Posted
How to use historical intelligence to get back to the future and defend your organization
We need to talk about something.
In the history of this blog, we’ve never discussed Back to the Future. It’s crazy to think that that’s the case as arguably the second-greatest sci-fi trilogy is rife with quotable lines and meme-able scenes that would make for amazing blog fodder. We have to say that we love the Back to the Future trilogy. Despite it essentially being the same movie three times, each one is memorable, full of iconic moments, solid special effects that have stood the test of time, and fun plots. You may be asking, “what is the point and what does any of this have to do with cyber threat intelligence?” Well, the point is that instead of being the villain (more on that to follow), Marty McFly should have learned from his family’s past adversities and adversaries to affect change in his life and prepare for future conflicts and incidents. This same struggle plays out daily in the cyber intelligence world: how do we use historical intelligence to get back to the future and defend our organization?
We argue that the utility of historical intelligence persists long after its indicators have been deprecated and actors no longer use them in operations. If we go back in time, we can learn things about our adversaries that will help prepare us for dealing with them in the present and future. With that in mind, for this post we went back in time to review Fancy Bear/ APT 28/ Sofacy’s use of a SSL certificate and identify whether there is anything we could use to figure out what they are doing now.
But first we need to level-set.
Delorean Diatribe
Nobody ever talks about it, so we’re going to talk about it. There’s something that you need to consider before we go any further: Back to the Future’s “protagonists” Marty McFly and Doc Brown are in fact the film’s villains, and Biff Tannen, although flawed, is the failed hero. The films do a great job of displaying Marty and Doc’s personal struggles and pairing those with the struggles of their past and future selves and families, but glosses over the fact that they are only able to confront those issues by way of a world-altering technical capability. Further, those McFly family struggles come from their own inabilities to cope with their surroundings and derive strength from their adversity.
On the other hand, Biff’s past, present, and future selves have effectively coped with their environments and found a way forward through adversity that didn’t involve God-like capabilities. While he may be a bully and a criminal, Biff only uses the Delorean to help out his past self after Marty and Doc use it multiple times to not only help out their families but also deteriorate Biff’s standing in the world.

As further evidence to our theory, in most notable sci-fi movies (Star Wars, The Matrix, Independence Day, Blade Runner, and The Terminator all come to mind) the antagonists are on the side with the technical superiority that gives them an upper hand in suppressing or fighting the protagonists. Regardless of their intentions with their use of the Delorean, Marty and Doc have the most technologically advanced device in the world and use it to their own benefit and thus, the detriment of others. Most heroes with such a superior capability would recognize the disadvantage to others and attempt to find peace with or better their adversary. Instead, Marty and Doc push Biff to his own manure-laden demise without offering him any symbiotic alternative that would positively impact all those affected by the Delorean’s time-altering wake.
In the end, naysayers to our theory will argue that Marty and Doc instilled some sort of space/time continuum justice against Biff and that all is right in the world. We’re not arguing that what Biff did was okay — certainly bullying, assault, and fraud are all horrible things for which there should be punishment — and the justice system provides avenues for addressing those crimes. But what Marty and Doc did was so much more despicable — with a capability that has no justice system-equivalent oversight — that they instead should be considered the villains.
Fancy Bear SSL Certificate acts as the Delorean
Whoa, that was heavy, but now let’s explore how we can avoid Marty’s pitfalls by reviewing historical intelligence on Fancy Bear to better defend against them now and in the future. In our last article, we reviewed Fancy Bear’s use of a self-signed SSL certificate (a1833c32d5f61d6ef9d1bb0133585112069d770e) and the infrastructure associated with it to derive their previously unidentified hosting and registration tactics. We then looked for recent infrastructure consistent with those tactics that could potentially be associated with Fancy Bear. Researcher Mark Parsons identified some of the historical use of this SSL certificate and its association to Fancy Bear attacks. Unfortunately, through our previous research, we were only able to identify Fancy Bear tactics based on current use of the SSL certificate.
In reviewing PassiveTotal (or RiskIQ) for the SSL certificate’s hash, we saw that it captured historical associations between the certificate and the IPs it was used on. PassiveTotal lists a total of about 40 IPs that have been associated with the SSL certificate.
