VMware Carbon Black
VMware Carbon Black leads a new era of endpoint security by enabling organizations to disrupt advanced attacks, deploy the best prevention strategies for their business, and leverage the expertise of 10,000 professionals to shift the balance of power back to security teams. Only VMware Carbon Black continuously records and centrally retains all endpoint activity, making it easy to track an attacker’s every action, instantly scope every incident, unravel entire attacks and determine root causes. VMware Carbon Black also offers a range of prevention options so organizations can match their endpoint defense to their business needs. VMware Carbon Black has been named #1 in endpoint protection, incident response, and market share. Forward-thinking companies choose VMware Carbon Black to arm their endpoints, enabling security teams to: Disrupt. Defend. Unite.
Integrations
Related Resources
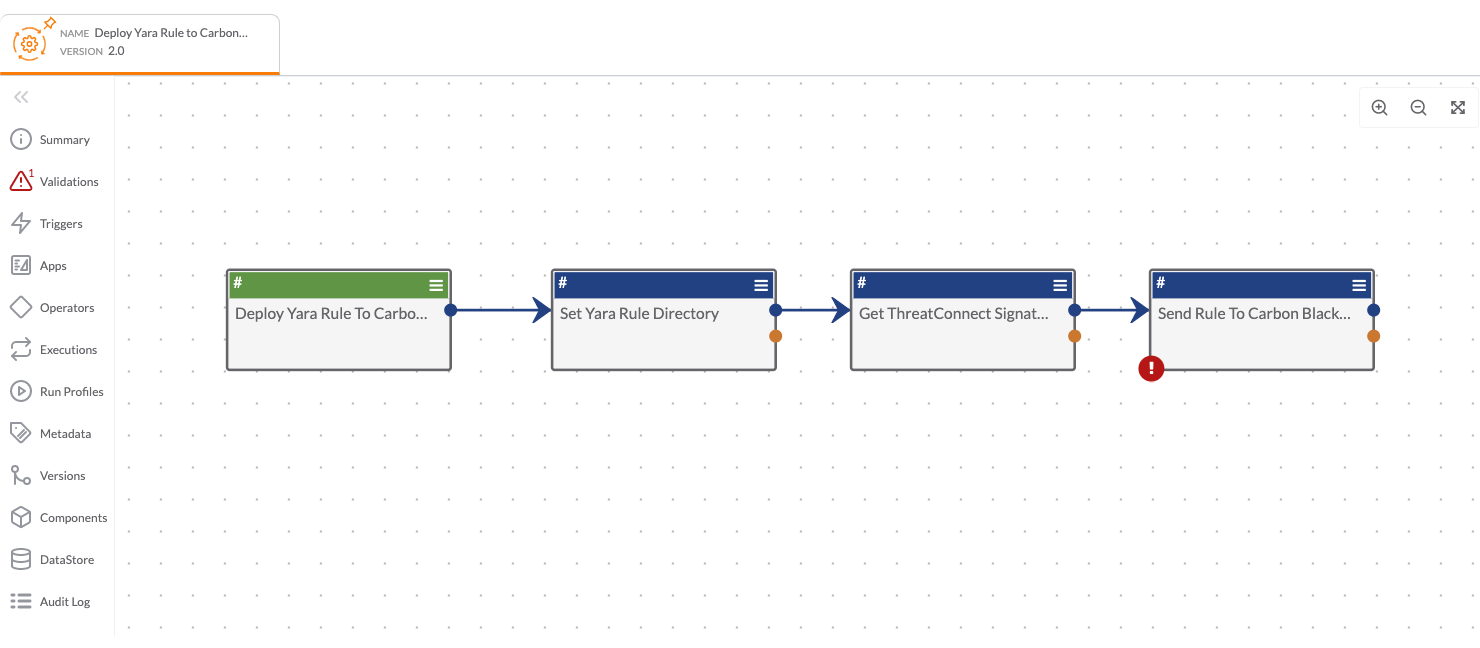
Built By ThreatConnect
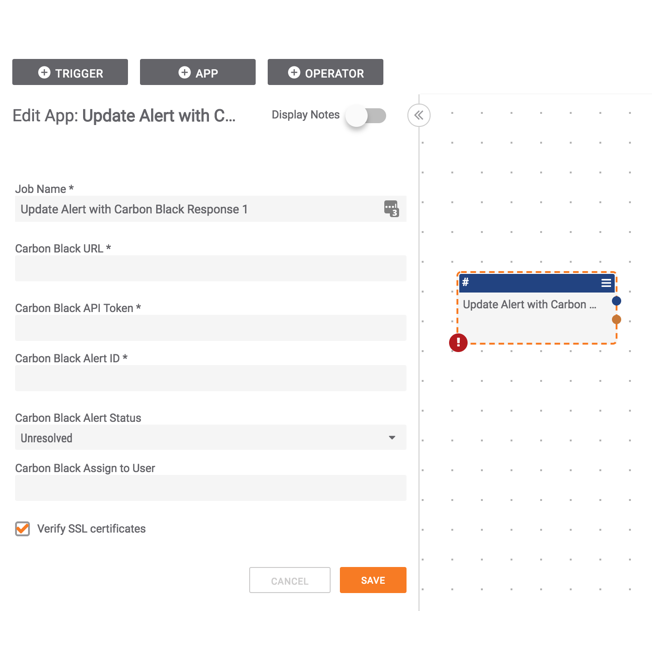
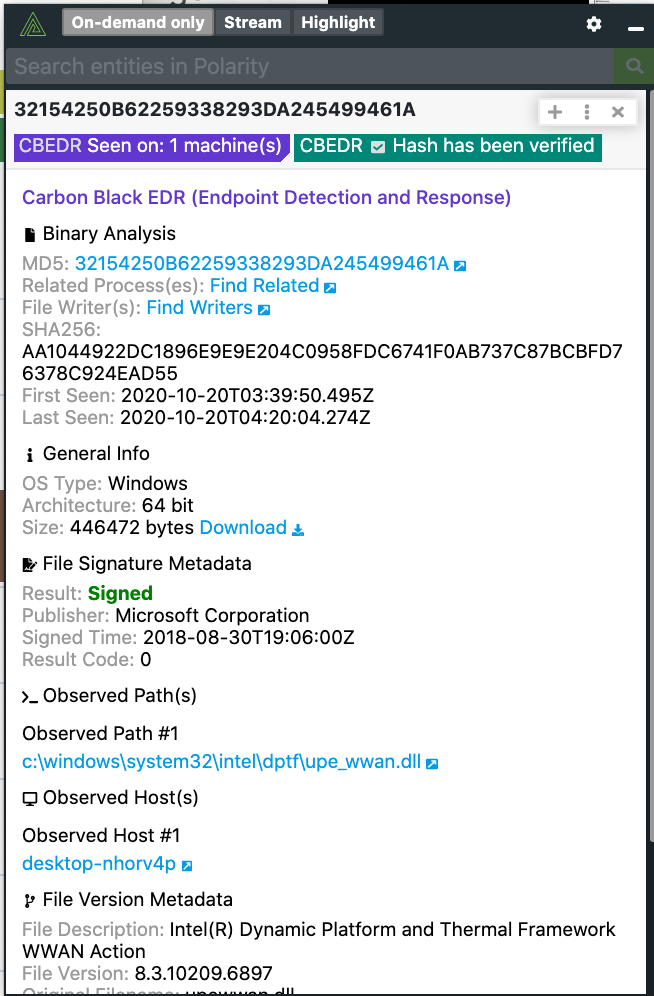
VMware Carbon Black with Polarity
Keep ReadingProducts
-
 Polarity
Polarity
Related Resources
Built By Polarity