threat intelligence. And that is acknowledging the producer, which it does very well right now, but it doesn’t acknowledge the consumer as well. And really we believe that that’s the big function that needs to be highlighted in again, not a new cycle. You know, it is an evolution of the current one.
32:34
Arpine Babloyan
All right, awesome. Thank you, Toby. Another one from Christopher. What are your suggestions on how to involve your stakeholders? How do you go about soliciting consistent and clear feedback for your CTI team?
32:50
Dan Cole
Another great question from Christopher. So how do you get stakeholders more involved? Well, it really starts with understanding why aren’t they involved in the first place. Trying to think, what is that quote from Tolstoy? Happy families are all alike, but unhappy families are unhappy in their own way. Looks kind of like security teams where, you know, each security team is going to have different challenges and different reasons for why that involvement is not happening. You know, we speak with teams where sometimes it is simply cultural, you know, where your teams are relatively siloed. Other areas we see it’s technology where, you know, there is a desire to involve stakeholders, but maybe the technology is not there. And that lack of involvement, you know, goes back to really the key problem that we see with the traditional intel cycle is that it does not make those consumers an active participant. So in terms of actually getting that consistent and clear feedback, you know, multiple approaches, you know, step one is really just getting those consumers to actually care about threat intel, you know, being able to answer that question, what’s in it for me? And that really starts with the planning phase with things like PIRs. So, you know, are those stakeholders being involved in PIR development? Are they being shown through those PIRs that what the intel team is doing are actually things that they care about? And over time that’s going to start building up trust as they start to see things like reductions in false positives, increase in relevancy.
And then the second piece is technological. When we talk about involvement and feedback, you know, sometimes that feedback can be qualitative, you know, like I mentioned with the PIRs, but it can also be quantitative. So you can think about something like detection efficacy, you know, if you have your incident response team using a tool like ServiceNow, for example, you know, they might not be talking directly to the intel team, but through an integration into ServiceNow, the IR team can be exposed to intelligence. And their feedback can take the form of something like a bi-directional integration where in ServiceNow they are reporting whether something was a true positive or whether something was a false positive. And that can become sort of quantitative feedback that feeds back to the threat intelligence team.
And then, you know, the financial team can take that quantitative feedback and adopt their processes. And over time that will build up the trust and confidence that the consumers have in the producers. And over time that will help build up a lot of that confidence and actively make the consumers want to be involved.
36:08
Toby Bussa
Yeah, I’ll say one other piece too, and kind of going more towards the requirements piece and getting involved, the stakeholders involved early there. We actually covered this in a webinar, previous webinar, and the recommendation was to not go to your stakeholders and say, “we have threat intelligence. What would you like?” But instead to be more proactive and try to anticipate, you know, how the threat intelligence could help their function and then go to them with a proposal that says, this is what we think we can do for you, and get their feedback on that proposal and iterate from there, because they’re probably not going to have a good idea about, you know, okay, well, thanks, but I don’t know where to start. I don’t know how to answer that question. So by inverting that approach and taking a proposal to them, you’re putting them in a position for them to digest that, but then agree or disagree or at least iterate on, you know, on what their actual requirements are and then you could go off and make that happen.
37:12
Arpine Babloyan
Awesome. Thank you, Toby and Dan. Joel is asking about where can we find the blog post? So I can cover that. We will be sending all of the links to the resources that Toby and Dan mentioned after the webinar with the presentation slides and all the links. Also, it will be posted on our website on threatconnect.com under discover section is where we have all the blogs. So we’ll send it out, but in the meantime, too, you can check that out there. All right, next question is from Arnaud. Is it possible to perform CRQ, cyber risk quantification, with the FAIR Model without CTI?
38:01
Dan Cole
So I love that question for a few reasons. If people on the call are not familiar, the FAIR Model, Factor Analysis of Information Risk, is a fairly standardized, no pun intended, a fairly standardized model for quantifying cyber risk. It looks at things like the frequency of loss events taking place, the impact of the loss events, and in terms of whether it’s possible to do that CRQ without CTI, I want to give a cheeky answer and be like, you could, but, you know, fundamentally the FAIR model includes things like threat capability, things like the knowledge and materials possessed by an adversary. So those are all factors that can come in through things like the diamond model, for example. And fundamentally those, you know, threat capability elements do come from CTI.
