SentinelOne
With the SentinelOne integration, users have the ability to interact with agents, threats, hashes, exclusions and blocklist items inside the SentinelOne platform. Utilizing these capabilities allows customers to determine whether threats are malicious or not. This gives the opportunity to run automated responses such as isolating an infected endpoint from the network.
The following actions are available:
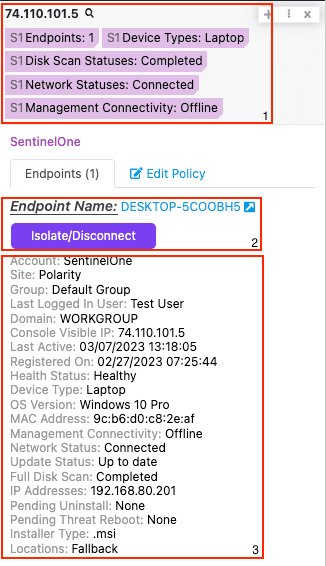
- Get Endpoint - Retrieve an endpoint's details. An endpoint is referred to as an "agent" inside the SentinelOne platform.
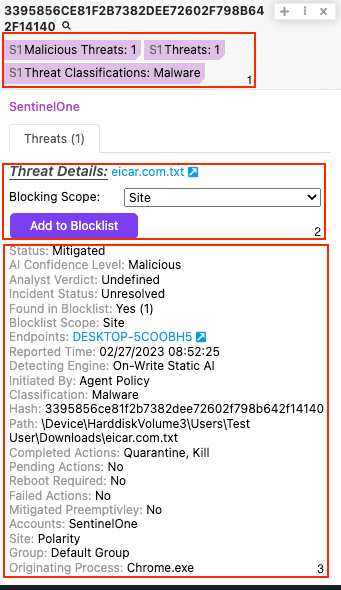
- List Threats - Return all threats that meet the filter criteria.
- List Endpoints- Return all agents that meet the filter criteria.
- Get Hash Reputation - Get the reputation of a hash, given the required SHA1.
- Create Blocked Item - Create a blocklist item for a SHA1 hash, for the scopes you enter in the filter fields. You can add the hash to multiple Groups, Sites, Accounts, and to the Global list.
- Delete Blocked Items - Delete items based on their hash IDs.
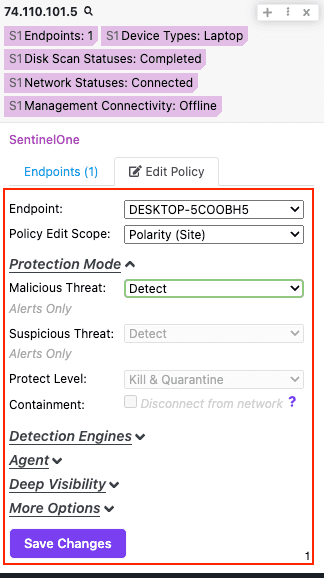
- Create Exclusion - Create Exclusions to make your Agents suppress alerts and mitigation for items that you consider to be benign or which you require for interoperability.
- Update Exclusion - Update an exclusion's details.
- Delete Exclusions - Delete exclusions by referencing their exclusion IDs.
This app can be found in the ThreatConnect App Catalog under the name: SentinelOne
Keep Reading


 Polarity
Polarity