Posted
We have exciting news: ThreatConnect now supports the MITRE ATT&CK Framework!
What does this mean for our users? By applying Tags to Indicators and Groups, you’ll be able to classify your intelligence in ThreatConnect using the tactics and techniques of MITRE ATT&CK and, more importantly, derive meaningful conclusions to help you prioritize response and make better decisions.
Directly from the ThreatConnect Platform, you’re able to view all Techniques related to the MITRE Pre-ATT&CK and Enterprise ATT&CK Datasets. Drill down into each Technique to get details mapped directly back to the information provided in the ATT&CK Framework.
In more concrete terms, you can query Intelligence with ATT&CK, create Dashboards with ATT&CK, and drive Playbooks logic with ATT&CK.
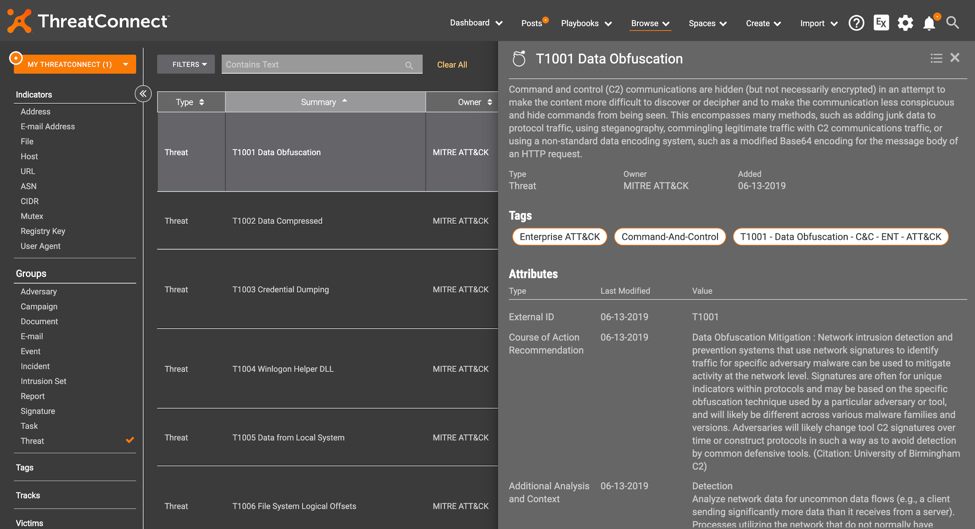
View of the Details Page for the ‘Data Obfuscation’ MITRE Enterprise ATT&CK Technique
Below, we’ve outlined three practical use cases where leveraging ATT&CK within ThreatConnect will help our users classify indicators, prioritize threats, and automate processes.
Using ATT&CK to Ask Critical Questions of Your Intel with TQL
- What can the adversaries I’m up against do?
- Are there critical techniques I’m blind against?
- For key tactics, what are the indicators I should be looking out for?
Once you start classifying your intelligence in ThreatConnect, you can start answering all of these questions and more with ATT&CK thanks to TQL.
Before we go further, here’s a quick review of TQL: ThreatConnect Query Language (TQL) is a SQL-like query language that allows users to build structured queries for advanced search filters, for example “show me Email Address Indicators tied to Incidents that involved ransomware.”
Once you’ve started classifying your intel with ATT&CK, you can use TQL to start asking some complex questions. For example:
typeName in (“File”, “User Agent”) and dateAdded >= “NOW() – 7 DAYS” and hasTag(summary contains (“per – ent – att&ck”))
This query shows all File or User Agent Indicators that have been added in the past week and are associated with the Persistence Tactic (obviously you’ll want to customize things to what matters to you!). You can take things even further by linking together multiple objects. For example, “show me all URL Indicators tied to Incidents of spearphishing” or “show me all Reports we’ve brought in recently that can help me better understand account manipulation.”
Note that TQL queries can be saved for later use and, as you’ll see in the next section, used to power Dashboards.
Using ATT&CK in Dashboards*
A key use for ATT&CK is prioritization. By understanding what tactics and techniques you’re facing, you can prioritize response, allocate resources, inform red teaming and adversary emulation exercises, make strategic decisions, invest in training and education, and the list goes on. You already know that ThreatConnect has very customizable and dynamic Dashboards. Paired with the flexibility of our data model and ATT&CK implementation, you can now use Dashboards to better understand the specific adversary tactics and techniques your security team is up against.
For example, the Dashboard card below shows the top Techniques being used by the Adversaries you’re tracking, as well as any Incidents.
