Mandiant
Mandiant is recognized by enterprises, governments and law enforcement agencies worldwide as the market leader in threat intelligence and expertise gained on the frontlines of cyber security. To make every organization confidently ready for cyber threats, Mandiant scales its intelligence and expertise through the Mandiant Advantage SaaS platform to deliver current intelligence, automation of alert investigation and prioritization and validation of security controls products from a variety of vendors.
Integrations
Related Resources
Built By ThreatConnect
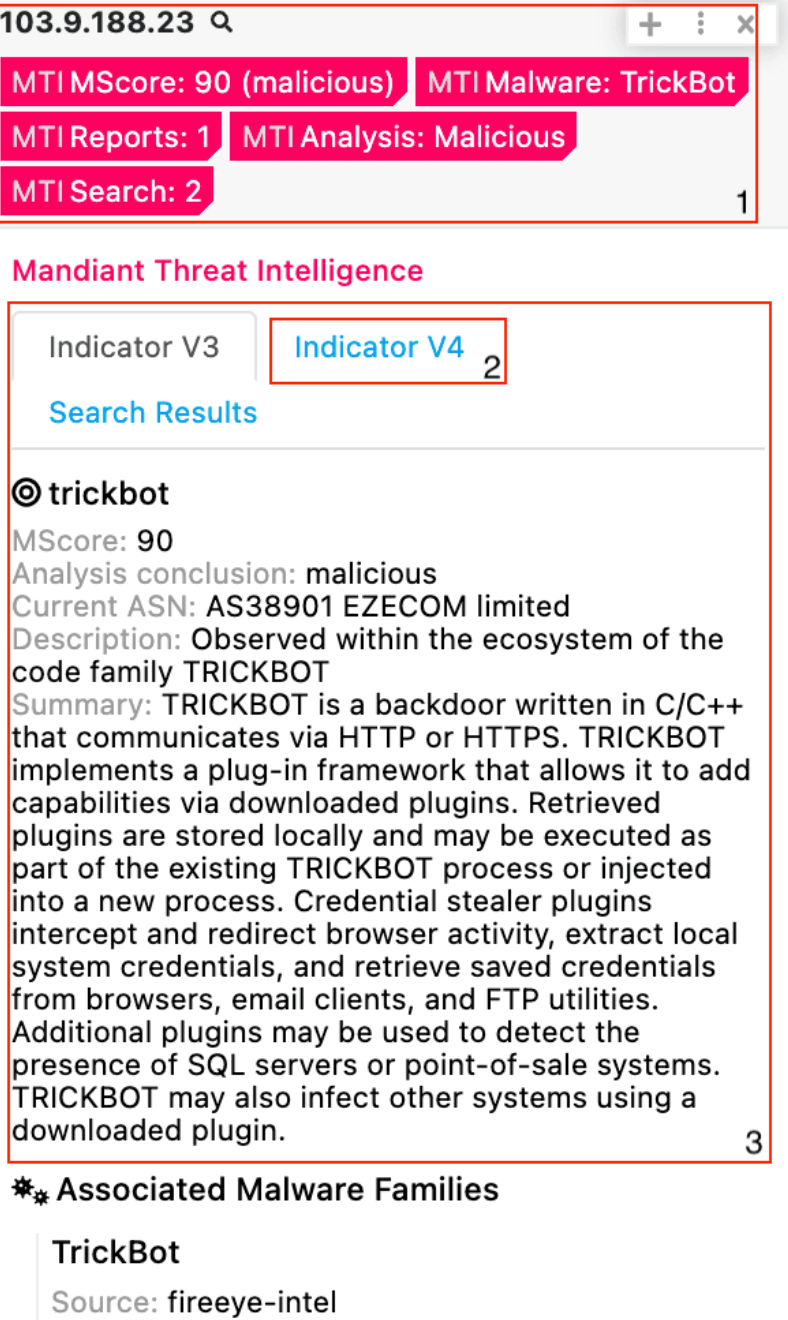
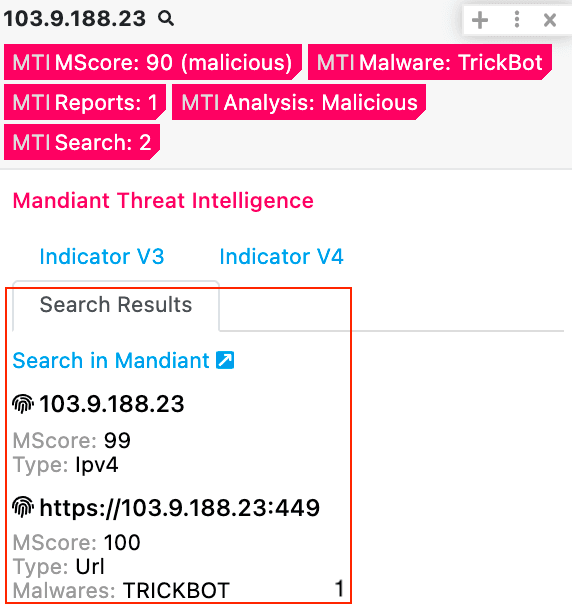
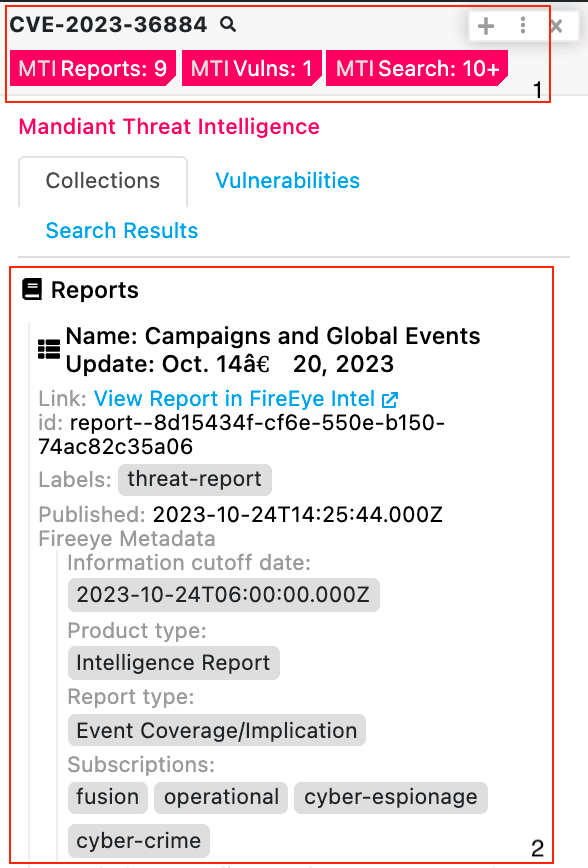
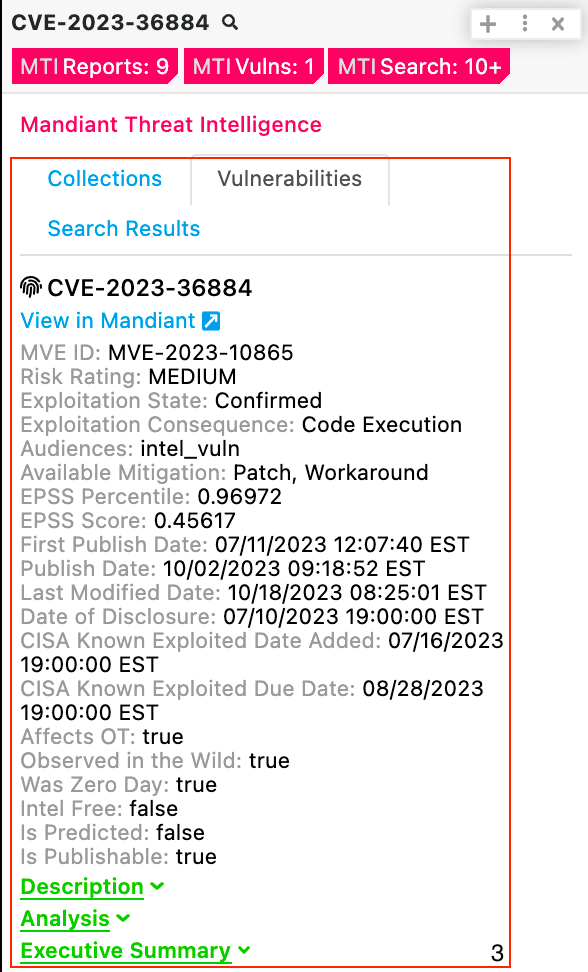
Mandiant Threat Intelligence with Polarity
Keep ReadingRelated Resources
Built By Polarity