Posted
Blog authored by Dave DeWalt, Founder and Managing Director, NightDragon. Read it on the Night Dragon’s website here
We live in a true golden age of data and information. Organizations have more threat intelligence, whether it be cyber, physical, etc, at their fingertips than ever before, from vulnerabilities to adversary profiles and more. Inside these stores of intelligence lies the opportunity for stronger, more resilient, and more responsive cyber and physical security. It’s truly a big data opportunity.
However, as with every many opportunities, it also creates new challenges. Of those millions of intel data points and alerts funneled into the organization from a variety of sources, which are the ones that matter to you? How do specific threats impact the risk profile of your business? How do you translate knowledge of a threat or threats and turn that into operational defense and protection? In short, what do you DO with all that threat intelligence, and how do you operationalize it? This is a challenge facing every CISO, security leader, and risk manager I talk to today.
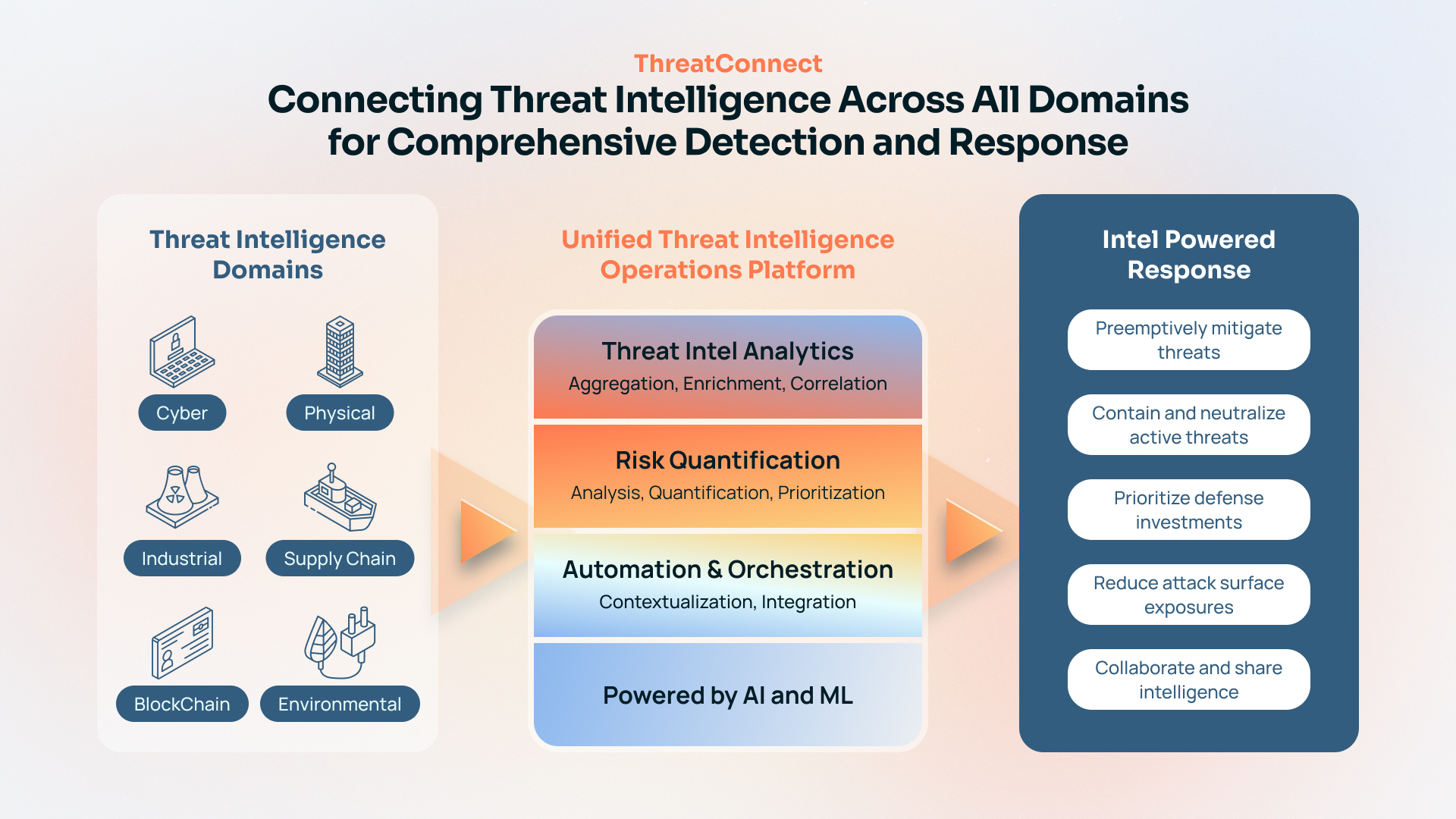
Over the last few years, it has become more and more evident that we need to unite our threat and risk intelligence across all domains, such as Cyber, Physical, Supply Chain, Industrial, BlockChain, and more. Allowing seams in our security and safety operations can cause longer response times, less efficacy, and significantly more cost and risk.
