No Results Match Your Search
Please try again or contact marketing@threatconnect.com for more information on our resources.

Leverage channel and integration colors for in-line context: Malware Analysis
Enhance cybersecurity with Polarity’s Malware Color Guide. Use color-coded visuals to prioritize threats, streamline analysis, and improve decision-making.

Use Cases and Quick Wins for Security Operations Centers
Revolutionize your SOC with Polarity’s augmented reality tool. Streamline workflows, enhance decision-making, and boost security efficiency.
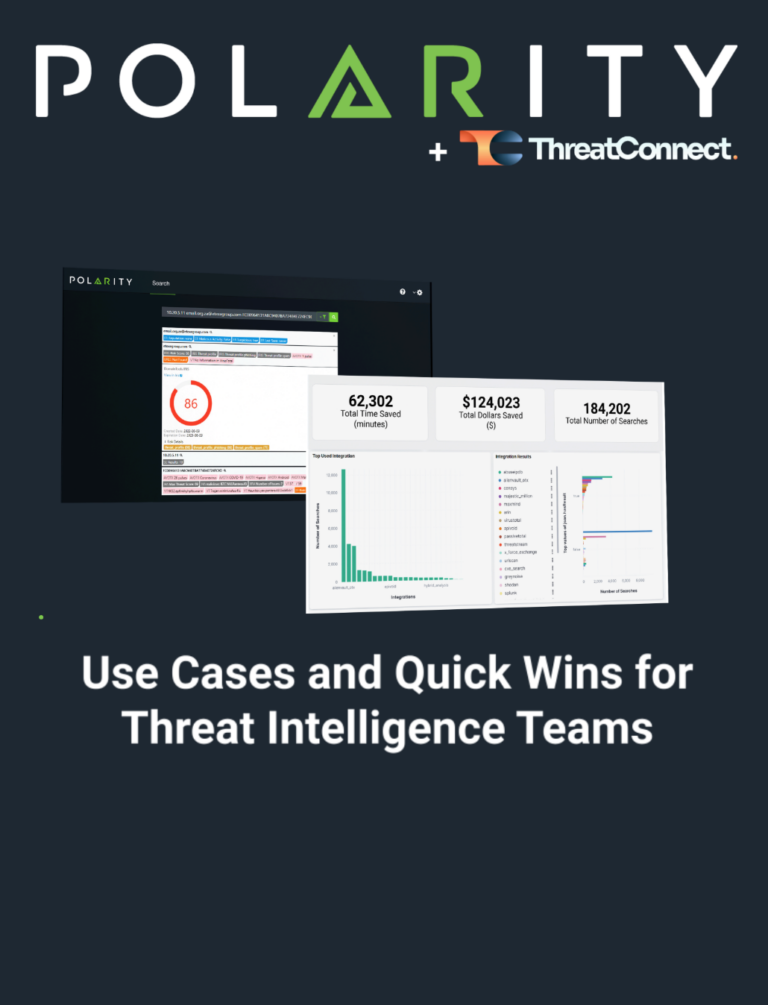
Use Cases and Quick Wins for Threat Intelligence Teams
Strengthen your security operations with Polarity. Access real-time threat intelligence, simplify decision-making, and maximize efficiency with effortless integration across more than 180 tools.

