No Results Match Your Search
Please try again or contact marketing@threatconnect.com for more information on our resources.

ThreatConnect and Zscaler Internet Access (ZIA)
ThreatConnect® and Zscaler® have partnered to enable joint users to automate their incident response and proactively protect their network from today’s sophisticated attacks.
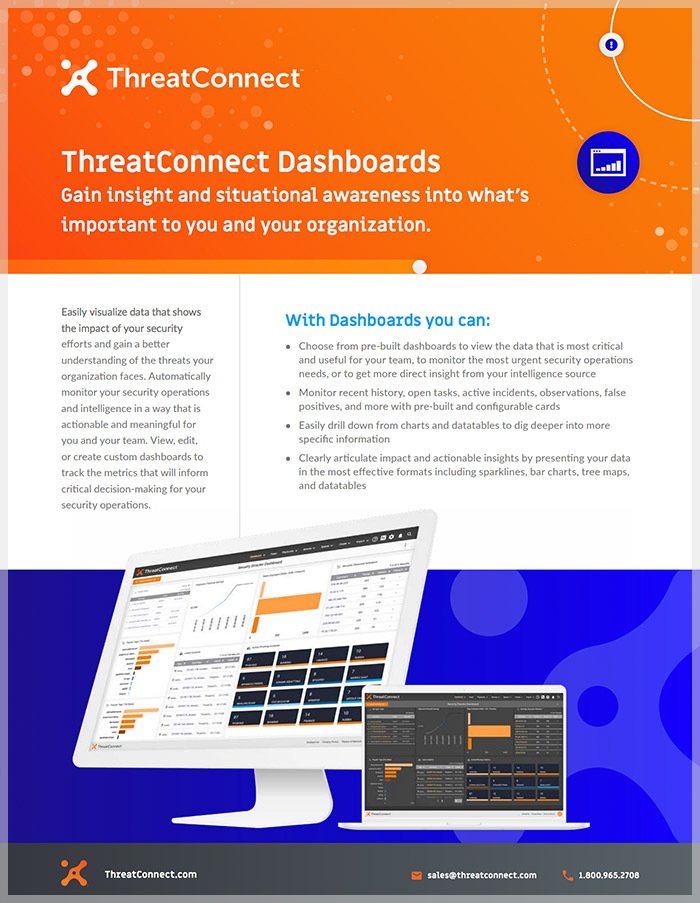
ThreatConnect Dashboards
ThreatConnect Dashboards allows you to easily visualize data that shows the impact of your security efforts and gain a better understanding of the threats your organization faces. Automatically monitor your security operations and intelligence in a way that is actionable and meaningful for you and your team.

ThreatConnect and Flashpoint
The ThreatConnect TI Ops Platform was designed to help users understand adversaries, automate workflows, and mitigate threats faster using threat intelligence. Flashpoint combines automation and human-driven data collection to delve into the internet’s most difficult-to-reach online spaces, providing a level of access that no other provider can. Access to this data, paired with timely, relevant, […]

SANS Survey: Improving the Bottom Line with Effective Security Metrics
Meaningful security metrics are critical for both accurate insight into the status of an organization’s security and persuasive communication to management to back needed changes and support the level of resources required. This year’s SANS Security Metrics Survey reveals that much still needs to be done to fully realize the potential power that metrics bring […]

SANS Survey: Closing the Critical Skills Gap for Modern and Effective Security Operations Centers (SOCs)
The SANS survey “Closing the Critical Skills Gap for Modern and Effective Security Operations Centers (SOCs)” was launched just two days before the World Health Organization declared COVID-19 to be a pandemic. However, the survey included many questions about staff changes in 2019, qualitative responses on what skills security managers see they need, which needs […]

SANS 2020 Automation and Integration Survey
The SANS 2020 Automation and Integration Survey looks into how respondents are adopting systems, where their systems currently stand and what is on the planning horizon.

