Posted
With 2024 in our rearview mirror, let’s take a moment to reflect. Like always, threats are evolving, and security challenges are becoming… more challenging: escalations in targeted ransomware attacks, emerging techniques like adversary-in-the-middle phishing, and a stream of vendors throw all of their offerings into the mix that now need to be integrated into your tech stack. The only constant is change (and the need to operationalize threat intelligence!) Here’s a look back at the solutions we delivered to make your job easier and your defenses stronger.
Polarity: Bridging Insights Across Systems with ThreatConnect
Switching between tools during critical investigations is a frustration many security teams know all too well. That’s why ThreatConnect acquired Polarity in 2024—to deliver actionable intelligence directly into analysts’ workflows and eliminate the inefficiencies of context switching. Together, we’ve transformed how teams access and utilize threat intelligence, integrating real-time insights into their existing processes.
Polarity’s Federated Search enabled seamless querying and correlation of data across multiple systems, all within the same interface. This innovation didn’t just save time; it redefined efficiency, empowering teams to focus on the threats that matter most. With the introduction of the CAL integration, Polarity users gained direct access to 2.2 billion indicators, along with feed metadata and analytics. Backed by machine learning and natural language processing, CAL brought real-time insights, automated summaries, and reputation scoring into Polarity, enhancing threat prioritization and decision-making.
By combining Polarity’s federated search capabilities with ThreatConnect’s intelligence ecosystem, we made context switching a thing of the past. These advancements empowered security teams to move beyond reactive responses, enabling them to adopt truly proactive cybersecurity strategies with unprecedented efficiency.
Breaking Down Silos: Helping You Make Faster, Smarter Decisions
When attackers escalate their tactics, like chaining vulnerabilities across systems or using living-off-the-land techniques to evade detection, you need a clear, unified view of the threat landscape. This year, we tackled the problem of fragmented data with tools that bring everything together.
- Clear Context was all about bringing the key insights you need—indicators, tags, relationships—into one view. No more hunting for information; everything was right where you needed it, so you could focus on action, not navigation.
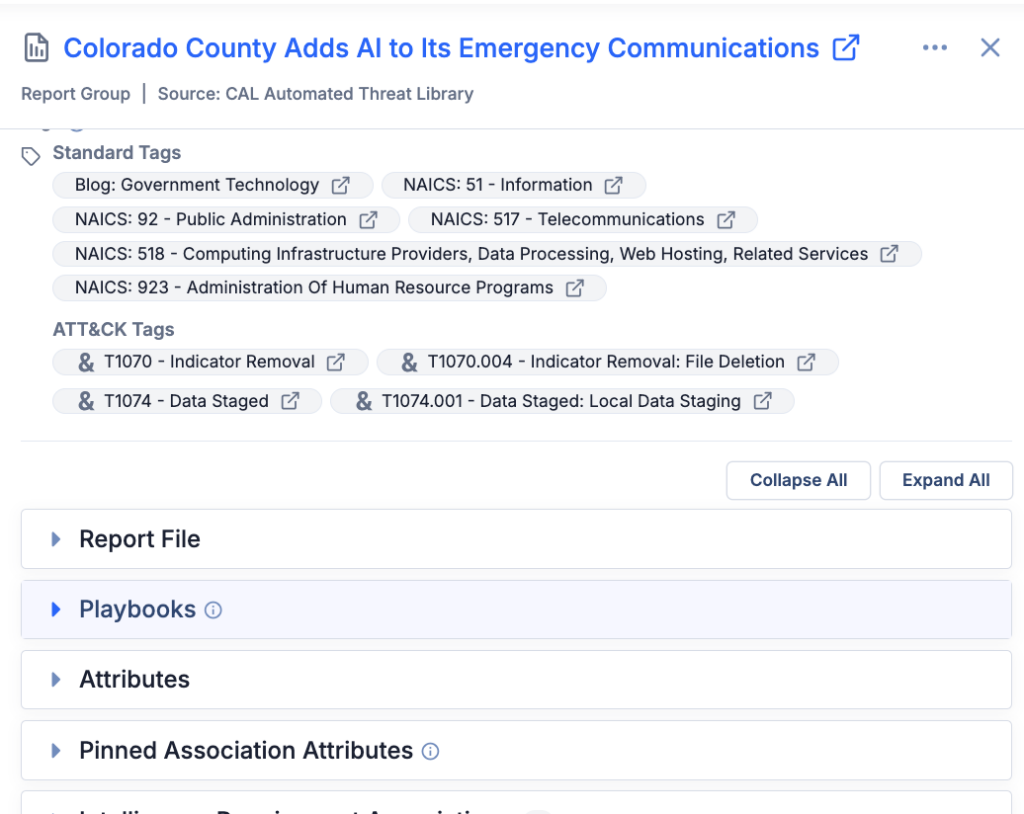
- The ATT&CK Visualizer brought adversary behaviors to life, mapping tactics and techniques to the MITRE ATT&CK framework. Whether it was ransomware operators targeting overlooked controls or emerging threats in your sector, you could identify gaps and prioritize defenses with confidence.
