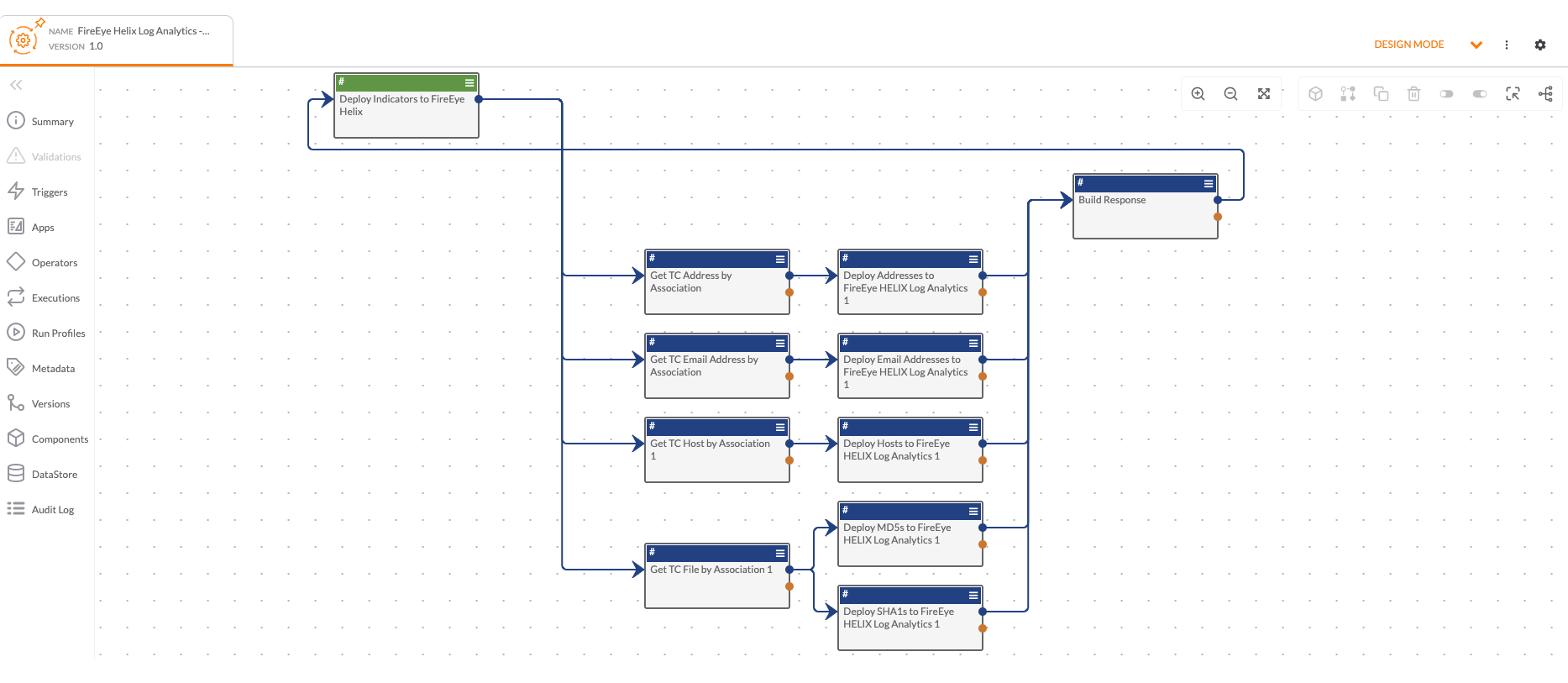
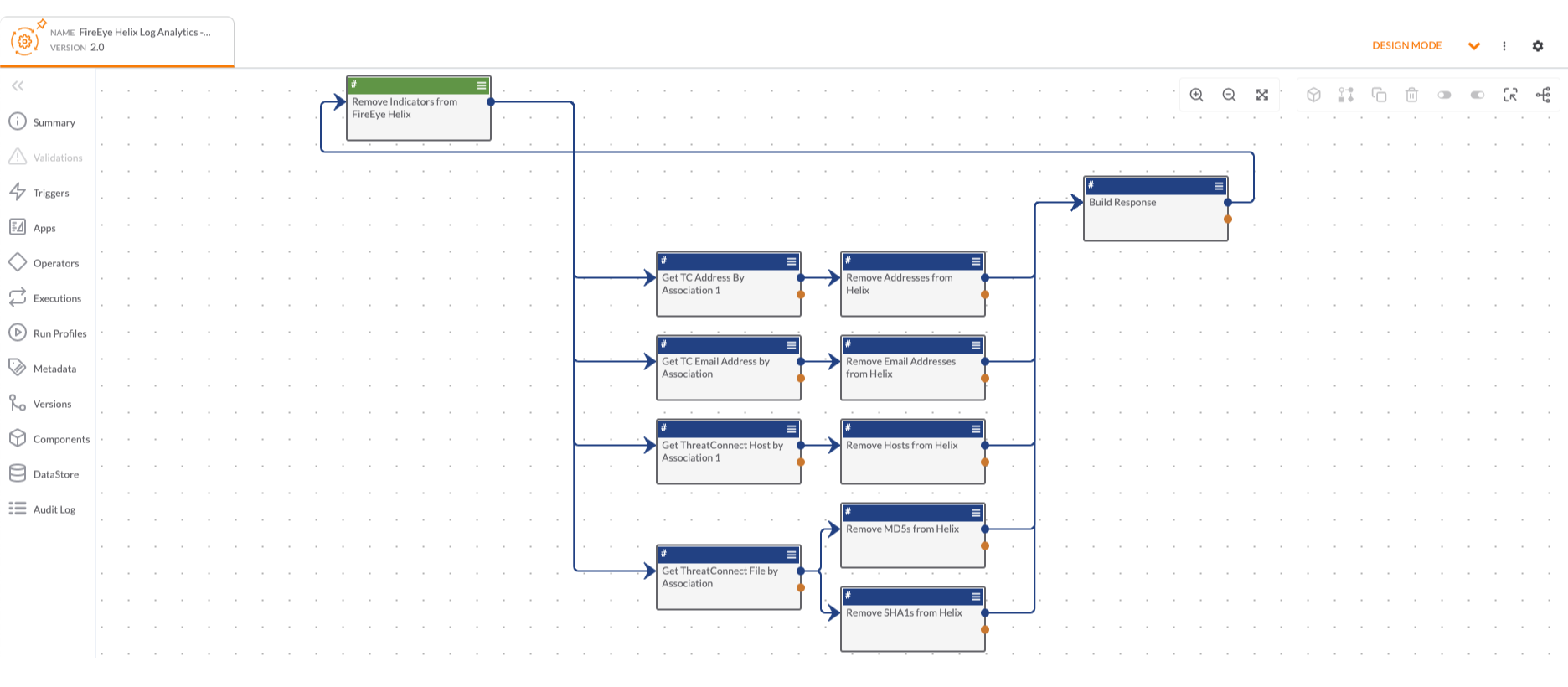
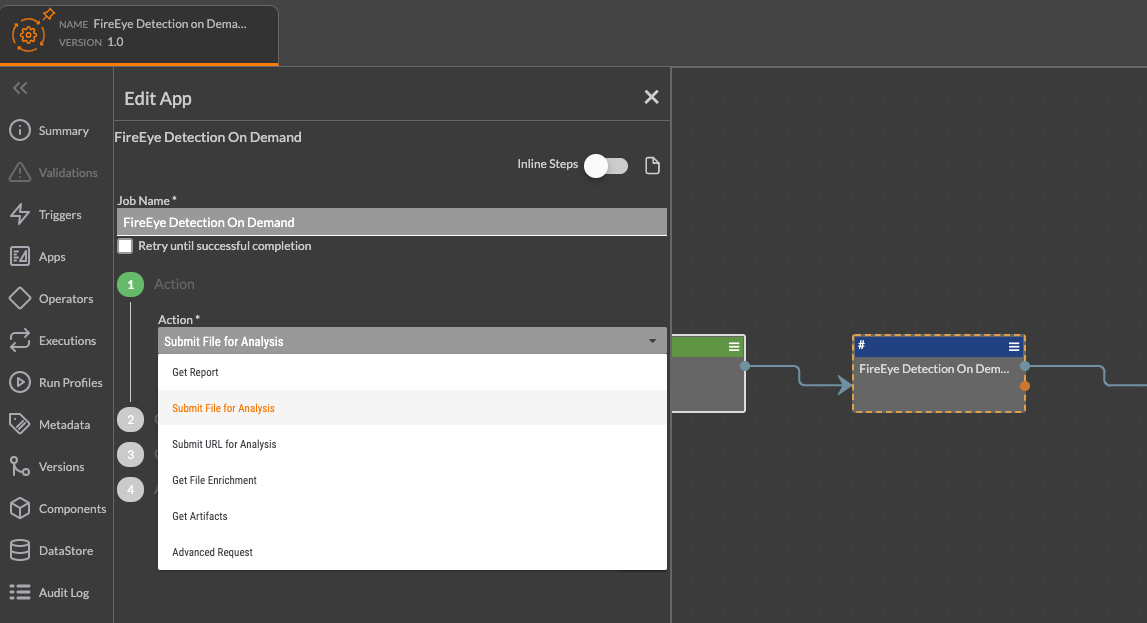
Fireeye Detection on Demand
With this Playbook app, you can automatically detonate, analyze, and submit files and URLs in FireEye from ThreatConnect to understand if they are malicious and return any contextualized telemetry. This all leads to more informed decision-making and more efficient remediation of malicious files through automation.
The following actions are available within the Playbook App:
- Get Report - Search by a Report ID to retrieve details based on the report.
- Submit File for Analysis - Submit a file for analysis.
- Submit URL for Analysis - Submit a URL for analysis.
- Get File Enrichment - Retrieve details about an analysis by its MD5 Hash ID.
- Get Artifacts - Retrieve artifacts from a report
- Advanced Request - Create a custom API request to the FireEye Detection on Demand API
This app can be found in the ThreatConnect App Catalog under the name: FireEye Detection on Demand
Keep Reading

 Polarity
Polarity