Reversing Labs
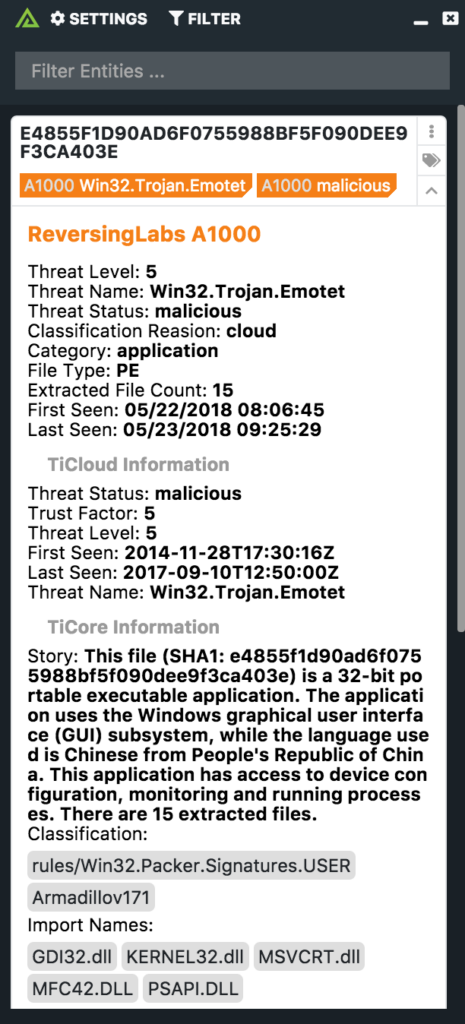
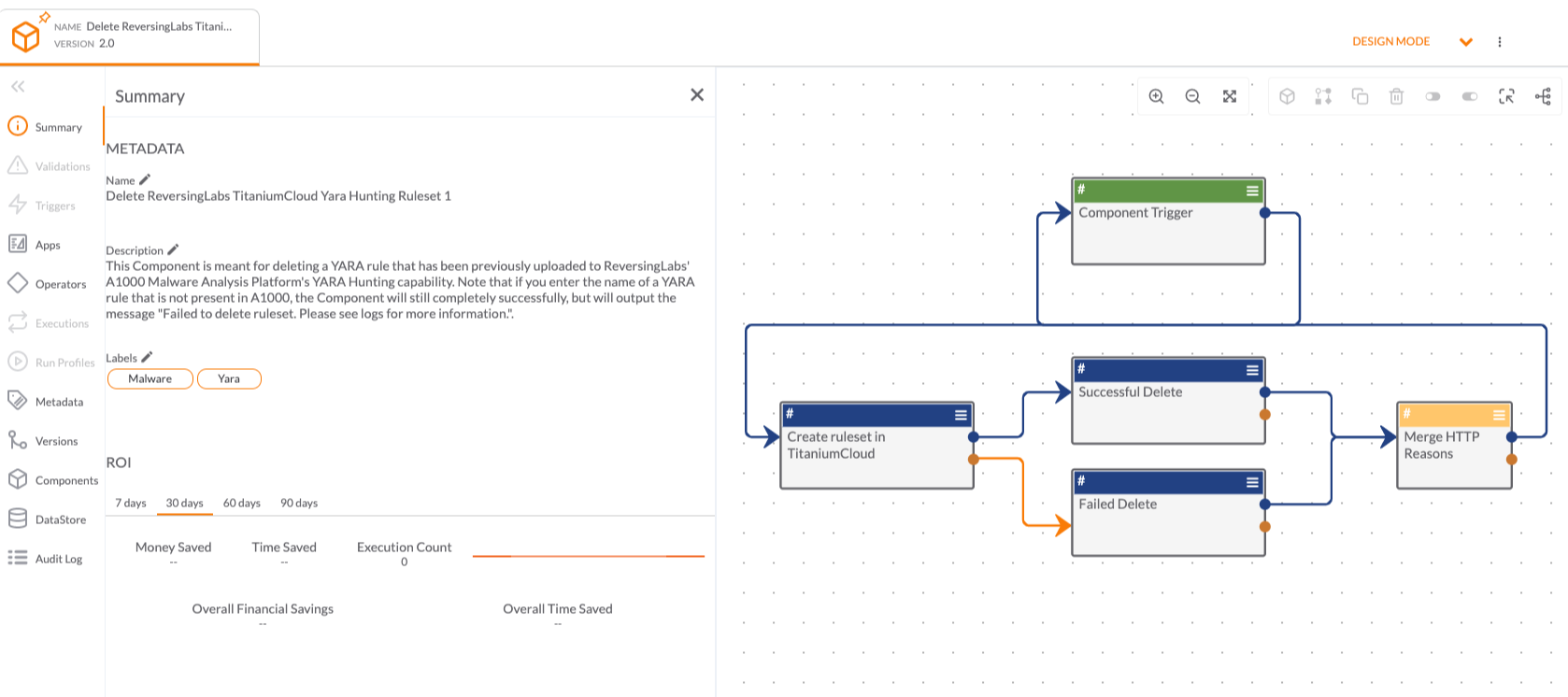
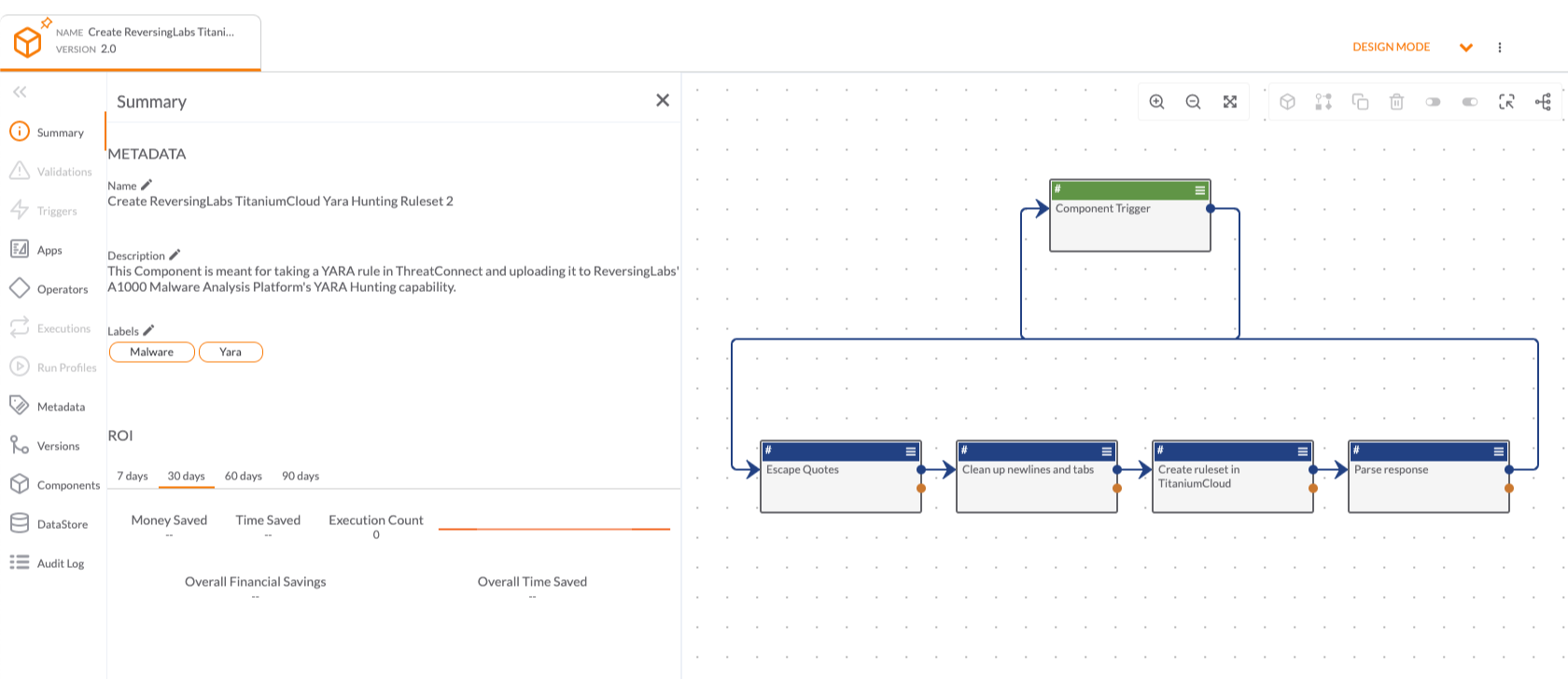
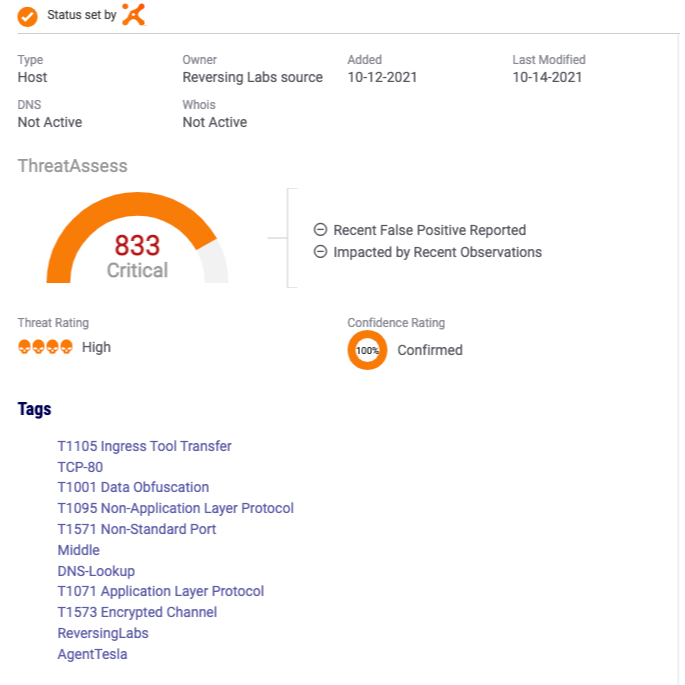
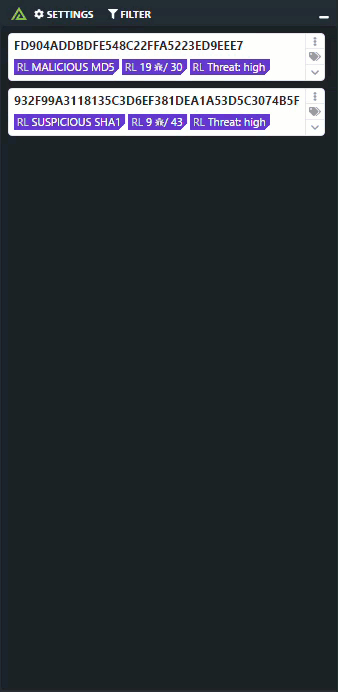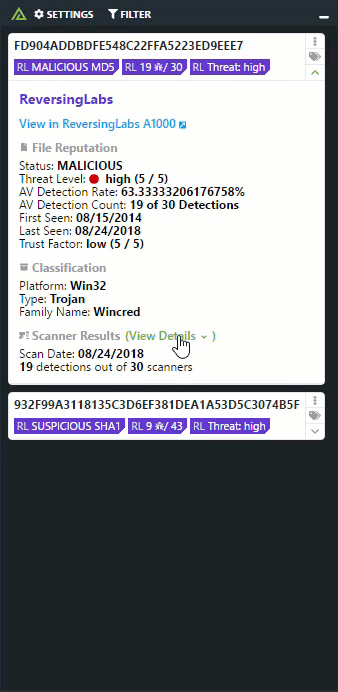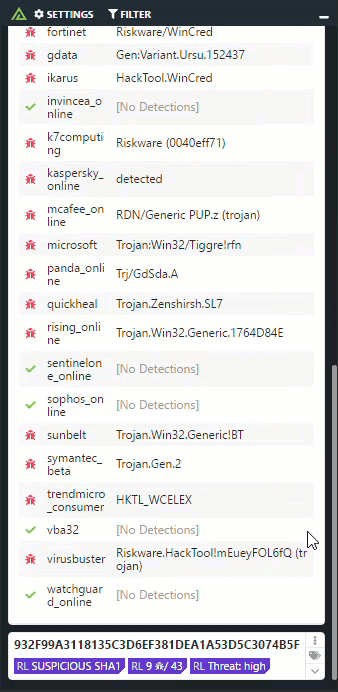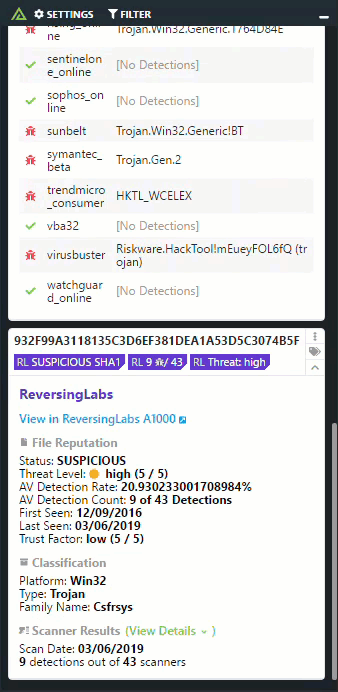
ReversingLabs solutions drastically accelerate and broaden organizations’s ability to detect new threats, respond to incidents and gain intelligence on attacks. Large enterprises and security vendors use these solutions as a foundation for protecting digital assets. Our solutions implement unique, innovative technologies that detect and analyze threats within files. TitaniumCore™ Automated Static Analysis evaluates internal threat indicators in files in milliseconds to support real-time and high volume applications. TitaniumCloud™ File Reputation service identifies and provides up-to-date threat intelligence on 2 billion goodware and malware files.
