Posted
ThreatConnect now supports MITRE ATT&CK Groups and Software within our Platform! Before we dive too deep, let’s define Groups and Software in MITRE ATT&CK.
What are Groups?
Groups are sets of related intrusion activities tracked by a common name in the security community. Analysts follow clusters of activities using various analytic methodologies and terms such as threat groups, activity groups, threat actors, intrusion sets, and campaigns.
What’s software?
Software is a generic term for custom or commercial code, operating system utilities, open-source software, malware, or other tools used to conduct behaviour modeled in ATT&CK.
So why does this matter?/How are groups and software used in ThreatConnect?
You can now more easily track threat groups, malware families, and specific techniques and sub-techniques that are relevant to your organization and industry and then form mitigation plans to address those threats. For example, customers in the Retail and Hospitality industry may want to research and monitor threat actor group FIN6. This cybercrime group has stolen payment card data and sold it for profit on underground marketplaces. They’ve also aggressively targeted and compromised point of sale (PoS) systems in the hospitality and retail sectors.
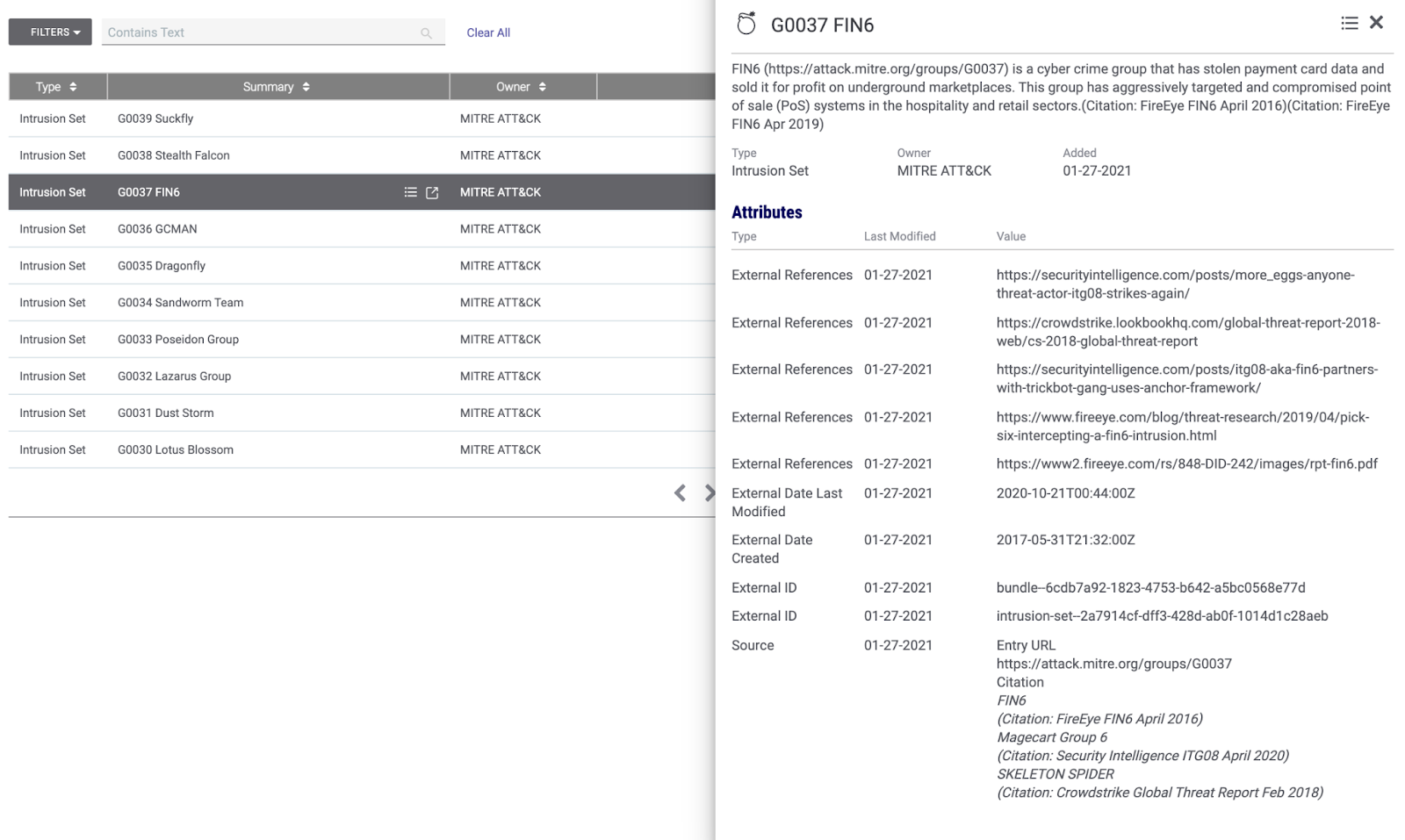
Threat Group – G0037 FIN6
Or you may know of a specific dangerous malware family that has affected your organization in the past. You may have been compromised by something like Smoke Loader, a malicious bot application that can load other malware. With MITRE ATT&CK Software support in ThreatConnect, you can now monitor for this malware and similar malware families and apply a mitigation plan anytime it’s found in your network.
