Posted
With expanding attack surfaces and rising burnout, aligning executives and security teams is more critical than ever. The Intel Hub transforms that alignment into decisive action.
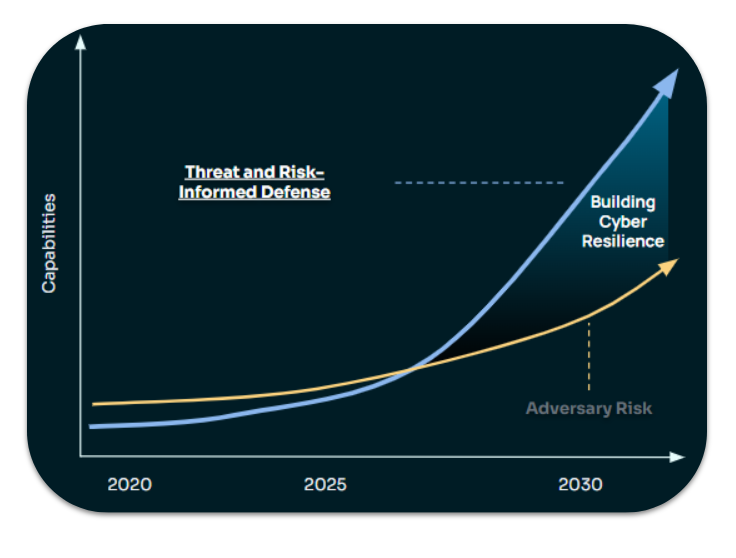
For years, cybersecurity teams have fought an asymmetric battle. Threat actors only need to succeed once. Defenders must succeed every time. But the rules of this game have changed – and the gap between attacker capability and defender capacity is widening at an alarming pace.
How alarming? Consider this jar of moldy rice.

There are 700ml of rice and 2ml of mold. The mold grows at a rate of 25% per day. We can chart this and see that after 3 weeks, the jar is 25% full of mold.
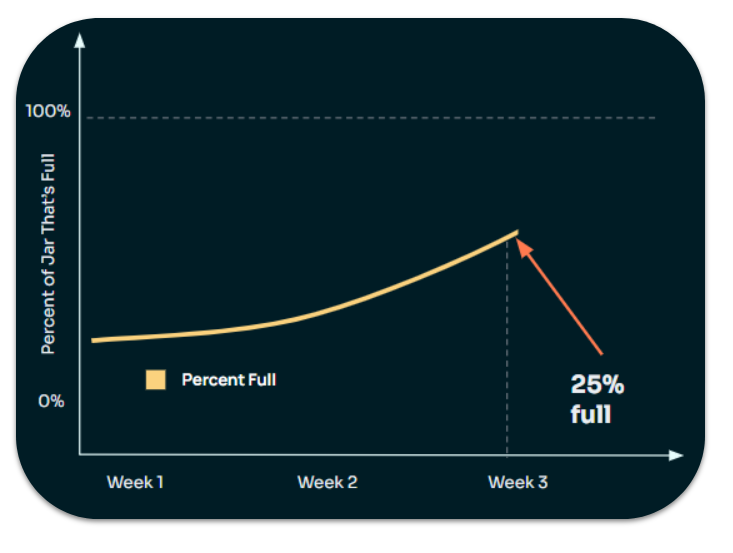
When will the jar be 100% filled?
A – Week 12
B – Week 24
C – Week 4
D – Week 8
The answer is C. It took 21 days from the start to get to 25%, but only 25 days to get to 50% and only 27 days to get to 100%. So the mold is chugging along at what looks like a mostly linear rate, but then: BAM!
That’s exponential growth. That’s a tipping point. And that’s exactly what’s about to happen in cyberdefense.
The data tells the story clearly. Exploitation of vulnerabilities as an entry point has grown 180% year-over-year [Verizon DBIR]. Supply chain breaches are up 68% [Verizon DBIR].
Internal threats have risen by 75% [Verizon DBIR], and the attack surface is exploding – cloud spend is projected to reach $2.4 trillion by 2030 [Forbes Business Insights], IoT devices will double [IoT Analytics], and the number of remote workers has tripled [WFH Research]. Meanwhile, security budgets and staffing are growing linearly at best, with a 4.8 million person cybersecurity workforce gap [ISC²] and 47% of organizations facing cutbacks [ISC²].
