No Results Match Your Search
Please try again or contact marketing@threatconnect.com for more information on our resources.

ThreatConnect Training, Workshops, and Services Catalog
Within this catalog, find a complete listing of ThreatConnect administered training, workshops, and service offerings. Constantly expanding, these offerings focus on kickstarting your experience with ThreatConnect to decrease your time to value, and ultimately help you master the ThreatConnect Platform.

Rating Threat Intelligence: Skulls Scale for Cyber Threats
In order for threat intelligence sharing and community collaboration to work, we all need to be speaking the same language. We, the analysts at the front lines, need a standard vocabulary and a standardized rating system so that we are all evaluating threats in the same manner.

A ThreatConnect Success Story: Using Automation to Collaborate with Partners
Learn how ThreatConnect solved these problems for a customer: Improved focus on alerts within the organization Significant workload reduction through automated enrichment Consistent communication of threat and incident information internally and externally
Using Visualization to Make Threat Intelligence Actionable
Follow along with Dan Cole, Director of Product Management, and Drew Gidwani, Director of Analytics, as they discuss how to use visualization to make threat intelligence actionable. Tune into this webinar to learn the best practices for using dashboards and tracking security metrics, how to apply analytics in dashboards, and how to build a dashboard […]
Playbook Fridays: QRadar Tag Search
Ground truth is one of the most important sources informing threat intelligence. A key source of this truth is what’s happening in the SIEM- QRadar in this case. Knowing this, we needed a way to correlate data in QRadar with intelligence in the form of Indicators in ThreatConnect. This Playbook was created to provide a […]
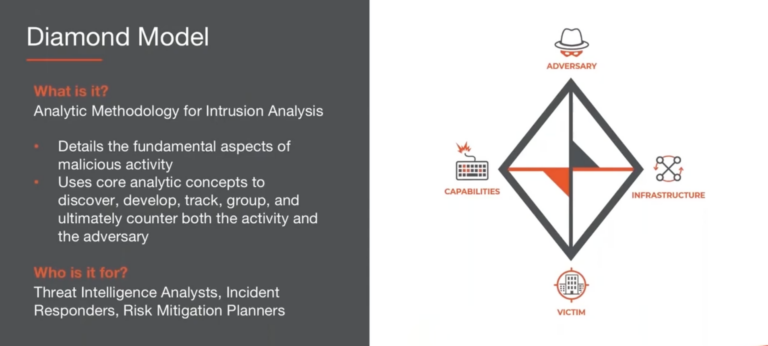
The Diamond Model: An Analyst’s Best Friend
During this video, 2 of the 3 co-authors of the Diamond Model for Intrusion Analysis, Sergio Caltagirone from Dragos and Andy Pendergast from ThreatConnect, talk about how to properly utilize the Diamond Model for Intrusion Analysis to triage incidents and categorize threat activity. ThreatConnect is the only threat intelligence platform built on the Diamond Model […]

Four Things You Might Not Be Doing in ThreatConnect, But Should Be
Watch this webinar to learn about the top four things that we don’t always see customers doing, but that we think could be super helpful. They are also the four things that we get the most questions about from customers. You’ll learn about: Operationalizing and optimizing ThreatAssess/CAL in your environment. Tags and Attributes – when […]
Identify, Manage, and Block Threats Faster: Webinar with ESG Lab
ESG Lab evaluated the ThreatConnect threat intelligence, analytics, and orchestration platform, TC Complete, and two components of the platform, TC Analyze and TC Identify. Their goal was to validate how the ThreatConnect platform enables organizations to identify, manage, and block threats with end-to-end detection capabilities and advanced analytics. View the webinar to hear ESG Senior […]
Collecting and Analyzing Intelligence About Potential Threats
Hear ThreatConnect’s Senior Threat Intelligence Researcher, Alex Valdivia, speak on a panel of experts on how to uncover the motivation and mitigation methods for threat actors targeting your organization.
ThreatConnect’s Revamped Search Functionality
Find what you’re looking for quickly; even if you don’t find what you’re looking for, our new Search will point you in the right direction. Indicators, Groups, and Tags now all feature a “Graph View” that lets you visualize relationships in the data and uncover important associations.
Playbooks ROI Calculator – How to Save Time and Money
Overview of our Playbooks ROI calculator, and how to display ROI in terms of time and money saved.
Exploiting the Adversary How to the Proactive with Threat Intelligence
Understanding your adversary is essential to effective cybersecurity. In order to block threat actors, now and in the future, you must know where they have been before, what their techniques, tactics, and procedures are, and if they are targeting your specific organization. By gaining a deep understanding of your adversary, you can take steps to […]



