No Results Match Your Search
Please try again or contact marketing@threatconnect.com for more information on our resources.

CISO Challenges: Be Seen As An Enabler!
Cybersecurity often gets branded as a business expense but it is time to switch the narrative. CISOs need to show how an effective cybersecurity strategy is an enabler; to protect the business from risks and increase resilience. Watch this video by Gerald Caponera (VP Cyber Risk Strategy at ThreatConnect) for a masterclass on how […]
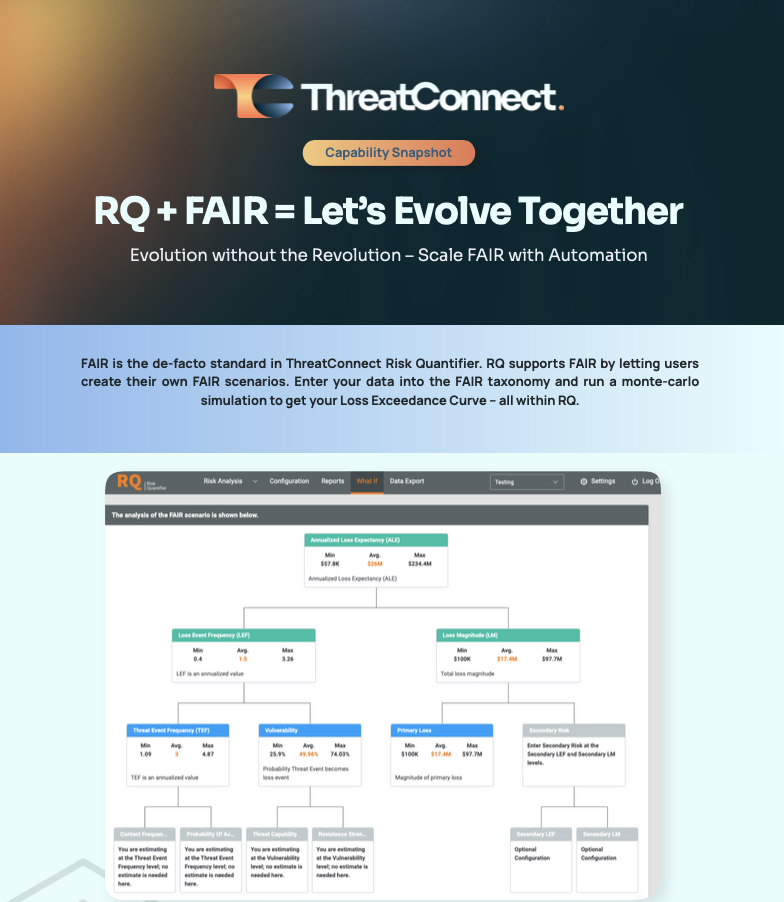
RQ + FAIR = Let’s Evolve Together
Overcoming challenges with FAIR is the key to seeing FAIR adopted at a wider scale in the industry and within companies that are using it today. RQ is introducing semi-Automated FAIR Scenarios that use automation to compute the Loss Event Frequency (LEF) portion of the FAIR taxonomy. Combine that with your Loss Magnitude projections and […]

ThreatConnect White Paper: Intelligence-Driven SOAR
What’s needed is a new approach, one that prioritizes real-world risk mitigation — so that SecOps teams can concentrate their efforts where they’ll have the biggest impact. This requires an intelligence-driven approach to Security Orchestration, Automation, and Response (SOAR).

Quantifying Risk & Understanding Cyber Insurance (On-Demand Webinar)
The cyber insurance industry is in turmoil as more and more businesses seek insurance protection against the onslaught of advanced threats, particularly ransomware, while both carriers and those seeking insurance lack the ability to automate risk and financial models to calculate security control improvements, improve response times and reduce exposure. Join ThreatConnect and AHT Insurance […]

ThreatConnect Threat Intelligence Platform (TIP) Data Sheet
The ThreatConnect Threat Intelligence Platform (TIP) centralizes the aggregation and management of all of your threat data. From one platform, normalize data from a variety of sources, add additional context, and automate manual threat intelligence-related security processes. ThreatConnect TIP provides you with a workbench to organize and prioritize your threat data and use it to […]

ThreatConnect Intelligence-Driven SOAR Data Sheet
ThreatConnect’s intelligence-driven Security Orchestration, Automation, and Response (SOAR) Platform provides a central location to integrate not only your security tools but all of your security team’s processes. Document those processes within ThreatConnect and increase efficiency with automation and orchestration. Continuously leverage high confidence threat intelligence stored within ThreatConnect when making decisions related to both tactics […]

Webinar: The Role of the CISO in Overhauling and Future-Proofing Cybersecurity
The CISO Challenge Series Webinar is based on the ThreatConnect Podcast’s new series that explores the five strategic challenges facing chief information security officers globally and how CISOs are innovating to overcome those challenges. Join us for this live CISO Challenge Webcast where three leading global CISOs will offer their perspectives on overhauling and future-proofing […]

Prioritize CVEs by Financial Risk with Risk Quantifier
With ThreatConnect Risk Quantifier (RQ), understand the potential financial risk that Common Vulnerabilities and Exposures (CVE’s) introduce to your organization and prioritize your patching efforts based on this. With the ability to automate the quantification of CVEs you can prioritize them by the amount of financial risk they bring to the organization. Prioritize Common Vulnerabilities […]

Enhance Your GRC Solution with ThreatConnect RQ
Governance, Risk, and Compliance (GRC) solutions are oftentimes at the center of an organization’s processes when it comes to managing risk for the business. With that in mind, having the most comprehensive view of all risks directly from the GRC solution is critical. Cyber risk is among the top 3 risks companies face, yet is […]

What If Analysis
What if you were asked what the quantified implications to cyber risk would be if your security budget was cut in half? Or maybe you might be tasked with deciding if it is possible to decrease security controls in one area and increase controls in another without any impact on financial risk. That’s why ThreatConnect […]

ThreatConnect RQ
Security organizations need to continually quantify cyber risk in financial terms and require a partner that helps them automate and orchestrate the right response. With ThreatConnect Risk Quantifier™ (RQ), you can automate cyber risk quantification in hours, unlike other approaches that take months and provide little to no actionable value as a result.

ThreatConnect and IntelFinder
IntelFinder is a fully automated and scalable service for customer–specific and actionable threat intelligence. The unique automated design enables IntelFinder to provide a comprehensive all–inclusive intelligence service at a fraction of the cost compared to existing services on the market. IntelFinder performs on–going monitoring to identify a wide variety of potential threats that exist outside […]



