No Results Match Your Search
Please try again or contact marketing@threatconnect.com for more information on our resources.
Turn Historical Threat Data into Actionable Intelligence Using Analytics
Learn how threat data becomes intelligence, how to structure historical threat data for tactical planning, and more.

A ThreatConnect Success Story: Upgrading from an Open Source TI Database
Find out how ThreatConnect helped a customer meet these objectives: Transfer all existing data from the open source database to ThreatConnect. Maintain all original creation dates, since the customer relied upon the dates for reporting, metrics, and memorialization. Ensure the transition from a dev environment to production was seamless.
Webinar: “How to Prioritize and Protect Against Relevant Threats: Context is Key”
Joint webinar featuring ThreatConnect and FireEye iSight Intelligence: How to Prioritize and Protect Against Relevant Threats: Context is Key.
[Webinar] Guccifer 2.0, the DNC Hack, and Fancy Bears, Oh My!
Follow Toni Gidwani, Director of Research Operations at ThreatConnect, in this webinar recording as she shares the intelligence used by the ThreatConnect Research team to search for answers surrounding the Guccifer 2.0 persona and tie the recent DNC Leak back to Russia.

A Fresh Look at Security Analytics
Did you know data can be viewed in three categories: “regular data, big data, and “too-big-for-you” data? In this white paper, ThreatConnect’s Director of Analytics discusses how security analytics is commonly used today, automation, and the impact of orchestration on efficiency and scale.

A ThreatConnect Success Story: Focusing on Relevant Intelligence
Learn how ThreatConnect solved these problems for a customer: Finding and using relevant intelligence Measuring risk based on current known vulnerabilities Using threat intelligence for detection

A ThreatConnect Success Story: Automating Analytical Processes
Learn how ThreatConnect solved these problems for a customer: Ingesting ISAC data and maintaining visibility in SIEM Making Threat Intelligence Actionable Automating analytical processes, correlating current attacks and past incidents
How to Prioritize and Protect Against Relevant Threats: Context is the Key
Joint webinar featuring ThreatConnect and FireEye iSight Intelligence: “How to Prioritize and Protect Against Relevant Threats: Context is Key”. The webinar covers how to prioritize your team’s response and put your intelligence to use.
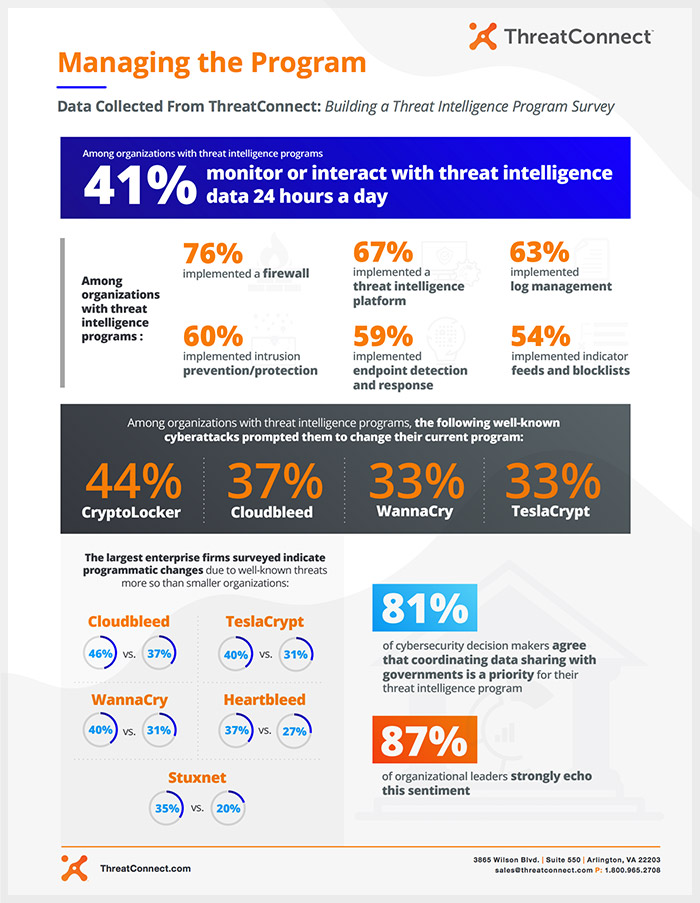
Building a Threat Intelligence Program – Managing the Program
The 2018 Building a Threat Intelligence Program Survey focuses on how organizations are leveraging threat intelligence to combat increasing cyber threats. Among organizations with threat intelligence programs, 41% monitor and interact with threat intelligence data 24 hours a day.
Guccifer 2.0, the DNC Hack, and Fancy Bears, Oh My!
Follow Toni Gidwani, Director of Research Operations at ThreatConnect, in this webinar recording as she shares the intelligence used by the ThreatConnect Research team to search for answers surrounding the Guccifer 2.0 persona and tie the recent DNC Leak back to Russia.

Building a Threat Intelligence Program
ThreatConnect surveyed over 350 cybersecurity players in the United States to understand how their organization uses threat intelligence to aggregate and monitor cybersecurity data in one place. Download the Report: Building a Threat Intelligence Program to review research findings that include how organizations who have fully-mature threat intelligence programs have prevented: phishing attacks (72%) ransomware […]
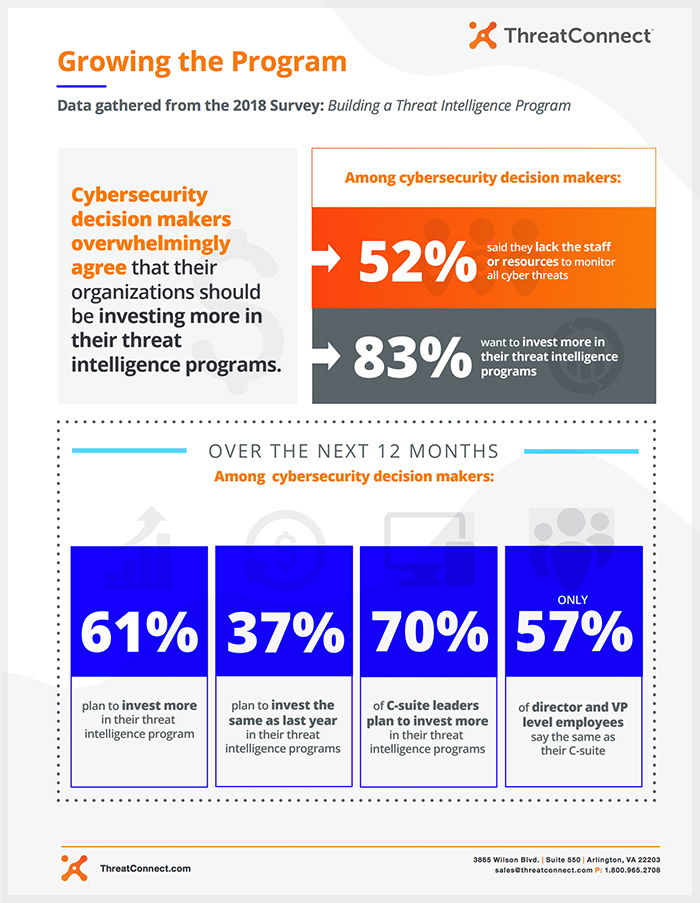
Building a Threat Intelligence Program – Growing the Program
The 2018 Building a Threat Intelligence Program Survey focuses on how organizations are leveraging threat intelligence to combat increasing cyber threats. Among cybersecurity decision makers, 52% said they lack the staff or resources to monitor all cyber threats.