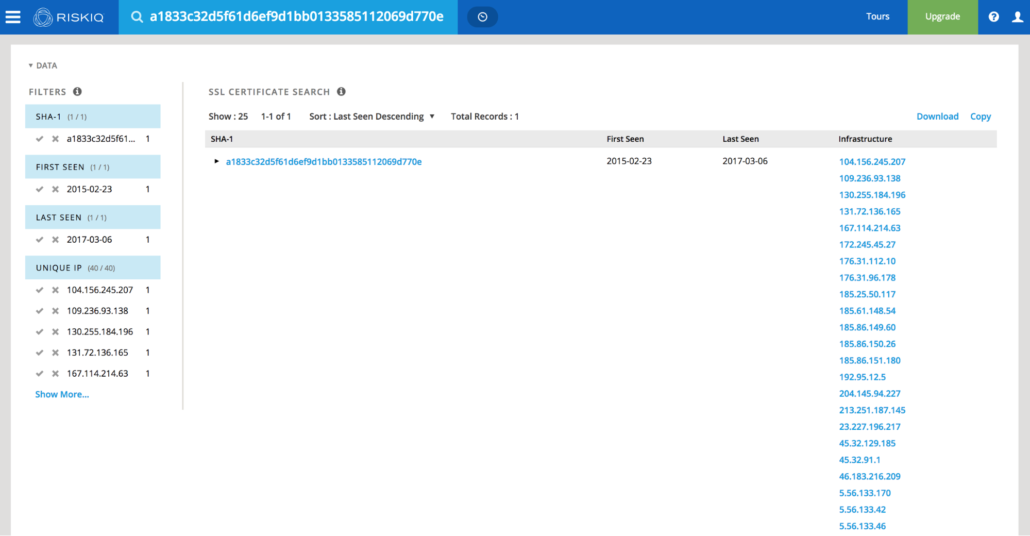
Investigating these IPs within PassiveTotal, we got an idea of the general timeframe in which the SSL certificate was associated with the IP address. This is important because we were able to use this timeframe to identify the domains that were hosted on those IPs during the same timeframe and thus may be associated with Fancy Bear. In some cases, as shown below, this timeframe dates back to 2015.
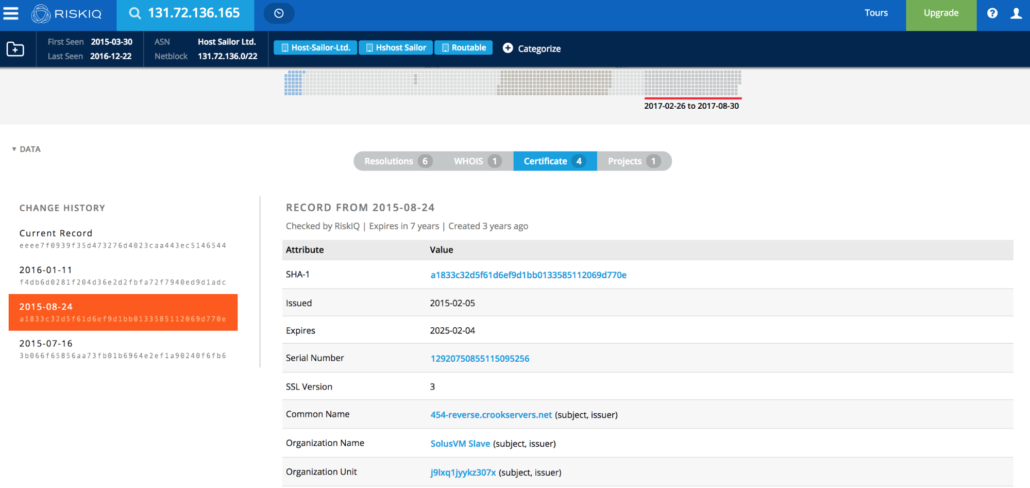
Once we had a timeframe for the association between the domain and IP, we used ThreatConnect’s Farsight DNSDB integration to build out the infrastructure that may be associated with Fancy Bear. As shown below, the domain vvorthyhands[.]org was hosted on the 131.72.136.165 IP address during the time when that IP was associated with the Fancy Bear SSL certificate (8/24/2015).