SANS Women in Cybersecurity Survey: Spanning the Career Life Cycle
The goal of this survey is to help women entering and advancing in the field of cybersecurity. The respondents, successful women working in varied roles in the cybersecurity community, were queried about everything from breaking into the field and gaining career momentum to choosing a specialty and finding ways to remain relevant. This report provides […]
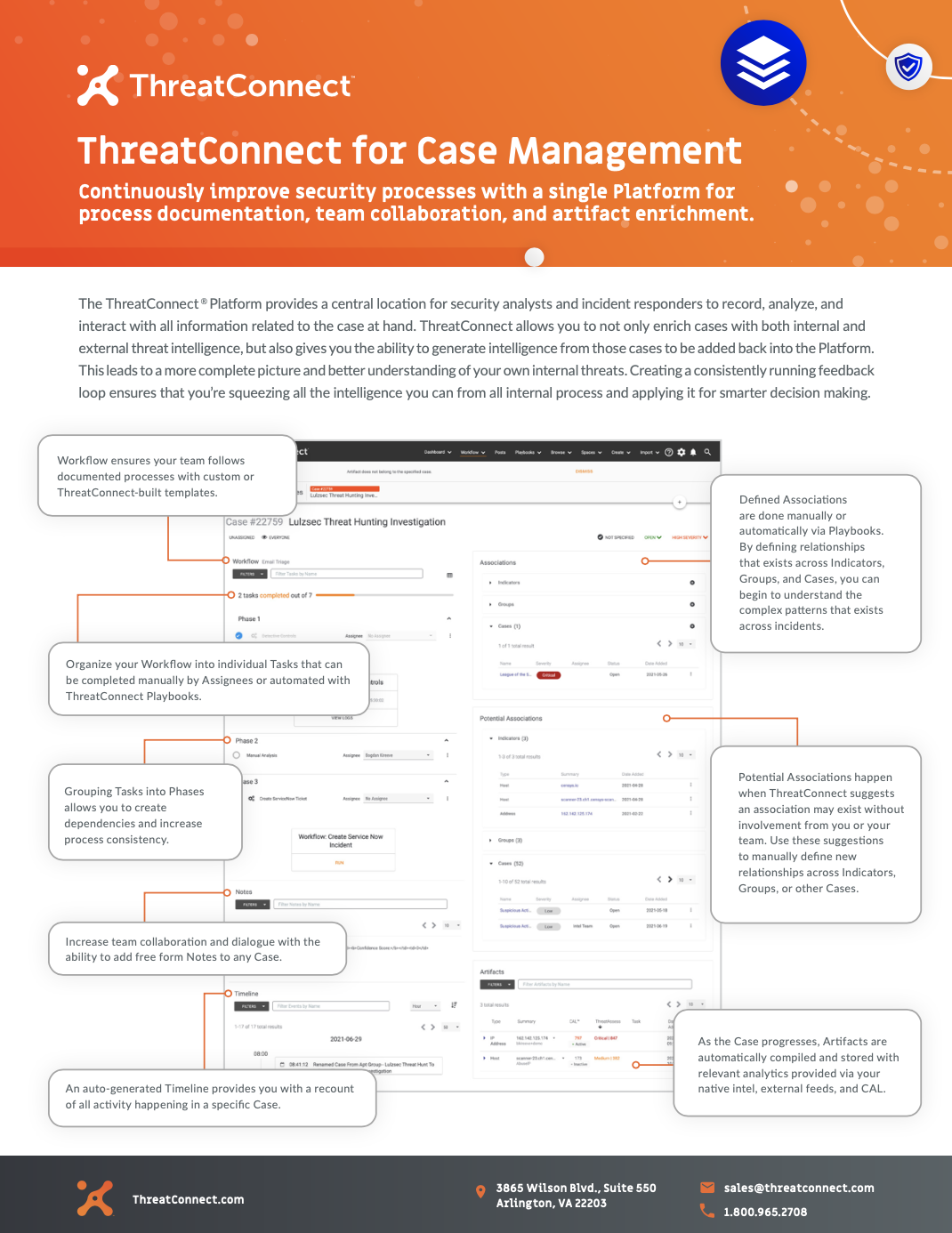
ThreatConnect for Case Management
Continuously improve security processes with a single Platform for process documentation, team collaboration, and artifact enrichment.

2020 SANS Cyber Threat Intelligence (CTI) Survey
The 2020 SANS Cyber Threat Intelligence Survey gathered current industry data from 1,006 respondents – a record number – and the highest ever reporting of CTI programs within organizations. SANS asked respondents to weigh in on how their programs measure effectiveness, an area that CTI programs must continue to improve on in the coming years.

Volume 2: Disrupting Adversary Infrastructure
Disrupting Adversary Infrastructure, Volume 2, ThreatConnect Tactics to Encourage Domain Registrar and State Entity Collaboration looks into how domain abuse takes its toll on businesses and how it can be alleviated using ThreatConnect’s capabilities to assess impact, apply countermeasures, and gather artifacts.

SANS 2019 Threat Hunting Survey: The Differing Needs of New and Experienced Hunters
The 2019 SANS Threat Hunting Survey gathered current industry data from 575 respondents predominantly from small/medium to medium/large organizations that are working in the field of threat hunting or working alongside threat hunters. This year’s report aims to help organizations understand what threat hunting is, why it is essential to protect their organizations, and how […]
SANSFIRE 2020 – Live Online
In this webinar, experts provide live online cyber security training in the wake of COVID-19.