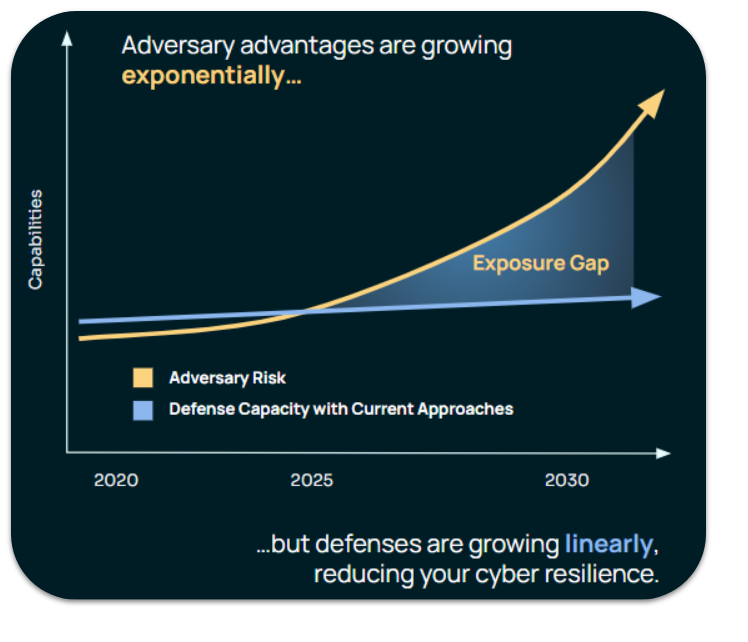
We are approaching a tipping point where incremental improvements are no longer enough. Cyber resilience demands a step change in how we align intelligence, risk, and operations.
That’s where the ThreatConnect Intel Hub comes in.
The Problem: Fragmented Insights, Linear Defenses
Security operations teams today face four systemic challenges that drain capacity, undermine morale, and leave the organization exposed:
- Lack of Prioritization
55% of teams admit to missing critical alerts because they couldn’t distinguish what mattered most [Mandiant – Global Perspectives on Threat Intelligence]. The flood of data means that many analysts default to firefighting, leaving high-impact threats unaddressed. - Lack of Context
84% of analysts worry about missing threats due to data overload [Crowdstrike Global Security Attitude Survey], and 82% report visibility gaps [Bedrock Security]. Without context, every decision carries more uncertainty, false positives rise, and investigation time grows. - Lack of Actionability
Investigations stall. Alerts linger for days. Lessons learned rarely loop back to improve defenses. In fact, 85% of Known Exploited Vulnerabilities remain unremediated after 30 days [Verizon DBIR]. - Disconnected Tools and Workflows
Siloed systems and legacy TIPs mean critical intelligence isn’t where teams need it, when they need it. Burnout is rampant – 84% of analysts report feeling burned out [1Password], and 70% say alert volume affects their personal lives [CISO Magazine]. The 2025 SANS SOC Survey reinforces this point — 62% of SOC leaders say their organization isn’t doing enough to retain staff [SANS SOC Survey]. CISOs increasingly frame burnout as a “capacity management” problem, recognizing that sustained overload translates directly into business risk.
These problems aren’t solved by adding more data feeds or point solutions. They’re solved by unifying the workflows, context, and prioritization that enable defenders to act decisively.
The Intel Hub: A Threat and Risk-Informed Defense Platform
The ThreatConnect Intel Hub unites threat intelligence, cyber risk quantification, and security operations in a single platform designed to do three things exceptionally well:
- Contextualize: Deliver high-fidelity, business-relevant threat context at the moment of need, grounded in AI-curated intelligence requirements and enriched with collective analyst insights.
- Prioritize: Focus teams on threats and vulnerabilities with the highest business risk and potential financial impact.
- Automate & Operationalize: Enable teams to act fast, adapt confidently, and continuously improve by embedding intelligence directly into operational workflows.
This isn’t just about knowing your threats. It’s about knowing which ones matter most to your organization right now – and having the means to address them without delay.
Closing the Exposure Gap
The Exposure Gap is the widening distance between the speed and sophistication of adversaries and the linear pace of most defensive improvements. Closing it requires more than just detection. It requires decision advantage – the ability to get the right intelligence to the right place at the right time, tied to business risk.