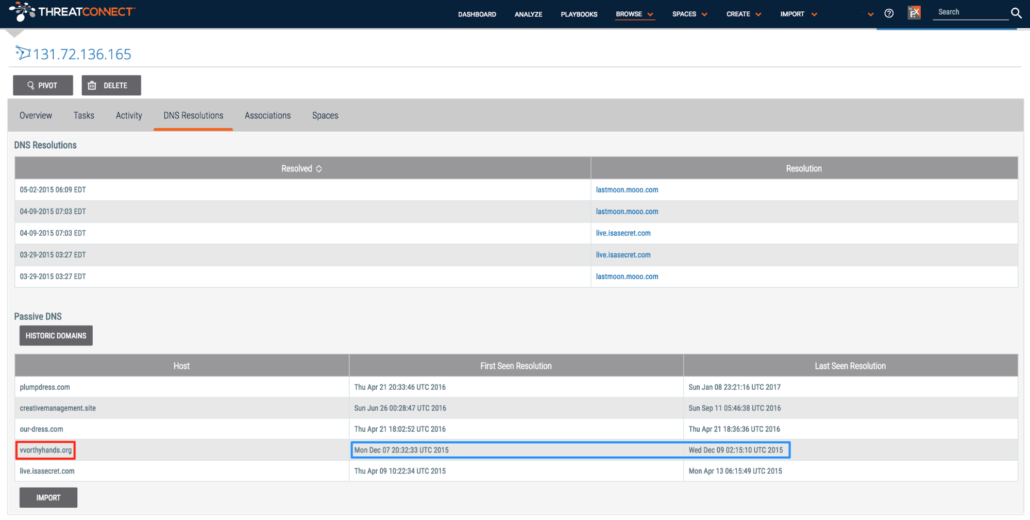
Running through this for all of the IP addresses identified using PassiveTotal, we came up with the below list of domains. It should be noted that in some cases, we were unable to include domains because of a lack of specificity in the timeframe in which the IP was associated with the SSL certificate.
| IP | Domain | Create Date | Registrant Email Address |
| 130.255.184.196 | adobeincorp[.]com | 10/25/12 | rvanholsted@yahoo.com |
| 131.72.136.165 | vvorthyhands[.]org | 9/5/13 | Private / fradmantisun@mail.com |
| 167.114.214.63 | tukangcendol-naikinbuhaji[.]com | 7/31/15 | PamelaBeauty213@hotmail.com |
| 185.25.50.117 | bmwriting[.]com | 11/16/16 | emiliorojas@mail.com |
| 185.86.151.180 | trbusinesslink[.]com | 6/13/17 | Private |
| 213.251.187.145 | mailpho[.]com | 10/9/14 | emmer.brown@mail.com |
| 213.251.187.145 | qov[.]al |
7/19/14 | NA |
| 45.32.129.185 | misdepatrment[.]com | 3/22/16 | frank_merdeux@europe.com |
| 62.113.232.196 | uniquecorpind[.]com | 10/25/16 | yasiner@myself.com |
| 86.105.1.136 | securelink1[.]org | 6/28/16 | domainhosting@tuta.io |
| 89.45.67.12 | cvvshop[.]lv | 2/15/13 | albert1408@live.com |
| 89.45.67.12 | googlegoogie[.]com | 4/14/17 | parpale@inbox.lv |
| 89.45.67.12 | zimbra-service[.]org | 3/1/16 | js_69tt@india.com |
| 89.45.67.12 | zimbra-servicing[.]com | 6/7/16 | kohler.yoh71@hotmail.com |
| 92.114.92.102 | networkschecker[.]com | 2/28/17 | Private |
| 92.114.92.102 | networkschecker[.]net | 5/12/17 | edvard_jozef@centrum.cz |
| 94.177.12.157 | netcorpscanprotect[.]com | 12/20/16 | ernesto.rivero@mail.com |
| 94.177.12.74 | zpfgr[.]com | 12/9/16 | olavi_nieminen@suomi24.fi |
| 95.215.44.38 | netcloselysecure[.]org | 11/8/16 | jesddin@europe.com |
Many of these IP and domains were previously identified for their association to Fancy Bear attacks in various industry reports. Several of the domains date back to 2016, while one of them dates back to 2012. These domains have been shared in Incident 20170918A: Infrastructure with Historical Ties to Fancy Bear SSL Certificate.
Okay, we’re back in 1955, now what?
At this point, we’ve successfully used the Fancy Bear SSL certificate to travel back in time and identify some older domains that we can most likely associate with Fancy Bear activity. We could also have employed some of the methodologies that we’ve previously described to identify these older domains and proceed from there. But we had these domains, so we reviewed their historic WHOIS registration and hosting information to identify how the actors behind them went about registering those domains.
We imported the identified domains into ThreatConnect to further review them for registration and hosting tactics. Using our DomainTools Spaces App, we reviewed the WHOIS history for those domains and identified the email addresses used to register them, name servers they used, and any other pertinent registration information.
