Anomali
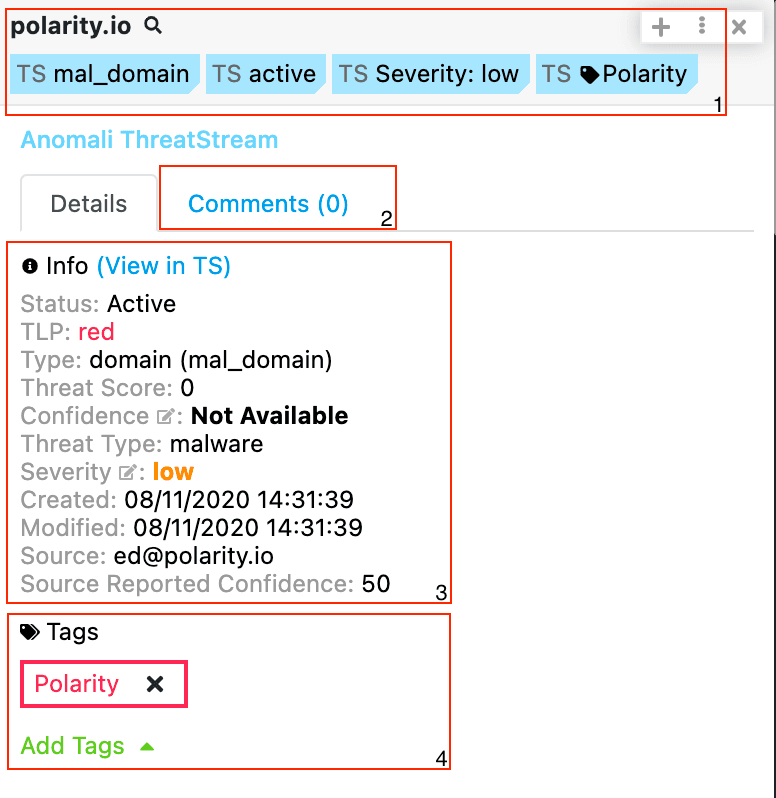
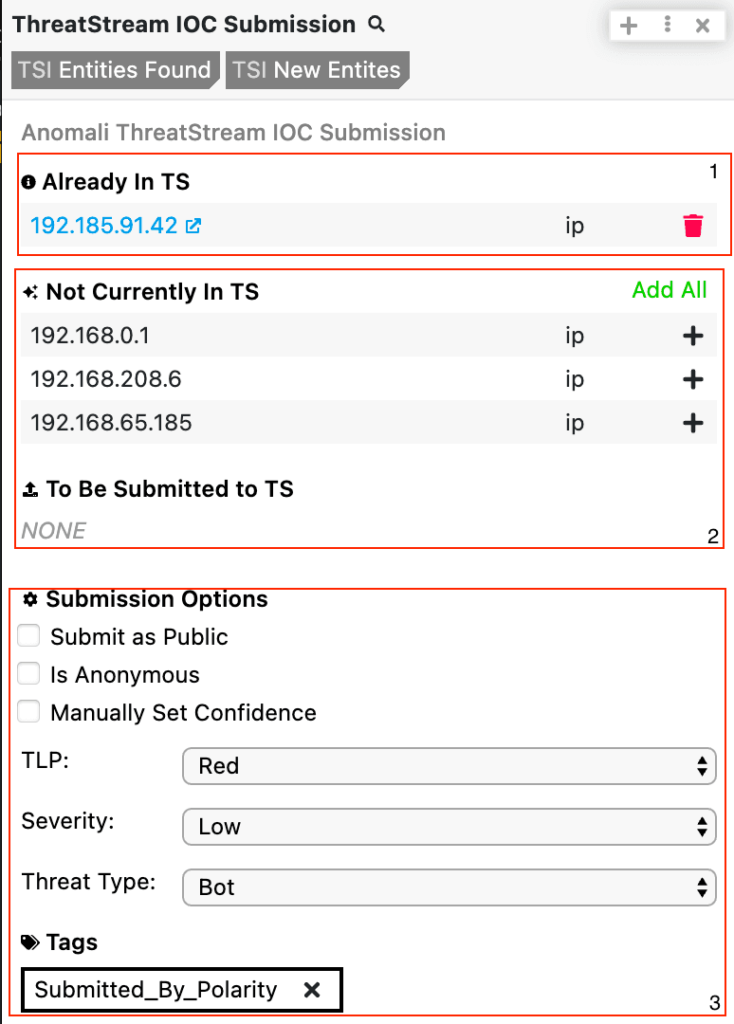
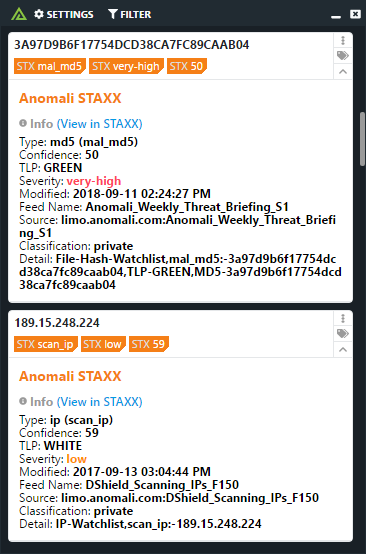
Anomali provides cybersecurity solutions that integrate threat intelligence, analytics, and automation to help organizations detect, investigate, and respond to cyber threats efficiently.
Specialties
Products
Integrations
Related Resources
Built By Polarity


 Polarity
Polarity