Posted
Staying ahead of emerging threats requires timely, actionable intelligence – but sorting through endless reports can slow even the best teams down.
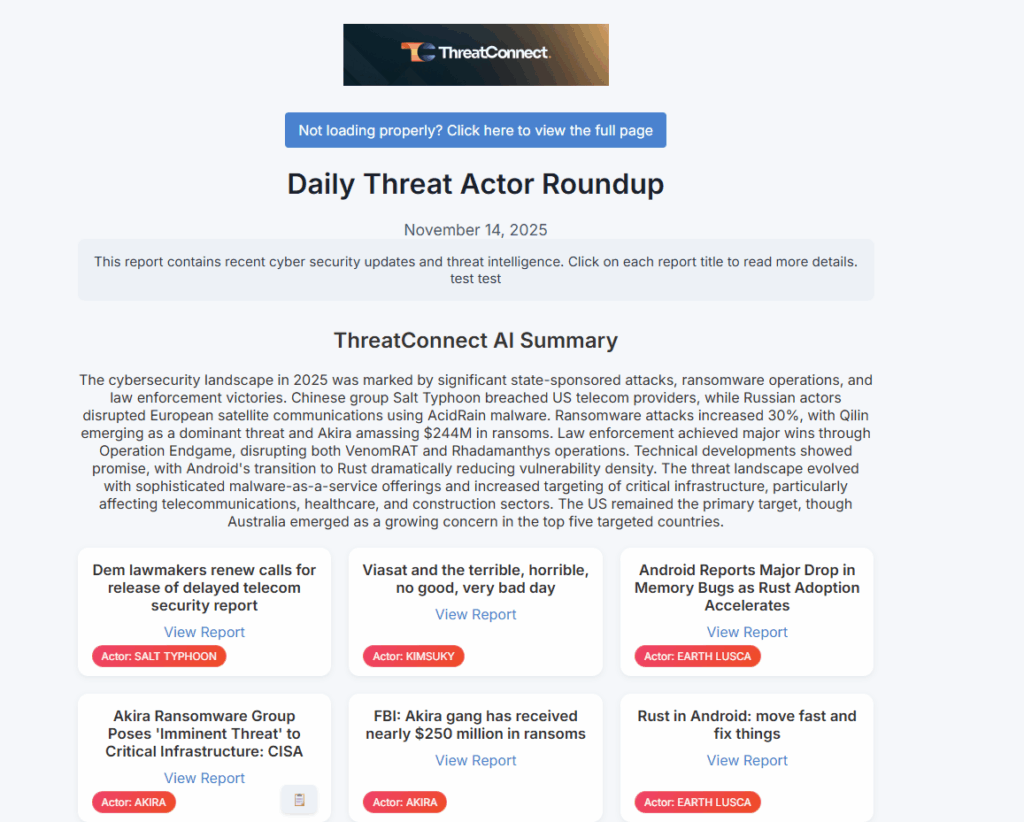
ThreatConnect’s new playbook-driven capability streamlines this process by automatically gathering and summarizing the latest threat intelligence tailored to your team’s interests, such as recent threat actor activity, vulnerability updates, or other areas of focus. Delivered straight to the inbox of your key stakeholders, it provides instant visibility into the latest and most relevant intelligence, as well as pathways to dive deeper into the intelligence that matters most.
Key Benefits:
- Program Visibility: Regular, high-value intelligence updates keep stakeholders informed of current priorities, reinforcing the visibility and relevance of the threat intelligence program while prompting timely feedback on evolving requirements.
- Stay Connected: Ensure your intelligence program remains part of the broader security conversation. Even as stakeholders operate in other platforms or defensive tools, this capability helps maintain alignment with emerging tactics, trends, and threats across the enterprise.
- Stay Informed: Receive daily, curated insights into relevant threat actors, recent campaigns, and emerging trends—helping your team stay ahead of developments that matter most.
- Save Time: Automated data collection and AI-driven summarization eliminate the manual work of reviewing multiple sources, freeing your analysts to focus on higher-value analysis and decision-making.
Whether you want to stay up to date in the CTI team, or help notify your internal stakeholders to help fulfil an RFI – this playbook will enable you to quickly pivot to different intelligence topics.
By transforming complex intelligence feeds into clear, targeted updates, this capability enables CTI and SecOps teams to maintain situational awareness, enhance decision-making, and stay one step ahead in a constantly evolving threat landscape.
How It Works
The Threat Actor Round-up consists of a generic component playbook, which enables the round-up generation, and a timer trigger playbook, which is tailored to focus on Threat Actor-related Intelligence.