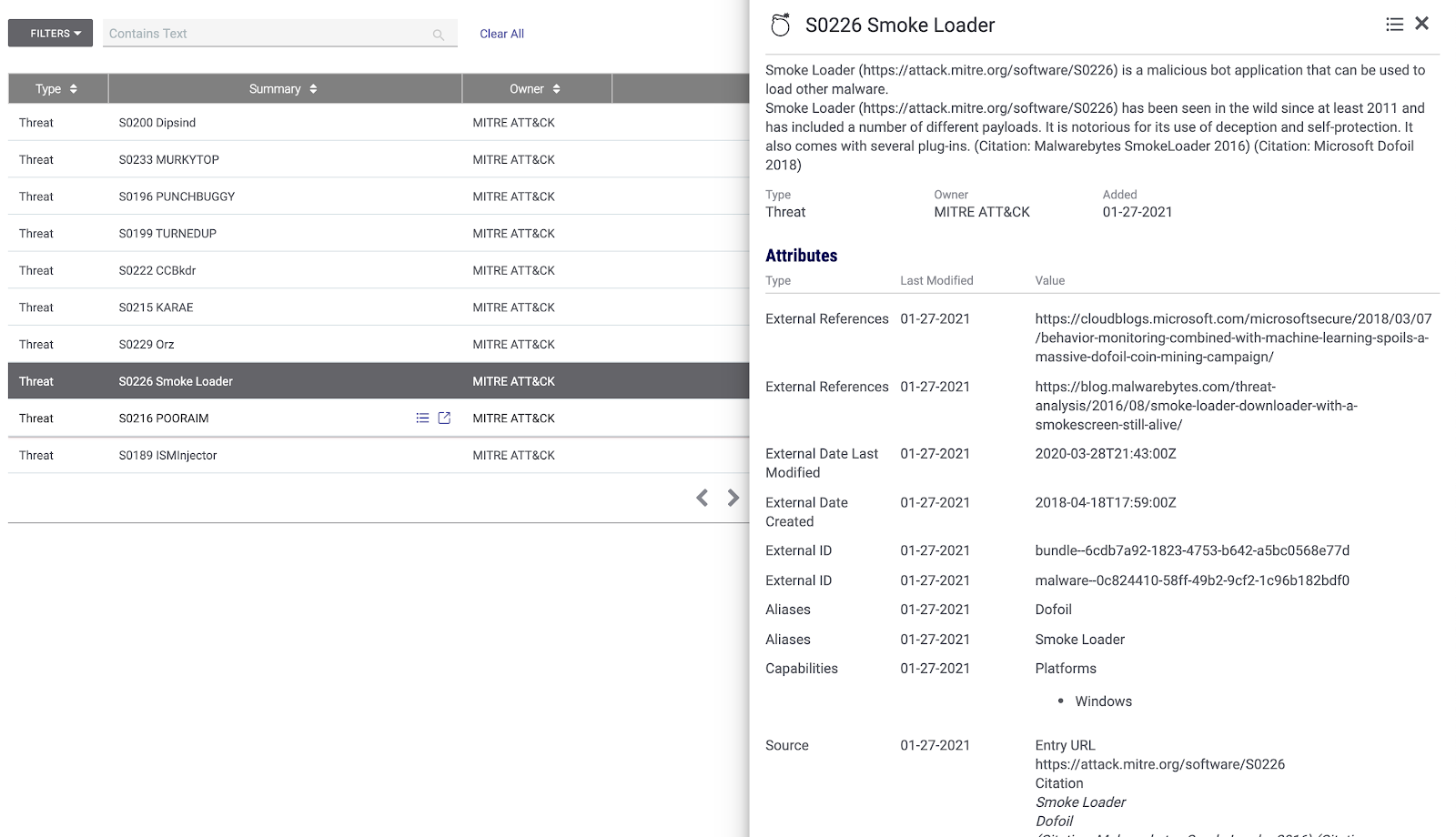
Malware Family – S0226 Smoke Loader
Bringing threat groups and malware families into ThreatConnect helps you to contextualize and prioritize how you respond to threats and what malware families you research.