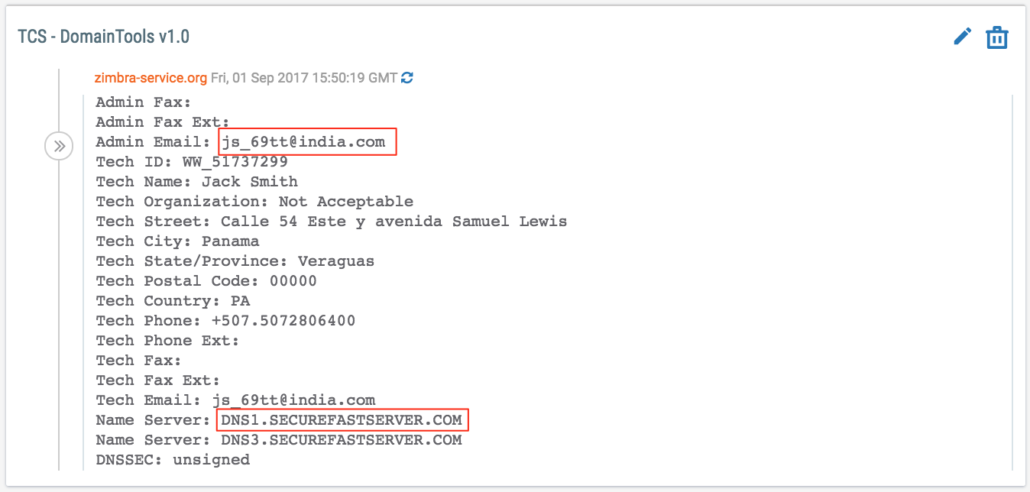
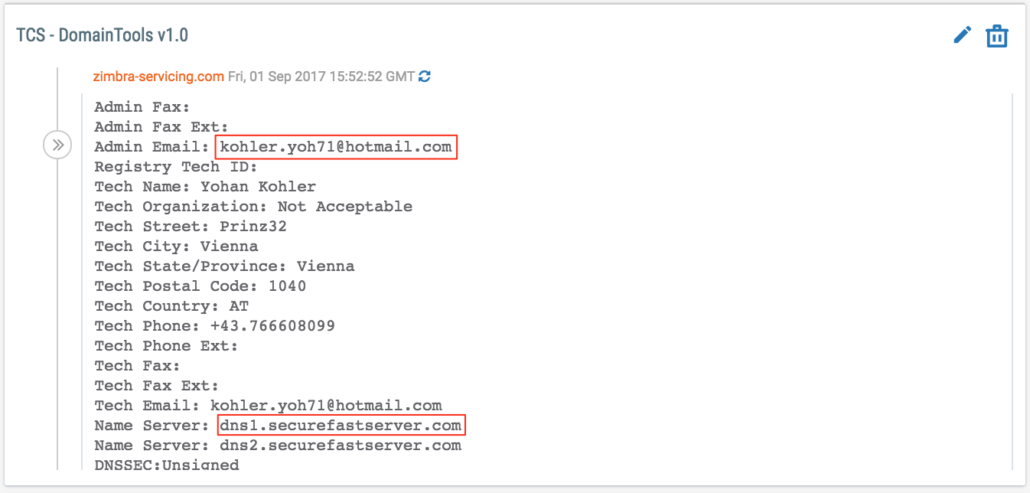
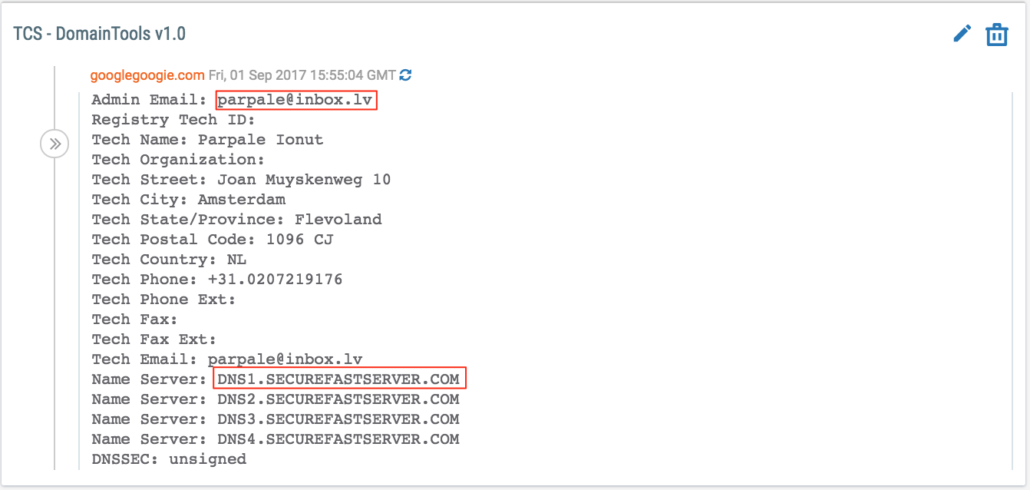
After reviewing those previously identified domains, we found that several of them — including uniquecorpind[.]com, bmwriting[.]com, and zpfgr[.]com — use ITitch, Carbon2u, and BAcloud name servers that we previously looked into while researching Fancy Bear infrastructure. However, we saw that several of these domains — including zimbra-service[.]org, zimbra-servicing[.]org, and googlegoogie[.]com — use Qhoster’s securefastserver.com name server.