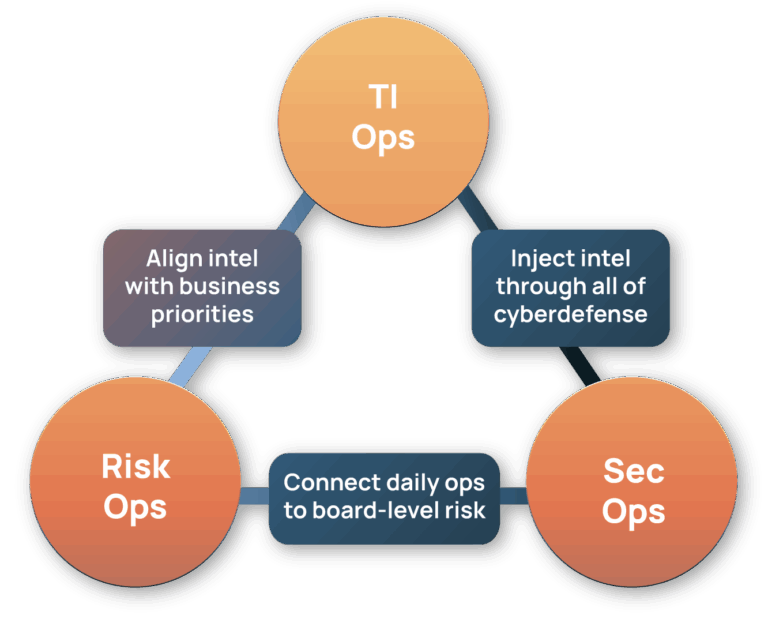
The Intel Hub closes this gap by aligning three essential capabilities:
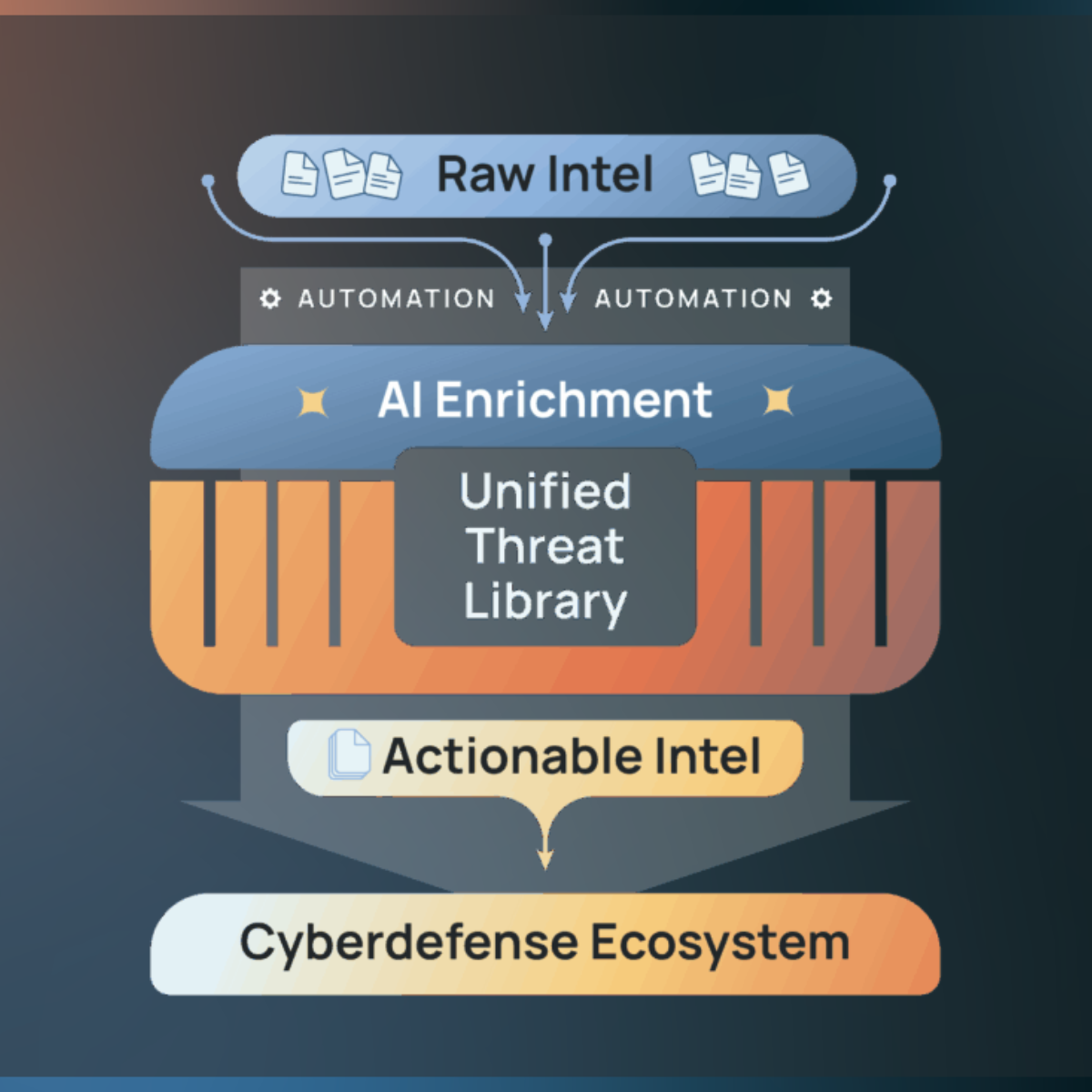
1. Operationalizing Threat Intelligence with TI Ops
TI Ops goes beyond centralizing threat data. It operationalizes it – defining intelligence requirements, enriching data with AI, mapping threats to MITRE ATT&CK, and distributing relevant intelligence directly to SOC, IR, Hunt, and Vulnerability Management teams.
The latest SANS CTI Survey shows progress here: business units and executives are now more involved in defining intelligence requirements than ever before, setting the stage for true SOC–business alignment [SANS CTI Survey]. This collaboration ensures intel relevance and makes ROI easier to prove.
- AI-curated requirements filter noise.
- ATT&CK gap analysis highlights control gaps.
