No Results Match Your Search
Please try again or contact marketing@threatconnect.com for more information on our resources.

Customer Story: How a Top Canadian Bank Revolutionized Cybersecurity with AI-Driven ThreatConnect
Learn how automation and AI transformed cybersecurity for a Canadian financial institution, saving time and improving threat detection by up to 99%.

Beyond the Buzzword: Real World Applications for AI in Cyber Threat Intel Webinar
AI and Threat Intelligence: Unlocking Potential, Navigating Risks In this recorded panel, our experts cut through the AI hype and reveal its real impact on cyber threat intelligence. AI is often marketed as a magic bullet, but many solutions fail to deliver meaningful value. Security teams face mounting pressure to process vast amounts of threat […]

Customer Story: Global Credit Union Reduces Alert Fatigue to Detect and Respond to Threats Faster
Combat alert fatigue with ThreatConnect. Discover how a credit union saved $1M annually and achieved 99% faster threat detection with advanced automation and threat intelligence.

How ThreatConnect Leverages AI
Discover how ThreatConnect uses AI to enhance cybersecurity, reduce risks, and improve decision-making. Learn how to integrate AI into your security operations.

Leveraging AI Integrations To Enhance Organizational Effectiveness
Streamline data analysis and decision-making with Polarity. Access diverse data sets, LLMs, and AI platforms through an intuitive, no-code interface. Transform your workflows today!

Polarity Enterprise by ThreatConnect
Enhance your security operations with the Polarity Enterprise. Discover our solution for federated search, real-time contextual intelligence, and seamless integrations.
Demo of Polarity Federated Search and Analysis Tool
Watch demo of Polarity, federated search and analysis tool, led by Joe Rivela, SVP, Customer Success and Co-Founder of Polarity.io: Click here to show transcript Joe Rivela: My name’s Joe. I’m SVP here responsible for customer success, but also heavily involved on the Polarity initiatives that we help to support and fulfill for our customers. […]

Sandboxing-Powered Threat Intelligence: Defending Against Stealer Malware
Integrating ThreatConnect’s Threat Intelligence Platform with VMRay enhances security by providing detailed insights into malware and threat actors. This combination streamlines workflows, helping SOC analysts prioritize alerts and improve defenses like SIEM, XDR, EDR, and NDR. Join our on-demand webinar, hosted by ThreatConnect and VMRay, to: Explore an in-depth analysis of Redline and Lumma infostealers […]

Operationalizing Threat Hunting: A Comprehensive Guide
This guide provides a clear framework for building or enhancing a structured, hypothesis-driven approach to threat hunting.

The Emerging Threat Playbook: Operationalizing Exploit Intelligence
Security analysts encounter significant challenges in managing threat intelligence and conducting vulnerability assessments, particularly as attackers swiftly exploit weaknesses. Watch our on-demand webinar hosted by ThreatConnect and VulnCheck where we offer valuable insights into strengthening cybersecurity strategies. Attend the webinar to learn about: Prioritizing high-risk vulnerabilities instantly with evidence of exploitation. Automating monitoring and getting […]
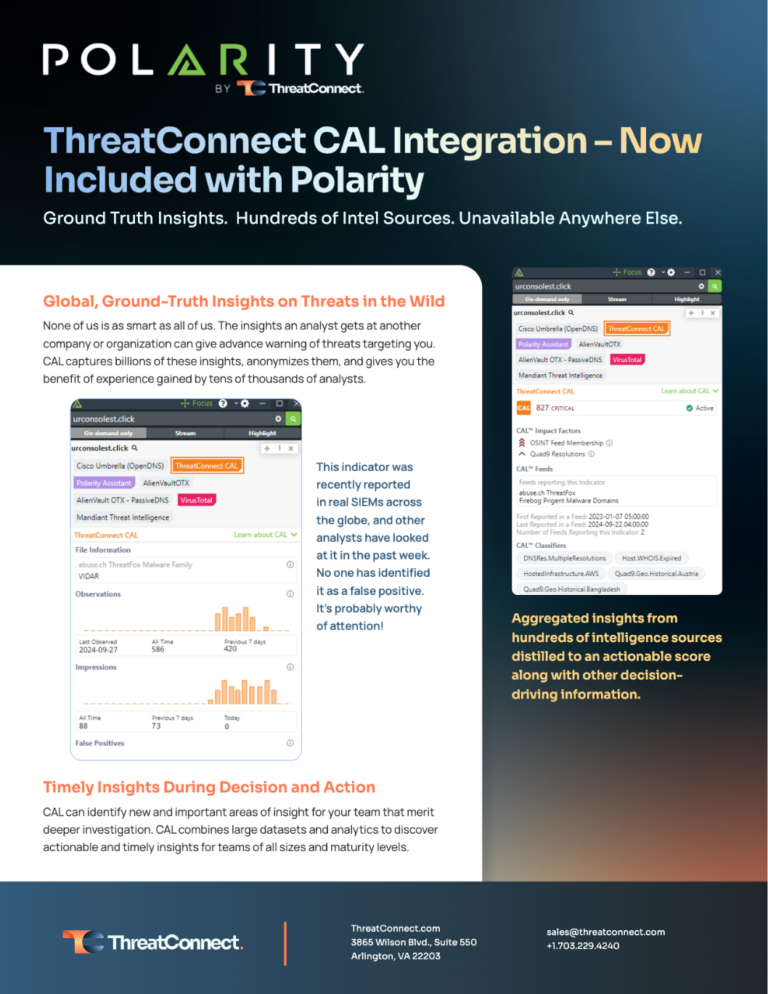
ThreatConnect CAL™ Integration with Polarity
CAL combines large datasets and analytics to discover actionable and timely insights for teams of all sizes and maturity levels.

Discover How Genuine Parts Company Transformed Their Cyber Risk Strategy
Explore how GPC optimized their cybersecurity strategy using ThreatConnect’s Risk Quantifier, transitioning to data-driven analyses for better risk management and investment decisions.