So now that we identified the use of securefastserver[.]com name server as a possible tactic that Fancy Bear is employing, we reviewed historical registrations involving the securefastserver[.]com name server to determine whether Fancy Bear used it consistently.
Consistencies in Tactics?
QHoster is an infrastructure reseller operating out of Bulgaria. Currently, about 820 domains currently use QHoster’s securefastserver[.]com name servers while at least 11,900 domains use QHoster’s other name server qhoster[.]net. This differs from other name servers or registration services that Fancy Bear has also used, such as ititch[.]com, bacloud[.]com, and nemohosts[.]com, that aren’t as widely used. These previously identified services have a smaller volume of domains that have been registered or hosted through them — typically less than 2,000 domains and in some cases less than 1,000. Because QHoster is more widely used than some of the other registration services Fancy Bear uses, we have a lower confidence in the infrastructure that we identified based on registration tactics alone.
That being said, we started off by getting an idea of how often Fancy Bear used QHoster’s registration services/name server and the specific email domains that they’ve used when registering domains through QHoster. The hope was that this could identify those email domains that we want to be on the lookout for when reviewing securefastserver[.]com name server domains now and in the future. First off, we used the Reverse WHOIS capabilities from our friends at DomainTools to identify current and historical domains that used the securefastserver[.]com name servers.
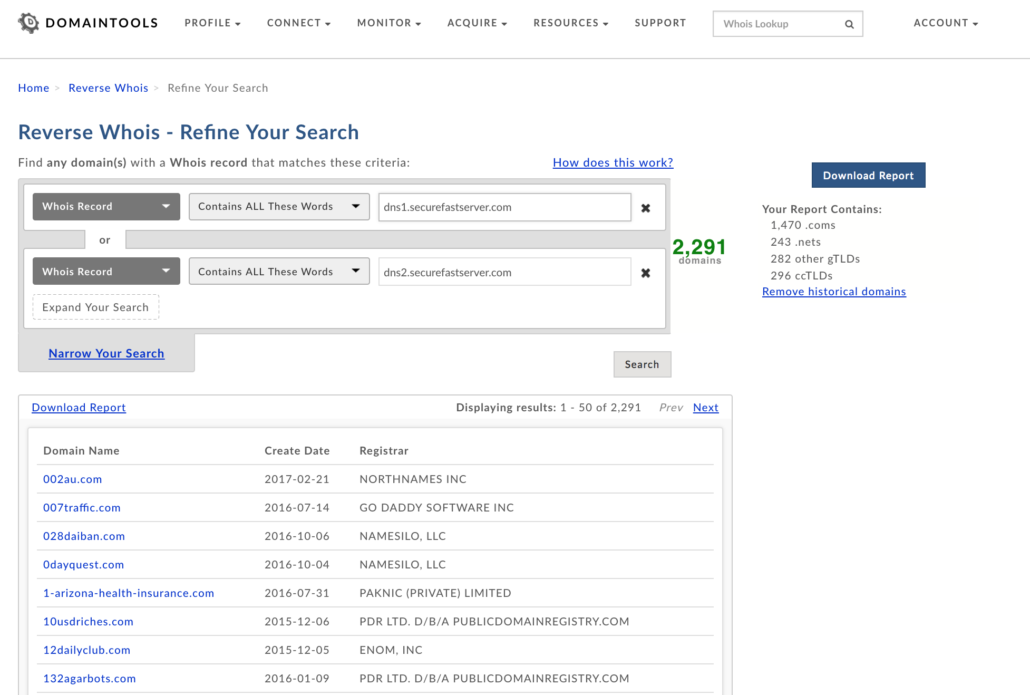
We then took the generated report from the Reverse WHOIS search and put those domains into ThreatConnect’s Analyze function. In doing so, we were able to see which domains ThreatConnect already knew about and ultimately identified those securefastserver[.]com domains that were associated with Fancy Bear but may not have been hosted at an IP with the Fancy Bear SSL certificate. When intersections with known bad are identified using Analyze, it is invaluable for network defenders. It also justifies research efforts like those described here, or quickly augments understanding of experienced activity.