Integrations
Built By ThreatConnect
Downloads
Related Resources
Built By Partner
Built By ThreatConnect
Built By ThreatConnect
ReversingLabs A1000 with Polarity
Keep ReadingPlaybooks
Built By ThreatConnect

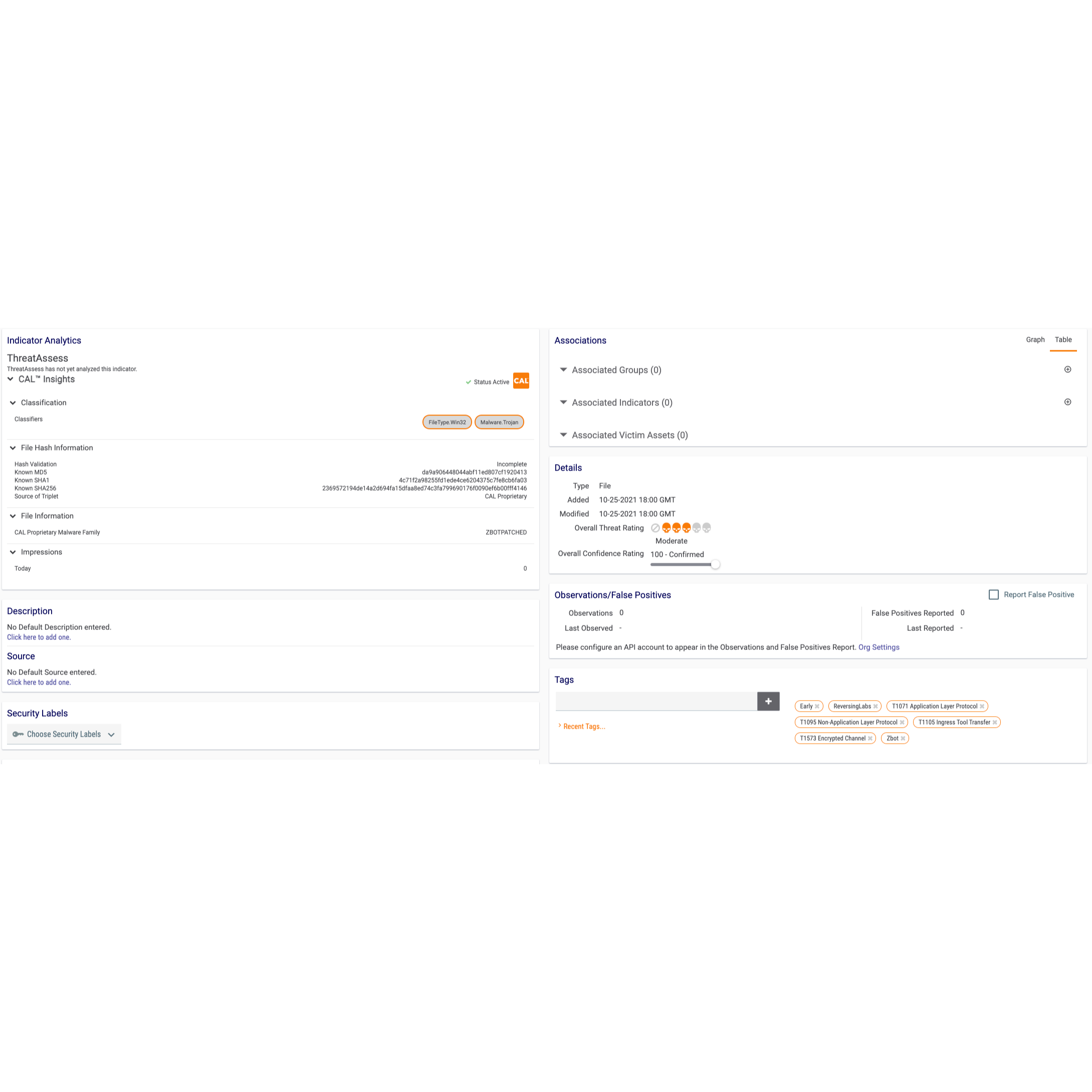
 Polarity
Polarity