- Frictionless dissemination ensures intel is in the right hands instantly.
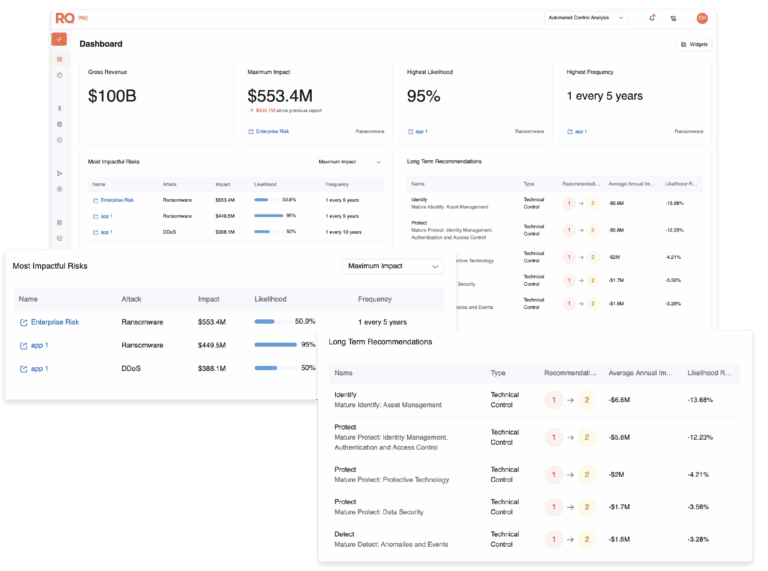
2. Quantifying Cyber Risk with Risk Quantifier (RQ)
RQ translates cyber risk into financial terms that executives understand. By modeling threats, vulnerabilities, and controls against potential business impact, RQ drives defensible prioritization and justifies investments.
- Dynamic, intel-driven risk scenarios replace static assessments.
- Financially-backed prioritization guides resource allocation.
- Executive-ready reporting bridges security and business language.
3. Accelerating SecOps with Polarity
Polarity delivers intelligence directly into any tool without integration work, enabling analysts to get the full context without breaking workflow.
- Contextual federated search spans 200+ tools and feeds.
- AI summaries condense complex threat data into actionable insight.