But part of the reason I really like this question is that, you know, when you look at the evolved intel cycle, you know, one of the key bridge step is that feedback and validation, you know, and we talked earlier in the webinar about how that feedback and validation can take the form of, you know, qualitative insights. Like, you know, this report was helpful or not, quantitative insights, when I talked about, you know, validating things like true positives, tracking whether actions were taken. But one of the most valuable pieces of feedback and validation is cyber risk. You know, did a specific piece of intelligence help reduce a company’s risk profile, risk exposure by a certain amount? You know, we can think of it as, you know, at the very top of the business, they care about things like revenue, profit, that sort of thing. And so risk is really a great way to translate what the intel team is doing into that sort of fiscal language that the business cares about. So, yeah, really great question.
40:25
Arpine Babloyan
Awesome. Thank you, Dan. All right, next question we have is, which stage of the threat intel lifecycle do you see most customers are having issues with.
40:38
Dan Cole
Having issues with? So there’s a fine point to that, and there’s actually a way that we look at this. We did a survey specifically on the intel cycle to sort of help us build this out. And one of the things that we looked at was where were analysts spending the most time in the cycle? And the bulk of time was spent in things like collection and processing. And one of the challenges that we saw in the survey is that a lot of time is being spent on collection and processing. But nobody was really having much fun with collection and processing. So where people actually wanted to spend most of their time was on analysis. Like, that was the clear winner. They’re called intel analysts, not intel collectors or intel processors.
And we found that the analysts really wanted to spend time on analysis so they could really be a hero, so they could really feel like they were making an impact. And it’s hard to feel like you’re making an impact when you are cutting and pasting intel into a spreadsheet or using Python to write data transforms. So, you know, it’s not so much that collection and processing where things necessarily went off the rails. It’s more than, it was just a very tedious part of the cycle. And so that’s where, you know, when you think about a product like ThreatConnect, you know, and our Threat Intel Ops Platform, you know, a big part of what we try to do is really help automate and speed through the collection and processing steps so that the analysts can get to the analysis step.
42:48
Arpine Babloyan
Awesome. We actually had a question about where, what stage do intel analysts specifically spend most of their time? So you kind of answered both, awesome with that one. All right, we have time for a few more questions, so if we don’t get to yours, we’ll reach out to you separately. But there is the next slide I’m going to read from Joel. When you consider the intel cycle and the component of analysis, is the collection and processing only limited to what is directly fed to you, or do you need to expand your research to include external items like patch information from vendors, risk bulletins from organizations like CISA, et cetera?
43:33
Dan Cole
So that really comes back to, like in all things threat intelligence, the short answer is, “it depends.” But fundamentally that goes back to the beginning of the cycle with planning. So we started with, you know, in the Empire Strikes Back example with Darth Vader setting very clear intelligence requirements. You know, find the rebel base, find Luke Skywalker. And the collection effort the Empire did, sending out probe droids, was really tightly aligned to those PIRs. So as part of planning and collection, you know, we talk a lot about PIRs, but emerging from PIRs., you also have this notion of collection requirements. So, you know, based on your specific, you know, maybe one of your PIRs is, you know, if you’re a financial organization, you know, defend against attacks to our payment processing systems. And so based on that PIR, you might then set collection requirements for, you know, collect data for, you know, get feed data, get vulnerability data, get malware data that might apply to things like attacks against a payment processing system. So I’d say, you know, the answer to your question is yes, assuming that your PIRs, from your PIRs, you emerge those collection requirements, and based on those collection requirements, that’s going to inform the external items that you get. But that also ties into the feedback portion, where in addition to getting feedback from your stakeholders, from the intel consumers, you also need to be looking at evaluating those collection requirements. So if I spend all this work to go out to CISA, spend all this work to collect patch information, is that data actually being useful?
And the same thing would apply to something like an intel feed. So if you’re bringing in an intel feed, is your team actually producing data from it? That’s sort of an output measurement. But more importantly, is that feed data actually producing intel that leads your consumers, your stakeholders, to take action, or is it just, you know, being sent off into the wind? So really it depends on collection requirements and consistent evaluation of those collection requirements.
46:09
Arpine Babloyan
Thank you so much, Dan. This is great. And thank you everyone for your questions. We got a couple of thank yous to our presenters and compliments on the content, which is great. Thank you for mentioning that. That means a lot to us. And I think this is all of our questions that we have so far. So I wanted to thank everybody again for joining us. Thank you to Dan and Toby for your amazing content. As a reminder, we will be sending the recording and all of the slides after this webinar and hope to catch you on the next one. Thank you so much, everybody.
46:51
Dan Cole
Thanks for having us.