Posted
Detect a website’s content management system (CMS)
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention.
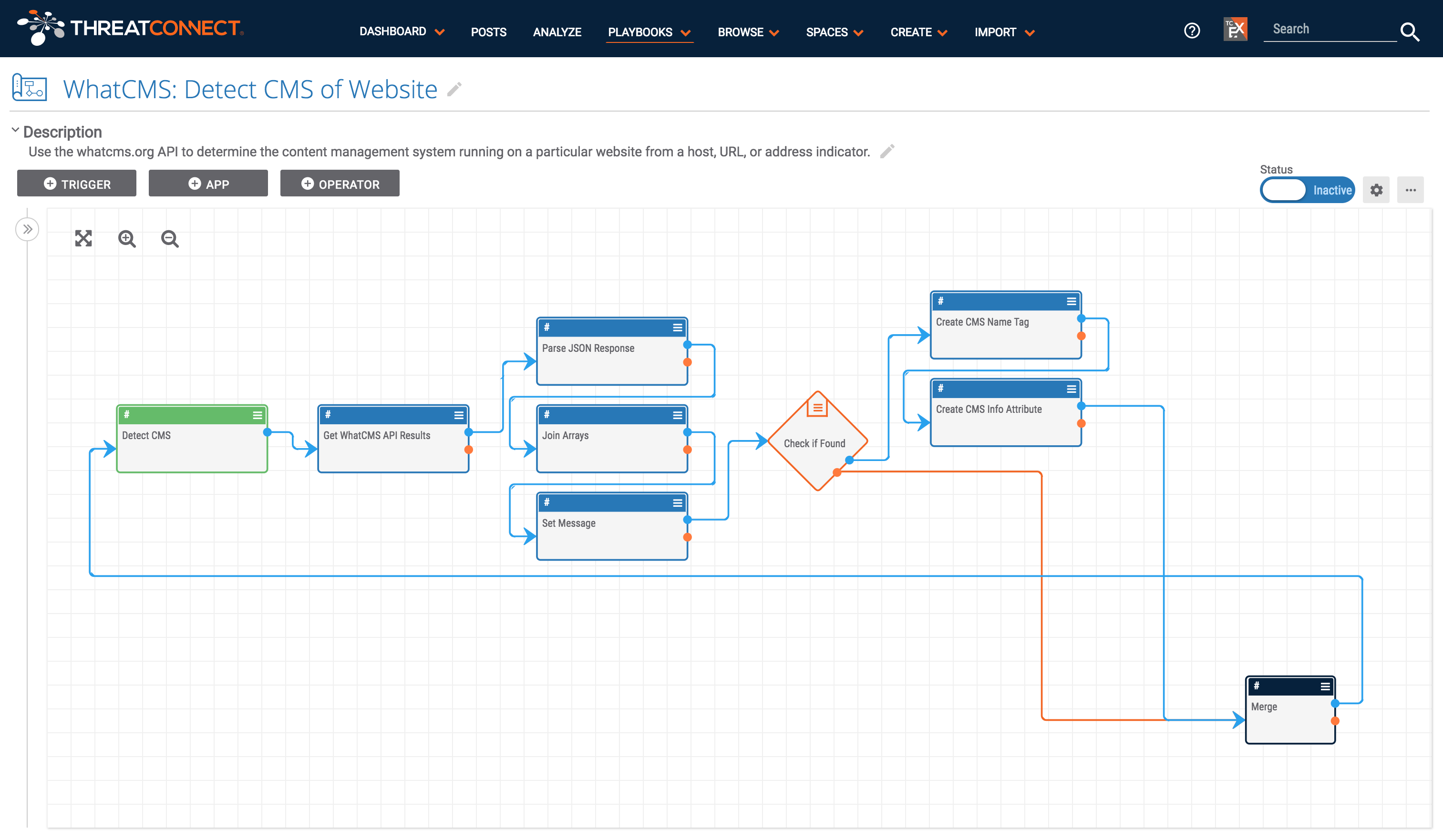
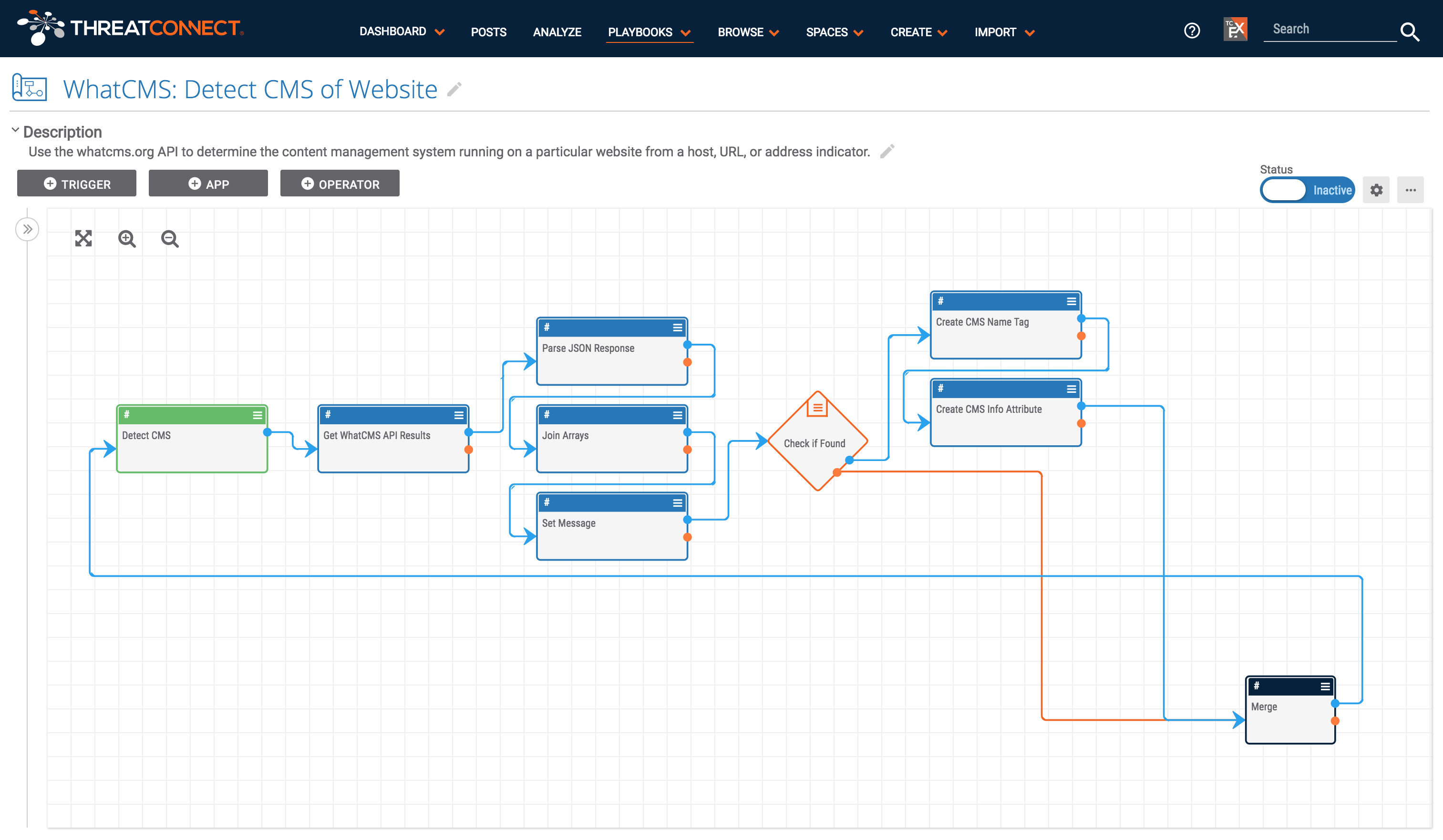
Determining the CMS (Content Management System) being used by a particular website is an important part of incident response and threat hunting. Incident responders are concerned with what CMS is being used because this gives clues into why a compromised site has been compromised. Certain CMSs are vulnerable in specific ways and identifying the CMS used on a site is a good place to start when investigating a compromised site. Knowing the CMS is also helpful when threat hunting as the directory structure of a site differs depending on the CMS. If an analyst is hunting for phishing or malware kits that have been installed on a site, knowing where to look decreases the time it may take to hunt for kits.
This Playbook makes it easy to find a website’s CMS using the WhatCMS API, saving time and effort. This playbook is triggered by a User Action trigger which shows up for URL, Host, and Address indicators. If one wants to determine the CMS in use by a website, just click the “Detect CMS” user action button. If the WhatCMS API returns successful results, a tag and an attribute with the name of the CMS will be applied to the indicator. The tooltip that appears once the process is complete also includes a link to refresh the indicator’s details page so that the user is able to view the new enrichment.
Installing the Playbook
To install the playbook, download WhatCMS_ Detect CMS of Website.pbx from our github repository (https://github.com/ThreatConnect-Inc/threatconnect-playbooks/). Then import it into ThreatConnect from the “Playbooks” page. When importing the app, you will be asked to provide your WhatCMS API key (for which you can register here). This will be stored in ThreatConnect as a Keychain variable and can be used in other ThreatConnect apps and playbooks (you can read more about variables in section 5 here).
Once you have installed the playbook, it would be helpful to walk through the playbook as done in the video below, so you can get an idea of what the playbook does.