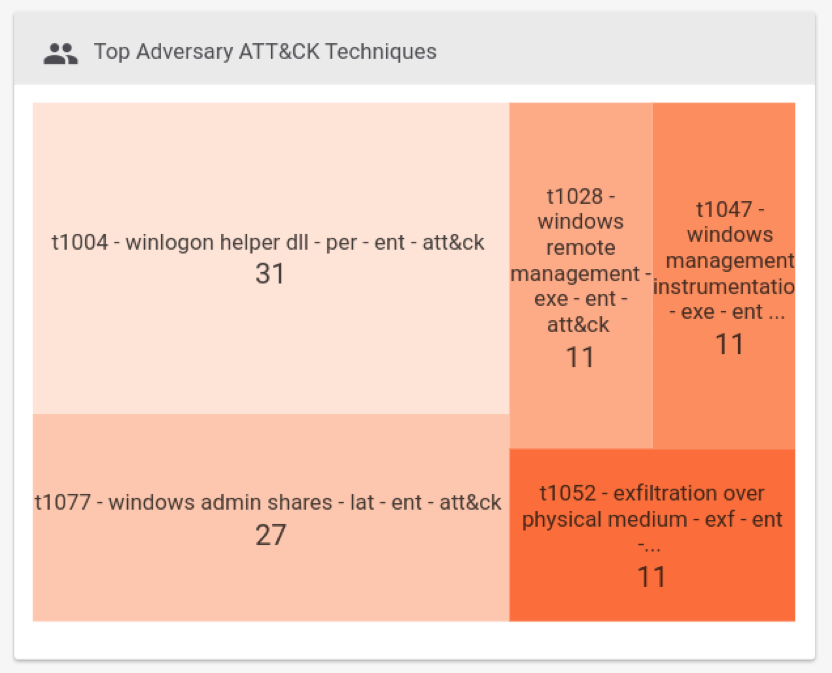
ThreatConnect Dashboard Card Showing Top Adversary ATT&CK Techniques
If you’d like to create a similar card, the underlying TQL query is:
typeName in (“Adversary”, “Incident”) and hasTag(summary contains (” – att&ck”))
Then just set the card to query by Groups and show the Top 5 Tags.
We want to point out that with all of these cards, there is an opportunity to drill down further. In the example above, clicking on T1028 will show you the eleven Adversaries and Incidents where the Windows Remote Management Technique was recorded in conjunction with the Execution Tactic.
Because of how we’ve structured our ATT&CK tags, it’s easy to query on specific tactics or techniques as well. Depending on how you choose to classify your intel using ATT&CK, you can create similar cards around Incidents, Indicators, and other data objects in ThreatConnect.
Using ATT&CK in Playbooks*
At ThreatConnect, we’re all about decisions you can actually take action on. The addition of ATT&CK into the ThreatConnect Platform is no exception. Incorporating ATT&CK into ThreatConnect Playbooks lets you automate how the framework gets utilized in your workflow. For example, let’s say you want your physical security team notified whenever a physical exfiltration incident occurs. The Playbook below will send a Slack message to the physical security team whenever an incident is classified as involving T1052 – Exfiltration Over Physical Medium. This is just a very basic example, and we’re looking forward to seeing how our users continue to leverage the framework in an automated capacity.
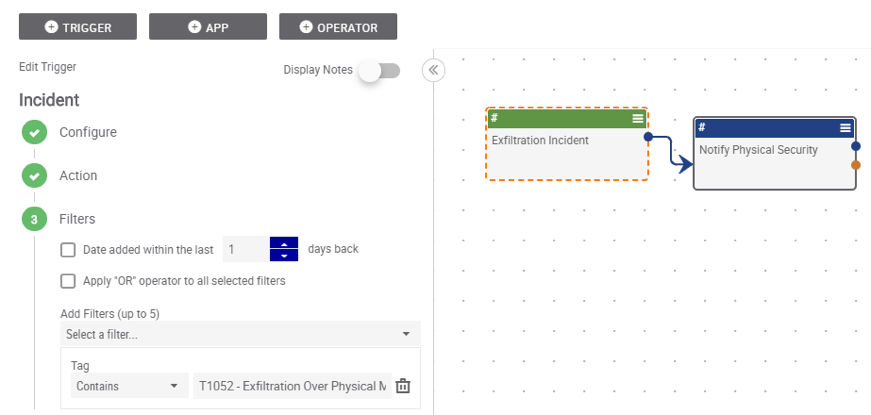
Example of Playbook that Incorporate ATT&CK Techniques in Orchestration Decisions
We view ATT&CK as a powerful framework for understanding adversary behavior and potential gaps in defense, and being able to prioritize those is critical to a successful infosec program. As we see more customers adopting the ATT&CK framework, we want to make sure they have the tools they need to understand the data and tie it to relevant intelligence.
This is just the beginning of MITRE ATT&CK support in ThreatConnect. We’re really excited about what the framework enables, so stay tuned as we continue to roll out more ATT&CK-related features in the coming months and beyond!
*Note that custom Dashboards and Playbooks require a paid subscription to a ThreatConnect dedicated cloud or on-premises instance.