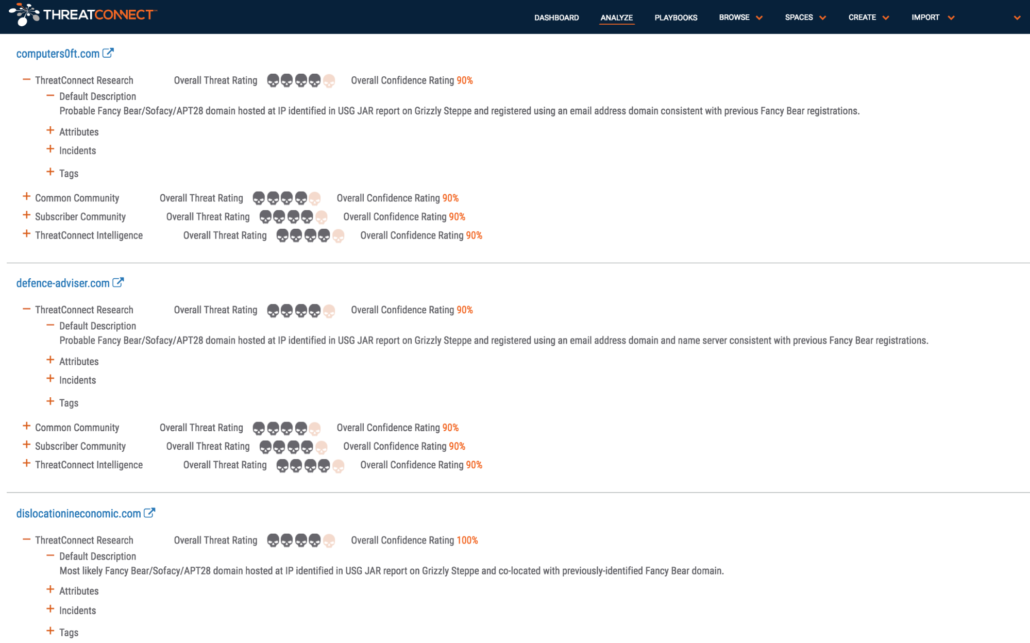
Several of the domains were associated with Fancy Bear by way of our research into the GRIZZLY STEPPE report while others were identified in a report on Fancy Bear (APT28) targeting the German Parliament. Using the WHOIS History in our DomainTools Spaces App, we identified the create date and original registrant email address for these domains.
| Domain | Create Date | Registrant Email Address |
| iscellane[.]org | 6/13/15 | th.kais@yahoo.de |
| mail-account-yahoo[.]com | 7/13/15 | pirat@iname.com |
| us-mg6-mail-yahoo[.]com | 7/13/15 | pirat@iname.com |
| edit-mail-yahoo[.]com | 7/28/15 | lary@asia.com |
| outlook-security[.]org | 10/15/15 | k.pavuls@yahoo.com |
| security-ukr[.]net | 12/7/15 | pirat@iname.com |
| web-privacy-guardian[.]com | 12/21/15 | labbylusak@mail.com |
| highcomission[.]org | 1/15/16 | brown_pool@india.com |
| uzbekistan-mfa[.]com | 1/29/16 | kad_75isl@india.com |
| defence-adviser[.]com | 4/7/16 | juh.rss@mail.ee |
| computers0ft[.]com | 5/25/16 | Lien.Jo@mail.com |
| dislocationineconomic[.]com | 10/13/16 | Isac.Blomqvist.free@mail.com |
Coupled together with the other securefastserver[.]com domains that we identified earlier through the SSL certificate research, we saw that Fancy Bear most likely has used the securefastserver[.]com name server since at least mid-2015. Additionally, several of the domains use 1&1 email domains mail.com, asia.com, and india.com, while others use more common email services like Yahoo and Hotmail. Now the key question is “how do we get back to the future” and apply the lessons learned from the past to proactively inform defensive efforts in the present?
