Tenable
Tenable®️, Inc. is the Cyber Exposure company. Over 30,000 organizations around the globe rely on Tenable to understand and reduce cyber risk. As the creator of Nessus®️, Tenable extended its expertise in vulnerabilities to deliver the world’s first platform to see and secure any digital asset on any computing platform. Tenable customers include more than 50 percent of the Fortune 500, more than 30 percent of the Global 2000 and large government agencies.
Specialties
Integration(s)
Built By ThreatConnect
Related Resources
Built By ThreatConnect
Related Resources
Built By Polarity

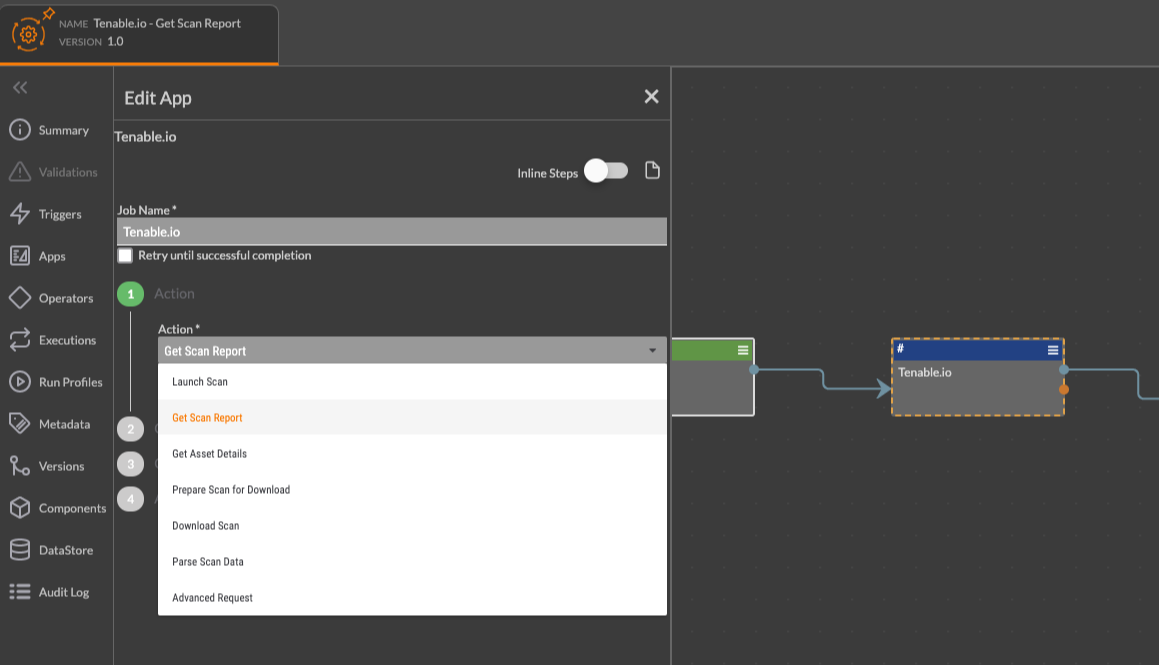
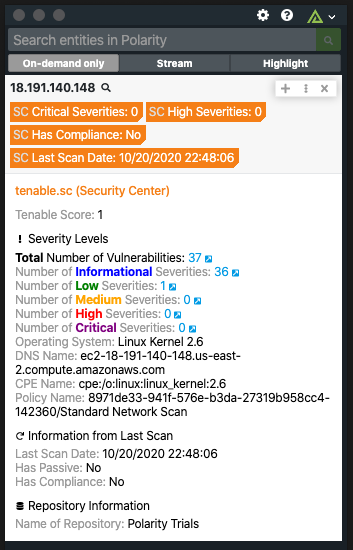
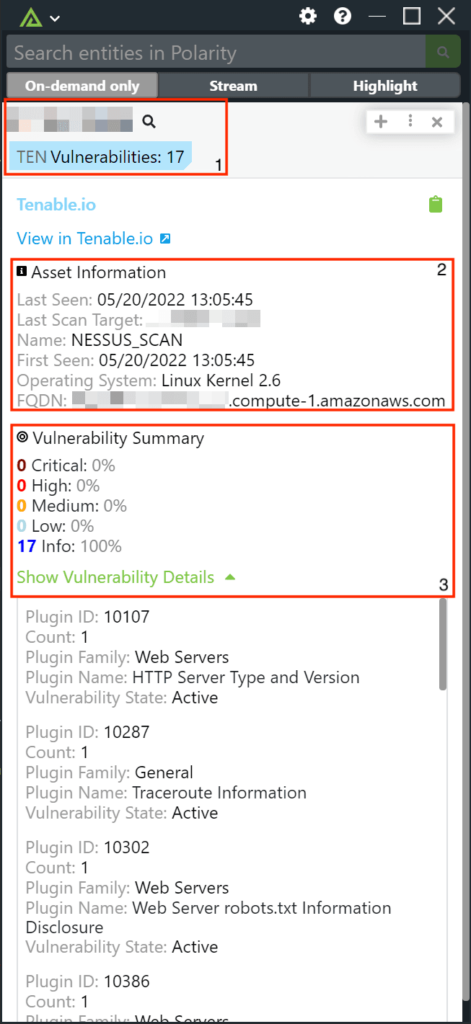
 Polarity
Polarity