- Playbook-driven automation executes from within the overlay.
Real-World Impact
ThreatConnect customers are already proving the model works:
- A Forbes 2000 hospital & healthcare system reduced incident response time from 7 hours to 37 minutes [Forbes 2000 Hospital & Healthcare System] – and it’s still dropping.
- A major social media platform cut time to close by 300% the month they implemented Polarity [US Head of Threat Management & Incident Response; Major Social Media Platform].
- A Fortune 100 insurance provider uses ThreatConnect to identify the most critical threats based on business impact [Fortune 100 Insurance Provider].
- A global manufacturer describes Polarity as saving “humans worth of time” by increasing utilization of their threat intelligence [Fortune 500 Global Manufacturer].
In aggregate:
- 98% of customers say ThreatConnect is critical to their operations
- 97% report improved effectiveness of tools like SIEMs, SOARs, and EDRs
- 90% see time savings over 50%
- 67% report more than 50% reduction in MTTR
- 63% have reduced false positives
- 79% say collaboration between teams improved
Why Now?
The urgency comes down to three converging pressures:
- Attack Complexity Is Skyrocketing (Thanks, AI!)
AI-assisted phishing can cut attacker costs by 95% [Harvard Business Review], 40% of business-targeted emails are now generated using AI [VIPRE Security Group Email Threat Trends], and over 57 nation-state-aligned threat actors are already using advanced AI tools [Google Threat Intelligence Group]. - The Attack Surface Is Expanding Relentlessly
Every dollar of cloud spend, every new IoT device, and every third-party connection adds another potential entry point. More vulnerabilities were reported in 2024 than in any year prior – up 30% over 2023 [SC Magazine]. - Defensive Capacity Isn’t Keeping Pace
Even if budgets grow, the workforce gap and burnout rates mean you can’t simply throw more people at the problem. 84% of security professionals report feeling burned out [1Password], and 70% say alert volume impacts their personal life [CISO Magazine].
The SANS SOC Survey makes the link explicit: reducing burnout is a form of risk mitigation because lower turnover preserves capacity and shortens dwell time [SANS SOC Survey].
And there’s one encouraging shift: according to the 2025 SANS CTI Survey, business units and executives are now more involved in defining intelligence requirements than ever before [SANS CTI Survey]. This growing cyberdefense–business alignment means security teams can focus collection and analysis on the threats that pose the highest business risk — making every defense dollar and analyst hour count. It’s a sign the industry is finally bridging the gap between operational needs and strategic priorities.
How the Intel Hub Delivers Decision Advantage
The Intel Hub turns fragmented security efforts into a cohesive, adaptive defense posture by:
- Connecting business priorities to frontline workflows so every SOC alert, every vulnerability scan, every hunt operation is informed by business impact.
- Enabling continuous improvement through feedback loops between detection, intel, and risk, ensuring lessons learned lead to stronger defenses.
- Providing AI-curated intelligence requirements that evolve with the threat landscape, ensuring relevance without overwhelming teams.
- Embedding risk quantification into operational priorities so resources go to the most impactful threats, not just the loudest alerts.
- Integrating without adding tool fatigue – context appears where analysts are already working, in any tool, with no integrations required.
For Every Role in the Cyber Defense Chain
- CISOs gain the ability to quantify risk, justify spend, and report outcomes in clear business terms.
- VPs of Cyber Defense can unify operations, intelligence, and risk to reduce MTTR and manage burnout.
- CTI Directors can prove the business value of intelligence while streamlining dissemination.
- SOC Analysts & IR Teams get the right context instantly, cutting through false positives and accelerating triage.
- Threat Hunters & Detection Engineers can focus on what actually threatens the business.
The Bottom Line
The ThreatConnect Intel Hub isn’t just another security product. It’s the connective tissue that unites threat intelligence, risk, and operations into a living, evolving defense capability. It’s how you:
- Contextualize every decision with high-fidelity, business-relevant intel.
- Prioritize based on real financial impact.
- Automate & operationalize action without adding complexity.
The threats aren’t waiting. The attack surface isn’t shrinking. The workforce isn’t magically doubling. The time for an Intel Hub – for connecting intelligence to action in a way that actually keeps pace with the adversary – is now.
Stop mold in its tracks: schedule a demo today.