Tracking Back to the Future
Those domains using a securefastserver[.]com name server and most likely associated with Fancy Bear were registered from at least June 2015 to April 2017. This timespan suggests that Fancy Bear regularly uses QHoster’s securefastserver[.]com name servers and registration/hosting services. To that end, we could have potentially exploited this historical tactic to identify current Fancy Bear infrastructure, or proactively identify it in the future.

For this research, we focused on those registration tactics that are most unique within the subset of domains that we previously identified. We began by doing a search in DomainTools’ Iris for any domains using the securefastserver[.]com name server that were registered using some of the less common email domains and created since the beginning of 2017.
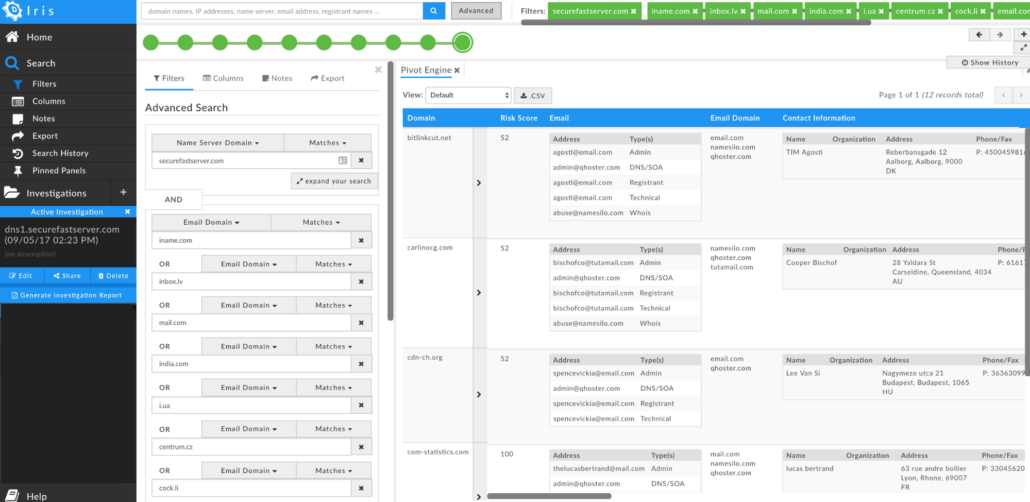
We then reviewed the results from that search to identify those domains that are hosted on dedicated servers — another tactic that Fancy Bear has consistently employed. This gave us the nine domains below, of which three were registered more recently than the domains we identified in the SSL certificate research above. While the registration and hosting tactics do not definitively associate these domains with Fancy Bear, given those consistencies these domains merit additional scrutiny. These indicators have been shared in Incident 20170919A: Notable Securefastserver.com Name Server Infrastructure.
| Domain | IP | Create Date | Registrant Email Address |
| cdn-ch[.]org | 86.105.18.113 | 1/1/17 | spencevickia@email.com |
| jpoweradmin[.]com | 86.106.93.111 | 1/8/17 | keiyokoyama1990@mail.com |
| bitlinkcut[.]net | 89.45.67.189 | 2/12/17 | agosti@email.com |
| login-freemail[.]com | 86.104.15.105 | 2/17/17 | v.lebzyak@i.ua |
| events-spot[.]com | 46.102.152.172 | 2/28/17 | mathiasmartens1983@mail.com |
| carlinocg[.]com | 89.33.64.123 | 2/28/17 | bischofco@tutamail.com |
| gmail-google-accounts[.]com | 86.105.227.212 | 5/19/17 | tovarasuceausescu@inbox.lv |
| com-statistics[.]com | 86.105.1.111 | 5/24/17 | thelucasbertrand@mail.com |
| mailer-support[.]com | 89.37.226.120 | 8/15/17 | 375walker@india.com |
GREAT SCOTT! As it turns out, our friends at root9B, employing some different research techniques in proactively searching for Fancy Bear, identified the login-freemail[.]com domain through the use of “Coming soon” messages on the domain’s website. In researching Fancy Bear-associated domains, root9B identified that several of their splash pages used the address “522 Clematis. Suite 3000” in West Palm Beach, FL, and many also used the same phone numbers “866-593-54352” and “403-965-2341.”
