SlashNext Phishing Incident Response
SlashNext Phishing Incident Response Playbook app enables ThreatConnect SOAR users to fully automate analysis of suspicious URLs. For example, IR teams responsible for abuse inbox management can extract links or domains out of suspicious emails and automatically analyze them with the SlashNext SEER™ threat detection cloud to get definitive, binary verdicts (malicious or benign) along with IOCs, screenshots, and more. Automating URL analysis can save IR teams hundreds of hours versus manually triaging these emails or checking URLs and domains against less accurate phishing databases and domain reputation services.
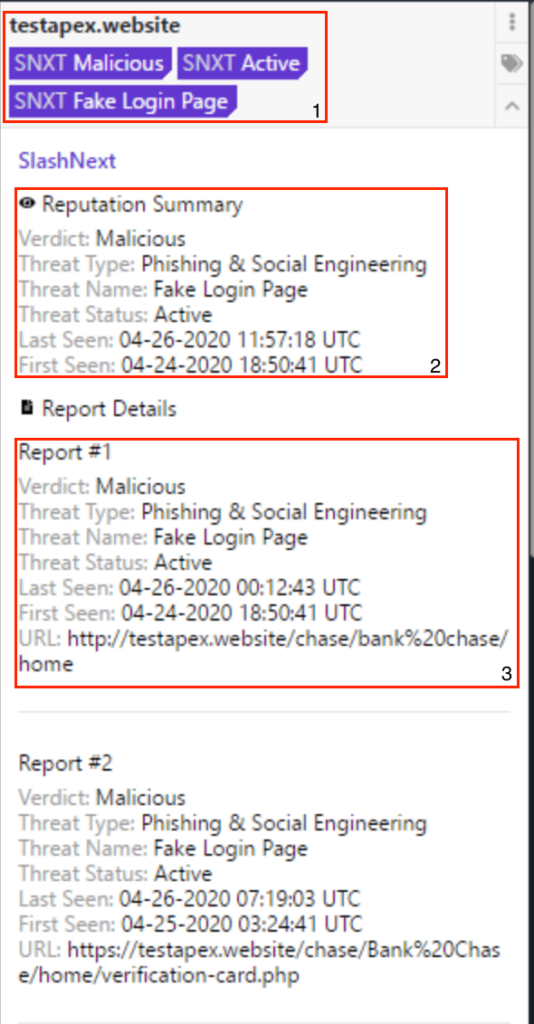
SlashNext threat detection uses browsers in a purpose-built cloud to dynamically inspect page contents and site behavior in real-time. This method enables SlashNext to follow URL re-directs and multi-stage attacks to more thoroughly analyze the final page(s) and make a much more accurate, binary determination with near-zero false positives. It also detects all six major categories of phishing and social engineering sites. These include credential stealing, rogue software / malware sites, scare-ware, phishing exploits (sites hosting weaponized documents, etc.), and social engineering scams (fake deals, giveaways, etc.).
SlashNext not only provides accurate, binary verdicts (rather than threat scores), it provides IoC metadata and screen-shots of detected phishing pages. These enable easier classification and reporting. Screen-shots can be used as an aid in on-going employee phishing awareness training and testing.
This app is developed and maintained by SlashNext. This app is available for download on this Marketplace.
Keep Reading


 Polarity
Polarity