End-to-End Triage of Atomic Indicators with Polarity
Discover how Wyndham Hotels & Resorts enhanced cybersecurity with Polarity, streamlining threat response and boosting collaboration. Download the case study!
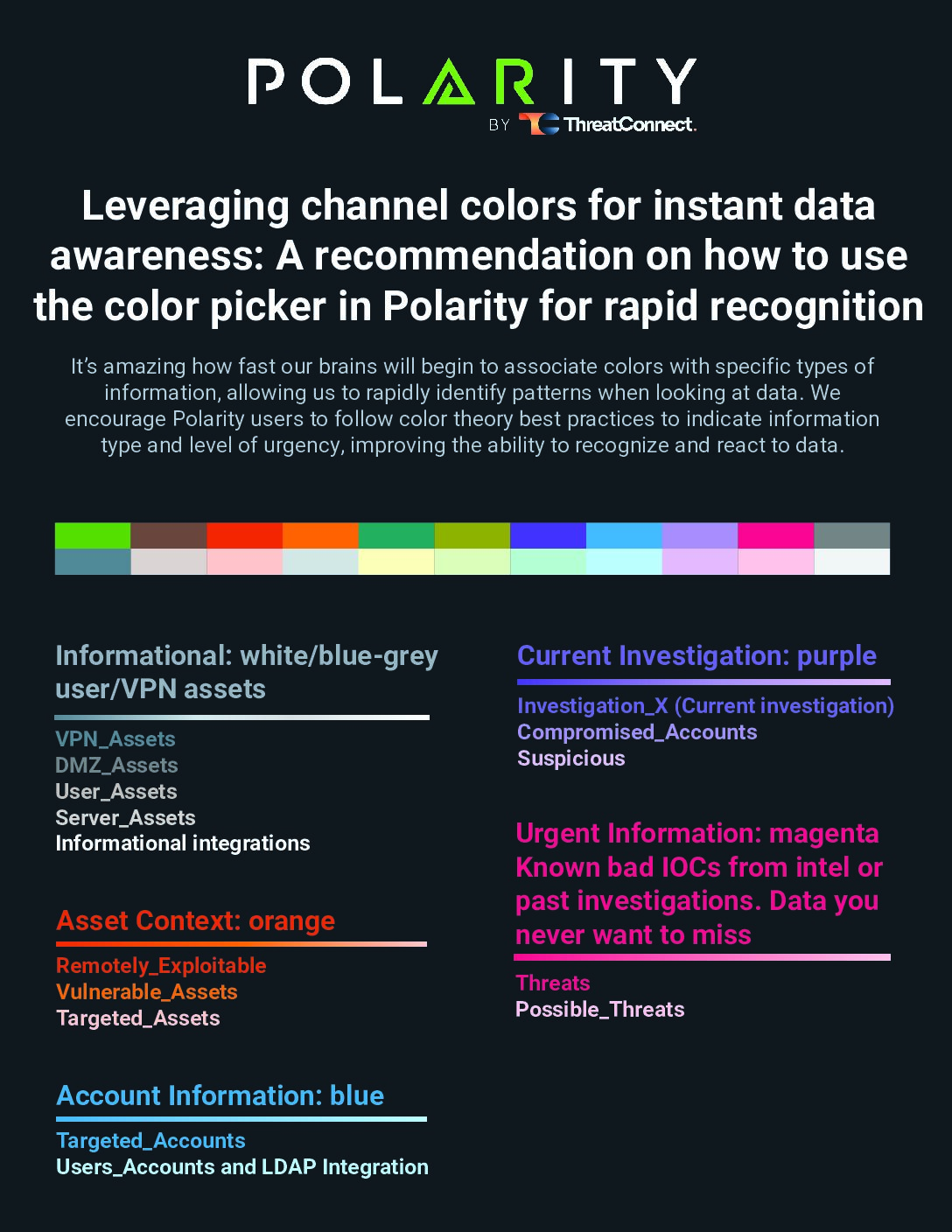
Leveraging channel colors for instant data awareness
By leveraging Polarity’s innovative color coding, you can quickly identify critical threats, streamline investigations, and prioritize vulnerabilities with ease. Assigning specific colors to data types ensures your team can respond faster and more effectively, transforming complexity into clarity. Ready to boost your efficiency? Download our Color Channels Guide today and take the first step toward […]

Advanced Threat Hunting
Proactively detect and neutralize cyber threats with advanced Threat Hunting strategies and tools like Polarity. Download our whitepaper to learn more.

Break Down Silos and Boost Productivity with Polarity
Solve knowledge silos with Polarity. Discover how unified access to tools, data, and teams enhances workflows for faster, smarter decisions. Download the brief.

ThreatConnect Report: CyberSecurity Under Stress
SecOps teams in the US and UK are being asked to do more with less, leading to higher stress levels that impact both their work and personal lives. The growing risk from cyber attacks is also compounded by significant recruitment and retention issues within cybersecurity.

A ThreatConnect Customer Success Story: Maturing Cybersecurity Infrastructure with Intelligence-Driven Operations
Find out how ThreatConnect enabled this organization to mature their cybersecurity infrastructure by: Removing silos, providing a centralized platform for threat intelligence and security operations personnel to execute daily tasks and manage their workflows together. Providing context for vast amounts of threat intelligence with our exclusive Collective Analytics Layer or CAL™️, so the team could […]