By searching for these consistent strings against “Coming soon” splash pages, root9B was able to identify the following domains:
| Domain | IP | Create Date | Registrant Email Address | Name Server |
| akamaisoft[.]com | 86.105.1.102 | 12/16/14 | leesa92@chewiemail.com | MONOVM.EARTH.ORDERBOX-DNS.COM |
| cleanphonetrksftware[.]com | Not Hosted | 1/19/16 | Privacy Protection | DNS1.SECUREFASTSERVER.COM |
| appservicegroup[.]com | 46.102.152.132 | 10/19/16 | olivier_servgr@mail.com | NS1.CARBON2U.COM |
| ppcodecs[.]com | 62.113.232.197 | 10/19/16 | chpiost8n@post.com | NS1.CARBON2U.COM |
| apptaskserver[.]com | Parked | 10/22/16 | partanencomp@mail.com | NS1.ITITCH.COM |
| akamaisoftupdate[.]com | 89.45.67.20 | 10/27/16 | mahuudd@centrum.cz | NS1.CARBON2U.COM |
| applecloudupdate[.]com | Not Hosted | 11/4/16 | ll1kllan@engineer.com | NS1.CARBON2U.COM |
| joshel[.]com | 86.105.1.13 | 11/9/16 | germsuz86@centrum.cz | NS1.ITITCH.COM |
| noticermk[.]com | 95.215.47.162 | 11/24/16 | frfdccr42@centrum.cz | NS1.ITITCH.COM |
| runvercheck[.]com | 185.156.173.70 | 11/25/16 | cauel-mino@centrum.cz | STVL113289.EARTH.OBOX-DNS.COM |
| reportscanprotecting[.]org | 146.0.43.98 | 12/3/16 | abor.g.s@europe.com | NS1.CARBON2U.COM |
| gtranm[.]com | 89.42.212.141 | 12/14/16 | wee7_nim@centrum.cz | STVL113289.EARTH.OBOX-DNS.COM |
| evbrax[.]org | 103.41.177.44 | 1/10/17 | kern82@gmx.net | NS4.ITITCH.COM |
| acrobatportable[.]com | 95.215.47.226 | 1/12/17 | jul_marian@centrum.cz | STVL113289.EARTH.OBOX-DNS.COM |
| hotfixmsupload[.]com | Sinkholed | 1/13/17 | luca_dozi@myself.com | STVL113289.EARTH.OBOX-DNS.COM |
| lowprt[.]org | 86.104.15.105 | 1/20/17 | avramberkovic@centrum.cz | NS4.ITITCH.COM |
| lgemon[.]org | 173.243.112.202 | 1/31/17 | ezgune@cock.li | STVL113289.EARTH.OBOX-DNS.COM |
| login-freemail[.]com | 86.104.15.105 | 2/17/17 | v.lebzyak@i.ua | DNS1.SECUREFASTSERVER.COM |
| downloadsstore[.]net | 86.104.15.165 | 3/17/17 | tiana_webster@myself.com | NS1.ITITCH.COM |
| rapidfileuploader[.]org | 185.86.148.212 | 7/11/2017 | Not Specific | NS-CANADA.TOPDNS.COM |
Some of these domains, including joshel[.]com and akamaisoftupdate[.]com, were previously identified in a December 2016 Palo Alto report on Fancy Bear (Sofacy) activity. In general, these domains show many of the calling cards of Fancy Bear infrastructure, including the name servers used, use of centrum.cz or 1&1 email domains, and being hosted on dedicated servers. This research has been captured in ThreatConnect Incident 20170919B: root9B Fancy Bear ‘Coming Soon’ Splash Page Research.
The create dates for these domains suggest that these “Coming soon” splash pages may have been regularly used since late 2016. To that end, similar to exploiting the infrastructure registration and hosting tactics mentioned earlier, monitoring for the strings root9B identified may help proactively identify new Fancy Bear infrastructure in the future. As an example, individuals can use a Censys query to identify splash pages with those matching strings.
Thinking Fourth Dimensionally
There is so much we can do with infrastructure like that identified in this post and there so many ways to slice and dice the data to build out intelligence on adversaries. When it comes to your organization’s adversaries, we implore you to be the hero. Don’t be a butthead like Marty McFly. Don’t wait for a time machine, or industry reports, to beat your adversaries and mitigate their operations.

Use historical intelligence to identify your adversaries’ tactics, and stitch together analytic techniques to exploit those tactics and bridge the gap from past to present. Further, by identifying and exploiting your adversaries’ tactics on an ongoing basis, organizations can move from a reactive defense to a proactive one that doesn’t rely on known bad. Or a time machine.