When you set up MITRE ATT&CK Groups in ThreatConnect, it’s like an additional premium intel feed that doesn’t cost a fortune to set up. For new customers or less mature organizations, it’s going to provide immediate value by bringing in high-fidelity intelligence and avoiding a 0 state or empty platform. Lastly, you can build custom dashboards that track relevant groups and malware families to give your team a birds-eye view of the threat landscape.
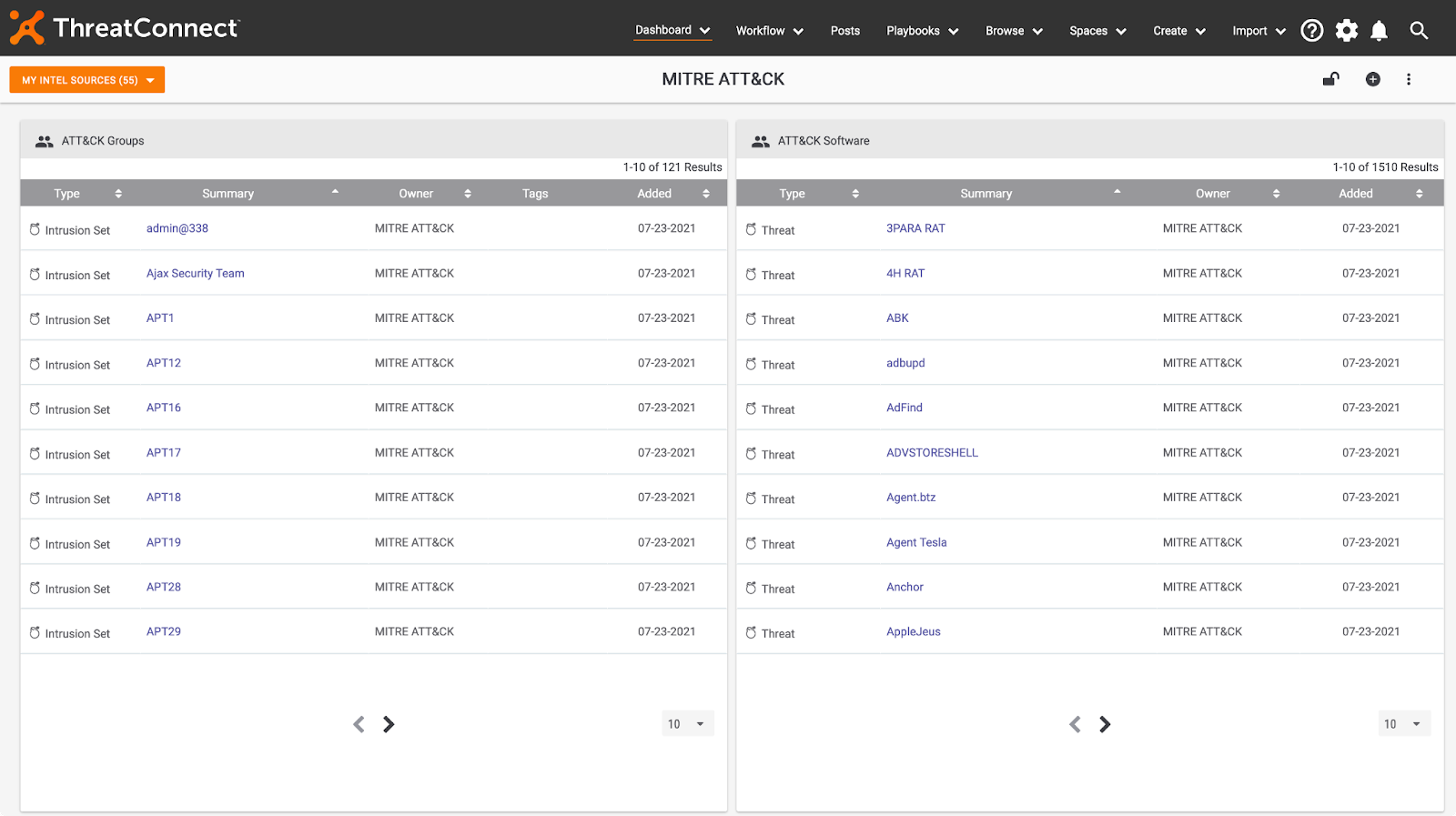
ThreatConnect – MITRE ATT&CK
We are excited to support a deeper functionality with the MITRE ATT&CK framework and have big plans for future enhancement; stay tuned!
If you’re a ThreatConnect customer, please reach out to your dedicated Customer Success Team for more information on using MITRE ATT&CK. If you’re not yet a customer and are interested in ThreatConnect and this integration, please contact us at sales@threatconnect.com.