- The Tags Across Owners Card made it easier to see the bigger picture by pulling contextual tags from multiple sources into one place.
These updates were all about helping you spend less time searching for answers and more time acting on them.
Reporting That Doesn’t Make You Want to Tear Your Hair Out
We know reporting can feel like a grind—especially when you’re trying to research or respond to a threat while at the same time trying to report on your progress and get the intel out. It has to be accurate, timely, and clear, but it doesn’t have to be so tedious.
- Reporting Templates let you standardize and automate your reports for Groups, Cases, or whatever you need. No more reinventing the wheel every time you start a new one.
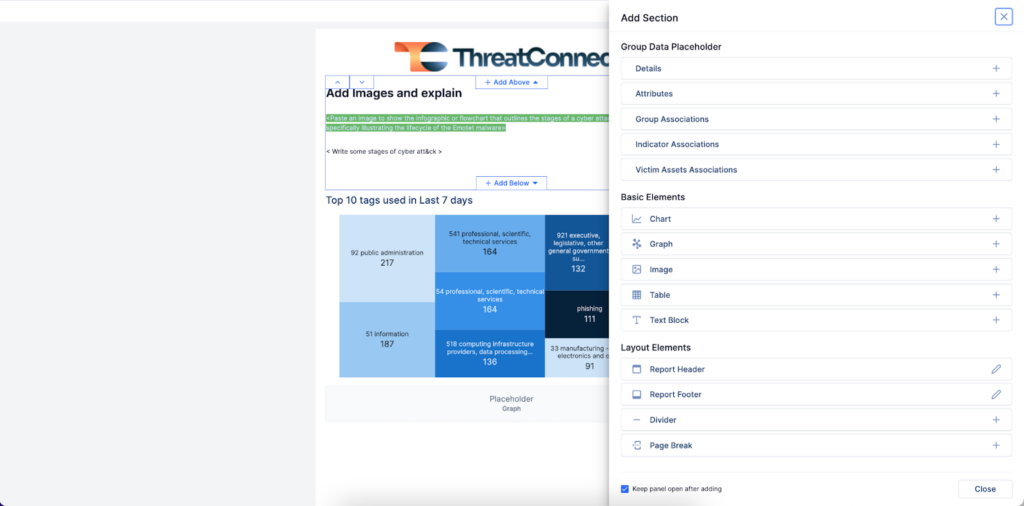
- The WYSIWYG Editor gave you an intuitive way to create polished, stakeholder-ready reports. Whether it was detailing how a supply chain attack unfolded or summarizing your organization’s threat posture, you could focus on the story while we took care of the formatting.
Speeding Up Investigations With Tools That Work for You
Investigations can be tough. You’re on the clock, trying to spot patterns and make connections (“Oh sweet mercy, is this double extortion ransomware??”), but the tools you have might slow you down. This year, we introduced features to help you move faster without losing precision.
- Enhanced Search gave you advanced filters and quick-access actions to cut through the noise and get straight to the intel that mattered most.
- With Polarity’s Federated Search, you could query multiple systems at once—no more jumping back and forth between tools. It saved time and, honestly, a lot of headaches.
- The Match Drawer for Intelligence Requirements helped align your work with your team’s strategic goals, making it easier to prioritize what really matters.
We know your time is valuable, and we hope these updates helped you get the job done faster and with less stress.