Install The Threat Actor Round-up Playbook
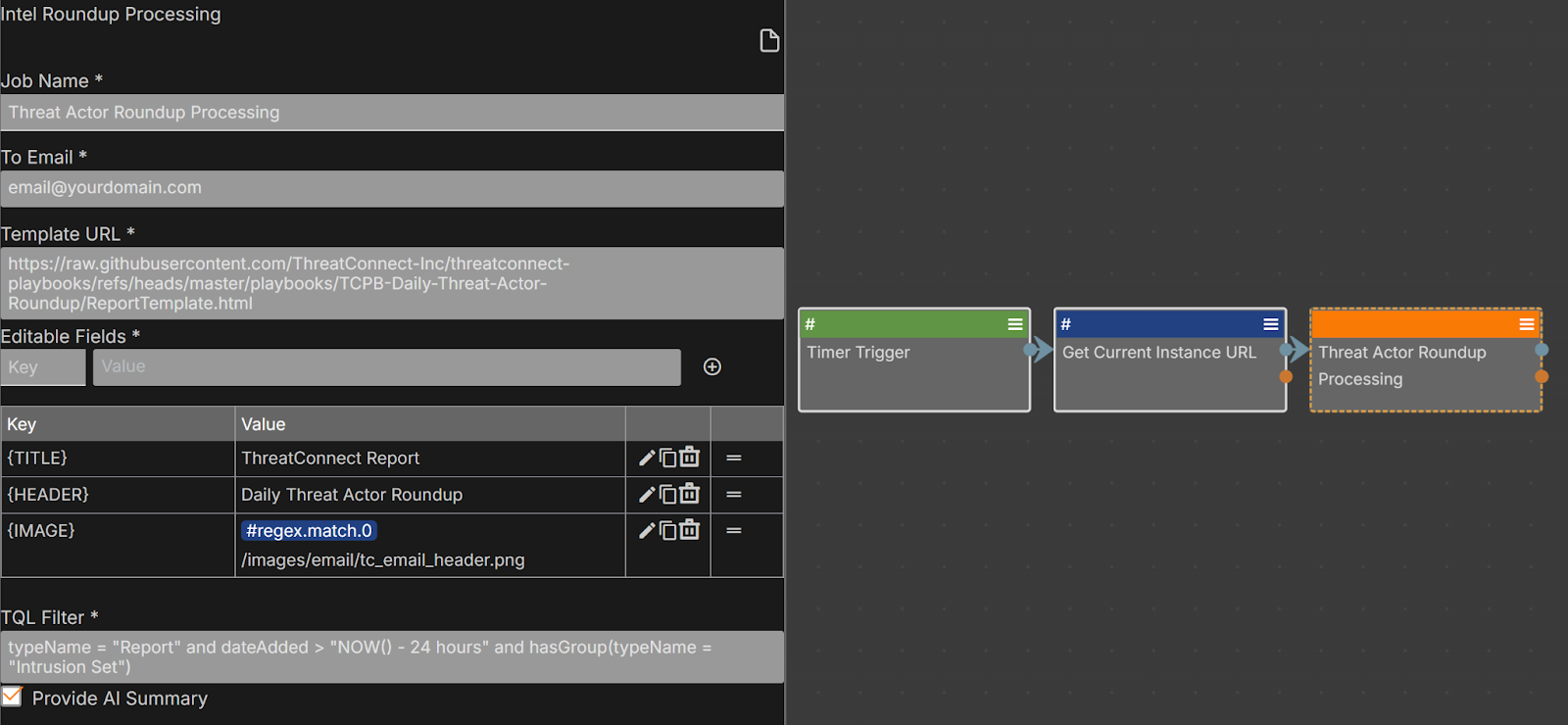
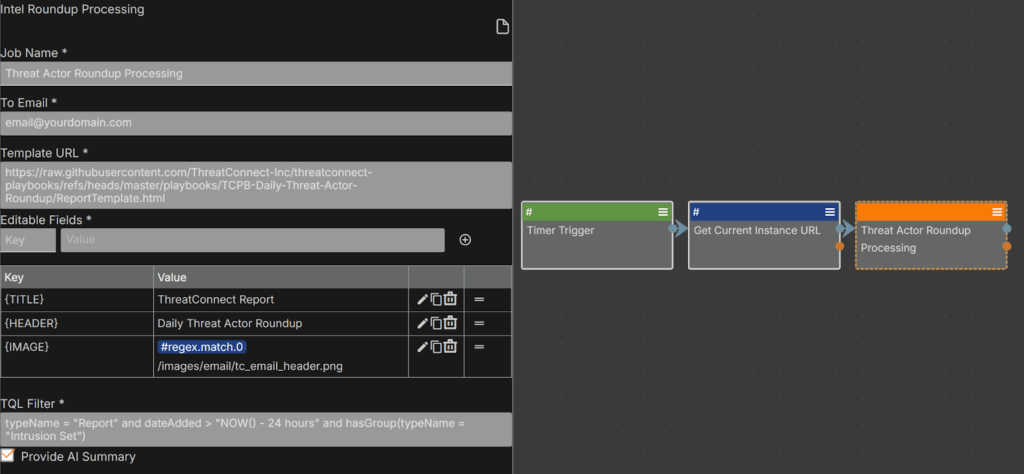
- [Reporting] Daily Threat Actor Round-up: This playbook is a simple one, where you configure the daily time it will run at, as well as a set of fields in the orange step, ‘Threat Actor Round-up Processing,’ to customize this automation for our particular focus: Threat Actor-related Intelligence.
Lead Contributor – Emmet Wray (Director, Customer Success Engineering
- Threat Actor Round-up Processing: which is represented by the orange Threat Actor Round-up Processing step in the above image, is a playbook component containing the actual logic of the process, which is fed by the fields you configured in the above step. This can include customisations such as:
- Group TQL query to select what the daily round-up should focus on
- Enabling AI summarisation using CAL
- Custom Logo & HTML template locations
How does your Company Access the Daily Threat Actor Round-up?
This can be downloaded via GitHub here
Or by importing it as a Shared Playbook using code: TL4EdEqX
If you need assistance with the installation, please refer to the GitHub README above or contact your Customer Success team.
End Result
On a schedule that fits your team’s rhythm, you can automatically deliver timely notifications highlighting the latest intelligence tied to relevant Threat Actor activity—aggregated from all your trusted sources.
Notifications can be tailored to specific audiences or use cases, ensuring the right insights reach the right people—whether that’s a SOC team tracking adversary behavior, a vulnerability team assessing risk, or leadership maintaining situational awareness.
These communications extend the reach of your threat intelligence program beyond the TI-Ops platform, creating meaningful touchpoints with stakeholders across the enterprise. Each update reinforces awareness, drives engagement, and brings users back to the platform content that matters most—keeping threat intelligence visible, relevant, and connected to the mission of defense.
For additional assistance, please contact your Customer Success team or submit a Contact Us form.