GreyNoise
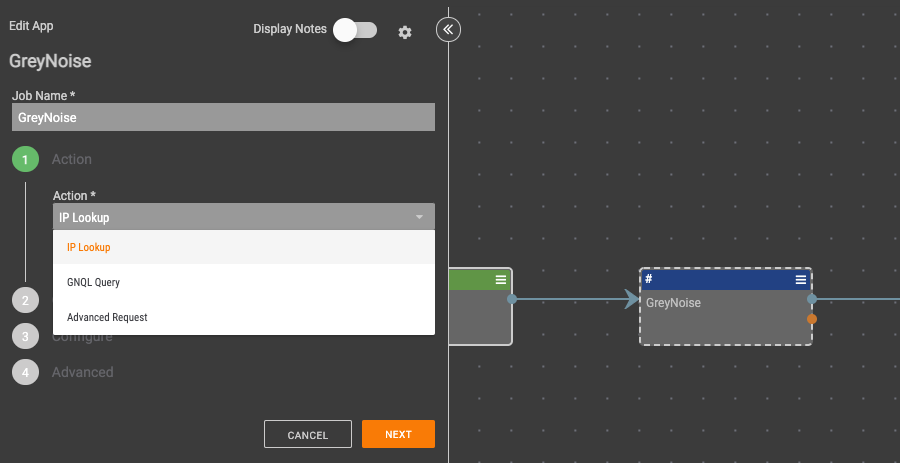
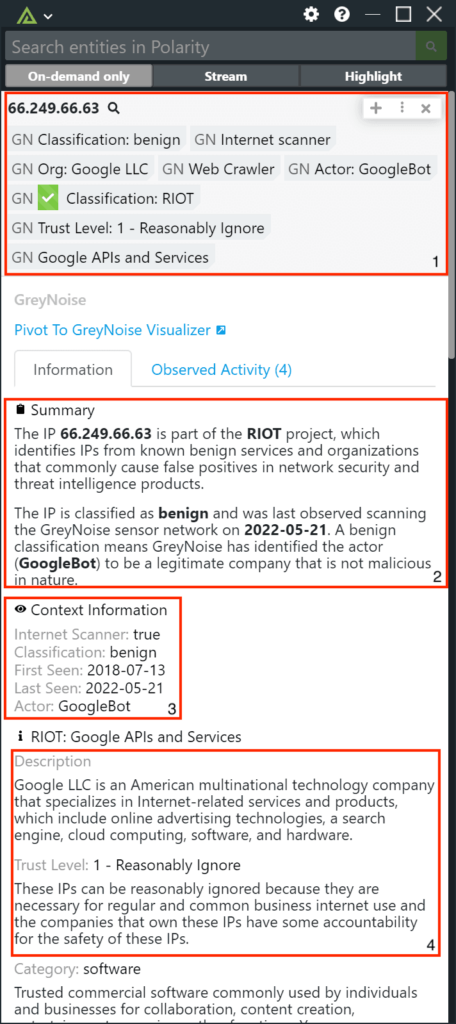
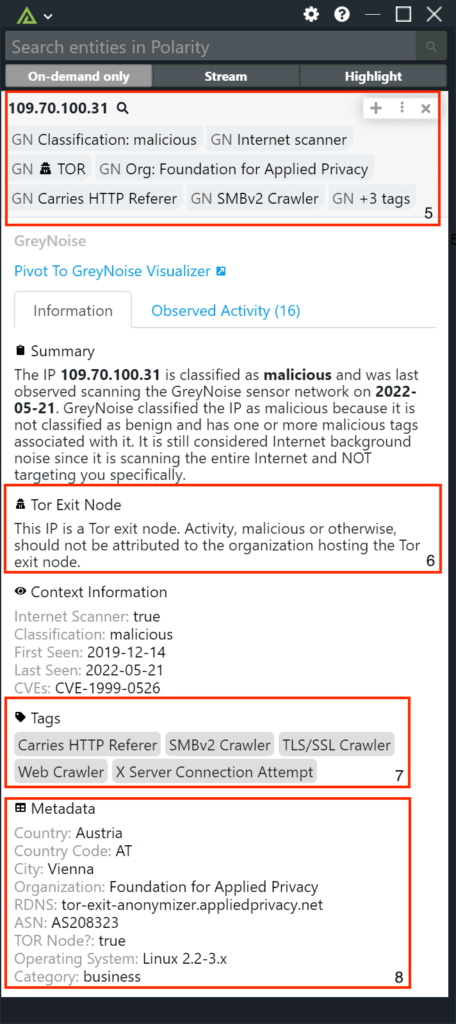
GreyNoise is a cybersecurity company that filters Internet background noise. It collects, analyzes, and labels mass internet scan and attack activity into a feed of Anti-Threat Intelligence. This context helps security teams reduce noise and prioritize signal-targeted attacks against their organization. Its drive to maximize analyst efficiency is delivered through its API, platform integrations, and visualizer. The company was founded in 2017 and is based in Washington, District of Columbia.
Integrations
Built By ThreatConnect
Built By ThreatConnect
GreyNoise with Polarity
Keep ReadingRelated Resources
Built By Polarity