Scaling Operations With AI and Automation
This year, we saw attackers leverage tools like generative AI to create more convincing phishing lures and scale their operations. To help you stay ahead, we leaned into AI, too, to level the playing field.
AI Insights transformed the way teams analyzed intelligence reports. By summarizing key takeaways in seconds, this feature reduced the time spent on manual reviews and allowed analysts to focus on actionable recommendations. The consistency and accuracy delivered by AI ensure that critical insights are not overlooked. Also, now in Beta, are AI search summaries and AI report summaries.
The Automated Security Controls Mapping in the ATT&CK Visualizer helped teams identify gaps in their defenses. This feature prioritized vulnerabilities by mapping security controls to specific MITRE ATT&CK techniques and provided clear guidance on where to focus resources.
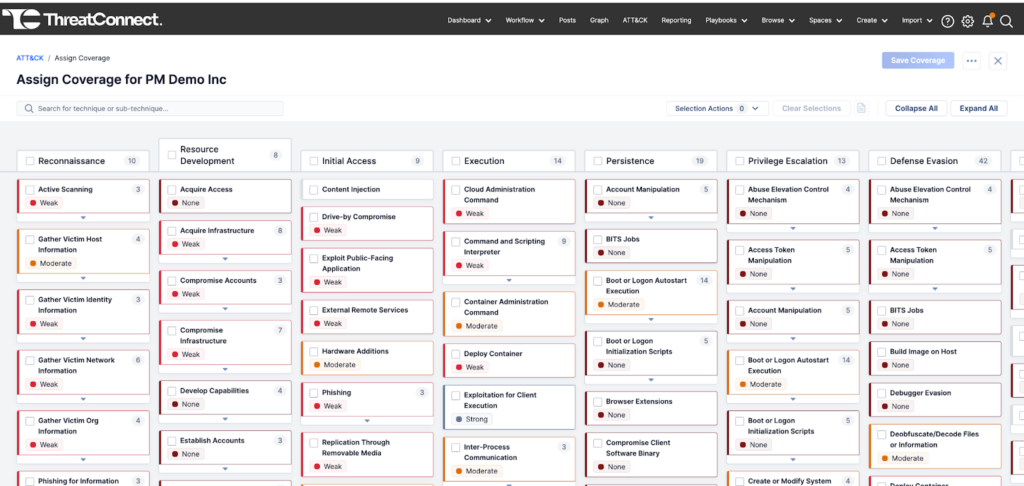
In 2024, enhancements were made to MITRE ATT&CK Classification in ATL, Doc Import, Browser, and Playbooks, enabling users to strengthen their security strategies.
Advancing Sector-Specific Intelligence With Industry Classification
Threats don’t look the same for every organization (banks don’t usually struggle with ICS/SCADA attacks). In 2024, we took a big step forward in tailoring intelligence to your specific needs with Industry Classification. By leveraging AI to classify intelligence by NAICS codes, we made it possible for you to tag intelligence with industry-specific context.
What does that mean for you? It means cutting through the noise and focusing on the threats that matter most to your sector. Whether it’s supply chain vulnerabilities for manufacturing or targeted phishing in finance, this enhancement gave analysts the clarity to prioritize and act faster.
This wasn’t just about making things easier; it was about empowering you with the precision to make smarter, more confident decisions.
Building a Seamless Threat Intelligence Ecosystem
We know your tools need to talk to each other, especially when trying to track fast-evolving threats across different environments. That’s why we focused on integrations to create a more connected ecosystem.
- Recorded Future and CrowdStrike integrations enriched your workflows, giving you the context you needed to make decisions faster.
- Elastic Security and Microsoft Copilot integrations ensured you could operationalize intelligence seamlessly, whether you were responding to a phishing campaign or preparing for a tabletop exercise.
By connecting your platforms, we made it easier to turn intelligence into action right when and where you needed it.
Looking Ahead
2024 was a year of innovation, and we’re so grateful to have been part of your journey. From tackling targeted ransomware to breaking down silos in your workflows, we’ve worked hard to deliver tools that make your life easier and your defenses stronger.
As we head into 2025, we’re excited to keep pushing the boundaries of what’s possible in threat intelligence. Thank you for trusting us to be part of your cybersecurity story. We look forward to another year of collaboration, innovation, and progress.

