Posted
ThreatConnect and Sumo Logic have partnered to deliver a new Playbook app. With this app, SOC analysts can automate searches for events in Sumo Logic and use these searches to do things like retroactive threat hunting or enriching an investigation with important Sumo Logic data. By automating these processes, you allow your team to work through investigations more effectively.
The following use cases are now enabled with this app:
- Threat Hunting. As part of an investigation, you may want to search Sumo Logic events for matching ThreatConnect indicators or Case Artifacts. By automating this process, you can introduce efficiency and consistency while freeing your analyst team of tedious tasks.
- Investigation Enrichment. As part of an investigation into Unauthorized Access, you may want to get a user’s activity logs around the same time period. By enriching an investigation with events or logs from Sumo Logic, you help your security team to make faster and more informed decisions and work through an investigation more quickly.
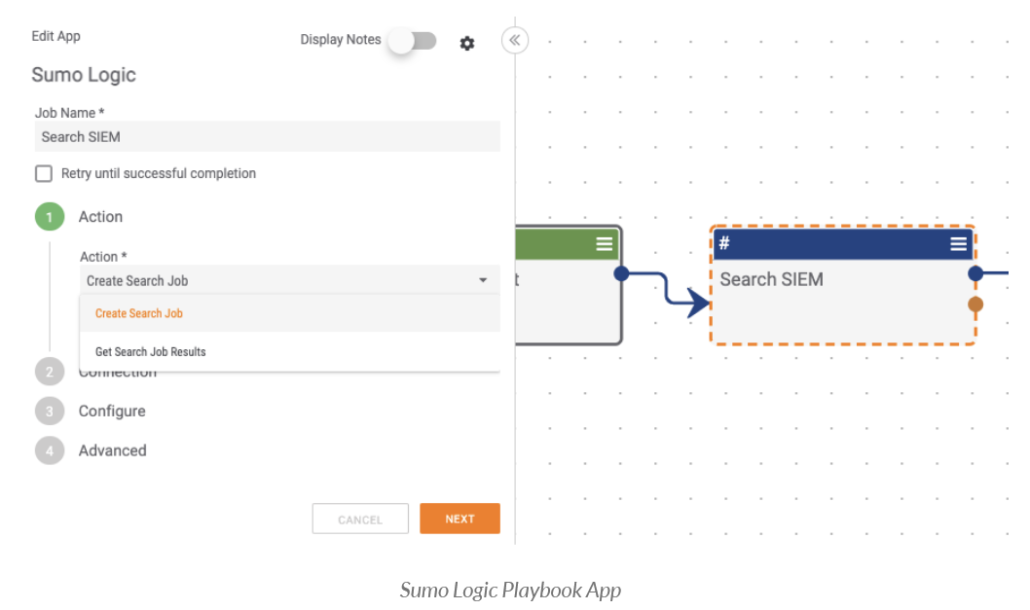
The following actions are available:
- Create Search Job: Creates a search job.
- Get Search Job Results: Get the results of a Search Job.
Together, ThreatConnect and Sumo Logic help users to automate searches in Sumo Logic as part of a threat hunting or an investigation enrichment process. If you’re a ThreatConnect customer, please reach out to your dedicated Customer Success Team for more information on how to take advantage of the Sumo Logic Playbook App. If you’re not yet a customer and are interested in ThreatConnect, contact sales@threatconnect.com.