Modernize Your Threat Intelligence Platform (TIP) Whitepaper
A modern Threat Intelligence Platform (TIP) can help right the balance of power between attackers and defenders by allowing CTI teams to build, focus, and provide threat intelligence relevant to the business and showing SecOps teams exactly where to apply their efforts to yield maximum results.
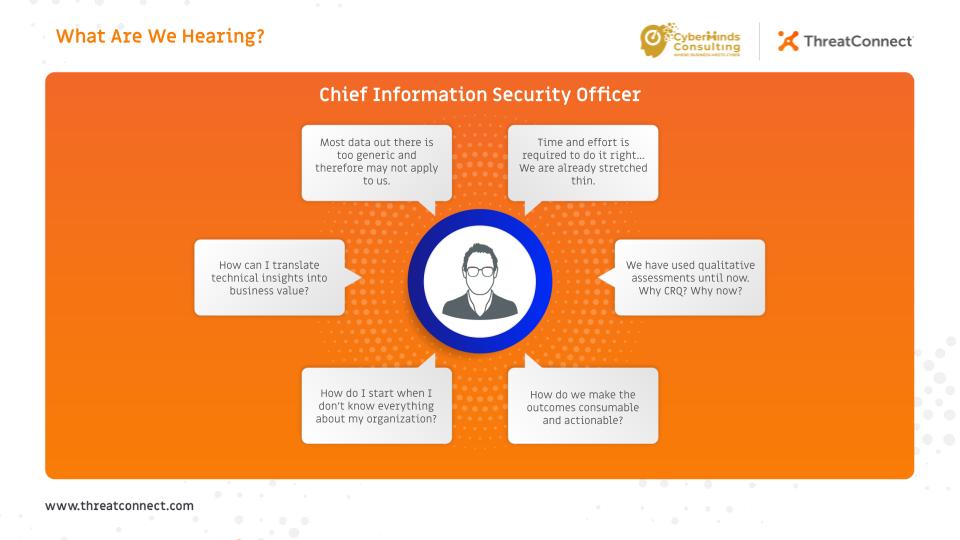
Cyber Risk Quantification – A practical guide for the C-Suite
For most firms, cyber risk management is an endless discussion of theoretical risk postures and registers filled with aging risk topics. Risk-based, data-driven quantitative models, such as ones promoted by the FAIR Institute are comprehensive, and elaborate; however, they require significant horsepower to demonstrate visible and traceable value. CISOs, CFOs, CIOs and other C-level executives […]
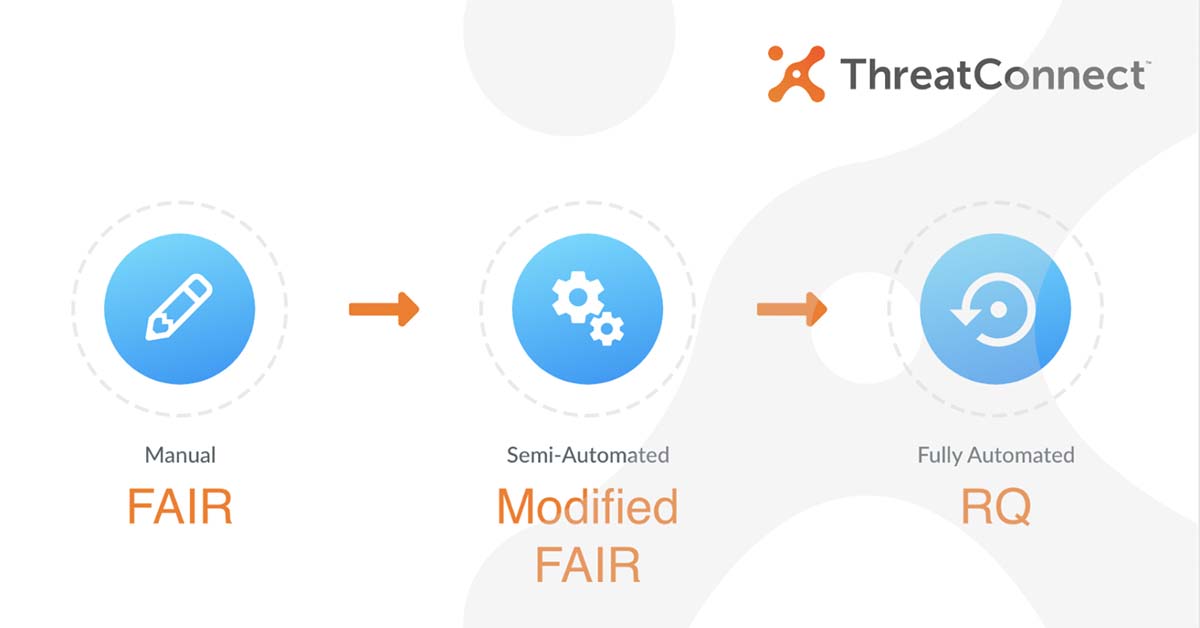
Evolving risk quantification using automation
At ThreatConnect, we hear firsthand that organizations are struggling to implement the FAIR model for cyber risk quantification so we designed a way to solve this issue. Risk Quantification 6.0 (RQ) provides the semi-automation companies need to evolve existing FAIR practices to scale and show a wide range of financial impacts and risk scenarios with […]



