AWS
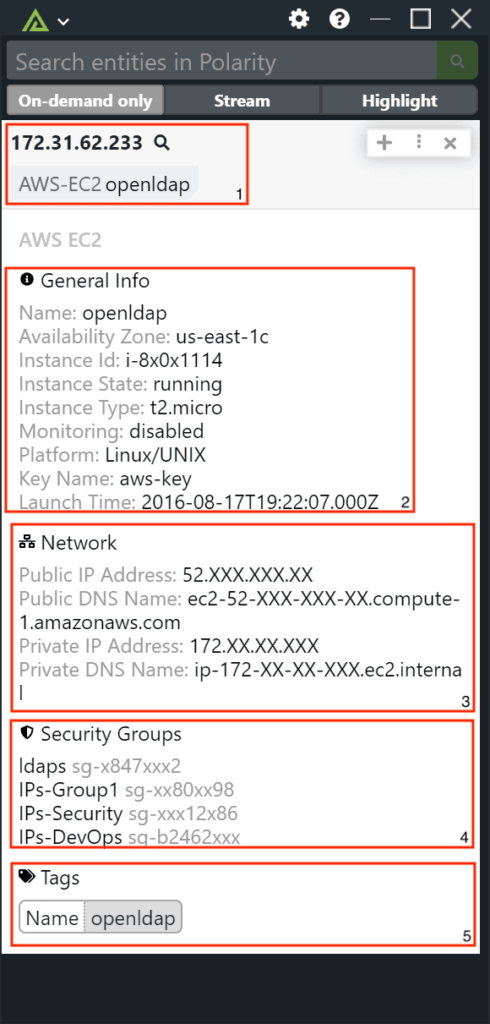
Amazon Web Services (AWS) is the world’s most comprehensive and broadly adopted cloud, offering over 200 fully featured services from data centers globally. Millions of customers—including the fastest-growing startups, largest enterprises, and leading government agencies—are using AWS to lower costs, become more agile, and innovate faster.
Playbooks
Related Resources
Built By ThreatConnect
Related Resources
Built By ThreatConnect
Related Resources
Built By ThreatConnect
Integrations
Related Resources
Built By ThreatConnect


 Polarity
Polarity