We have seen the impacts of this breach after breach, incident after incident. Ransomware, for example, can cause physical damage as well as digital and cyber damage. Physical threats such as floods, storms, accidents, and even outright war can cause risk and damage to digital systems. The attack on Colonial Pipeline is a perfect example of this, with a digital ransomware attack causing physical impacts to fuel supply chains.
Today, security teams primarily rely on cyber threat intel sources Mandiant, Crowdstrike, Recorded Future, and others, while other teams like OT security and physical security rely on other threat intel sources to make decisions and prioritize risk. NightDragon sees a world where a single platform can serve as a connective tissue to all intelligence gathered from the world’s best researchers and threat intelligence sources, whether it be cybersecurity, physical security, related to critical infrastructure, or supply chains. The time to fuse our Intelligence is NOW. The time to measure each indicator with quantifiable risk is NOW. The time to build integrated playbooks and workflows across all threat domains in NOW.
A Unified Threat Intelligence Operations Platform not only helps aggregate the increasing volume and variety of intel data but also confidently prioritize, manage, and respond to threats using automation and quantitative risk insights.
This is why I am excited to announce that NightDragon has partnered with ThreatConnect, maker of leading threat intelligence operations (TI Ops) and risk quantification solutions. ThreatConnect’s platform centralizes the aggregation and management of all the threat data relevant to CISOs and security operations teams, then turns that threat intelligence into actionable insights, captures and applies analyst knowledge for additional context, and layers a risk quantifier to measure cyber risk in monetary terms. It then allows teams to orchestrate and automate processes to respond faster and more confidently than ever before.
CEO Balaji Yelamanchili and I share this vision for a single platform to serve as a connective tissue between all the various threat intelligence feeds that CISOs leverage today. I have known Balaji for 25+ years since I was CEO of Documentum. While we may have served on what some might call opposite sides of the table in the years since – him on Team Yellow at Symantec and me on Team Red as CEO of McAfee – I am thrilled to now reunite with him to make this vision a reality.
NightDragon will partner with ThreatConnect to help launch the company into its next phase of growth and accelerate this shared vision of a connected view of threat intelligence. We will put the power of our NightScale platform to work with ThreatConnect, providing the team with the people, partnerships, playbooks, and programs needed to grow and scale. As part of this partnership, I will also be joining the Board of Directors of ThreatConnect as Non-Executive Chairman.
Given its platform and market traction, ThreatConnect is well-positioned to be the threat intelligence platform that serves as this connective tissue. The team’s platform accomplishes much of this today, and the organization has already seen incredible momentum, including more than 200 enterprises and thousands of security operations professionals who already rely on ThreatConnect every day to protect their most critical systems. I believe this can and will be done. It needs to be done. Connect the Threat with ThreatConnect.
We look forward to working with the entire ThreatConnect team to bring our shared vision into reality. Together, we will change how CISOs and security leaders are able to tap into the power of threat intelligence from every source and, as a result, better protect their organizations for many years to come.
About the Author
Dave DeWalt is Founder and Managing Director of NightDragon, a late-stage and growth venture capital firm focused on the cybersecurity, safety, security, and privacy market. He is a veteran CEO, advisor, and investor who has led companies, from startups to the Fortune 500, on a transformational journey of success. Focused on technology and cybersecurity, Dave helped create more than $20 billion of shareholder value during his 15-plus years as President and CEO of three major companies. That includes driving the largest cybersecurity IPO to date as of 2013, and leading the largest all-cash deal in technology history as of 2010. Today, he serves as Managing Director of Allegis Cyber as well as investor and board member in the world’s most innovative companies such as Delta Airlines, Five9, Forescout, Phantom Cyber, Claroty, Team8, DataTribe, Illusive Networks, and Optiv.