Posted
We’re improving our integration with Intel 471 by releasing more apps and functionality between the platforms. We now have multiple Runtime Playbook Apps, a Job App, and a Service App for joint customers to leverage.
The following use cases are enabled through this integration:
- Utilize Intel 471 intelligence in an enrichment fashion to correlate and validate alerts during the triage process, providing more context for SOC analysts, helping them make a more informed decision on the priority and severity for follow-on investigative actions
- Focus on the probability of exploitation of vulnerabilities in the wild via regularly updated reports that track the life cycle of significant vulnerabilities observed in the underground from initial disclosure to exploit weaponization and productization. Vulnerability Intelligence offers an analyst-driven assessment of priority vulnerabilities beyond volumetric keyword hits
- Gain a more holistic understanding of the threat landscape by leveraging finished reporting on malware families, which provides analysis of the malware and features, network traffic, how to identify, detect, and decode it, extract and parse its configuration, control server(s) encryption key and campaign ID
These apps will allow you to automate intelligence processes, investigations, response actions, and more. With this release, the following apps are available:
Improvement to existing:
- Intel 471 Adversary Intelligence Job App
- Intel 471 Information Reports: Tactical and operational intelligence reports on notable cyber activity derived from human intelligence sources and engagement with threat actors and communication channels.
- Intel 471 FINTEL: A number of different finished intelligence products, including Intelligence Bulletins, Threat Actor Profiles, Underground Pulse, Underground Perspective, and Intelligence Whitepapers.
- Intel 471 Spot Reports: Short reports providing breaking news and observations on notable events, actors, malware, and possible breach alerts.
New Apps:
- Intel 471 Malware Intelligence Job App
- Malware Intelligence Reports: In-depth analysis of malware families and features, network traffic, code samples, how to identify and detect, how to decode, extract and parse its configuration, control server(s), encryption keys, and campaign IDs.
- Malware Indicators: Curated, High-Fidelity Indicators of Compromise (IOCs) Feed – Near-real-time feed of file and network-based indicators from Malware Intelligence for automated ingestion into security systems to block and detect malicious activity from malware.
- Intel 471 Vulnerability Intelligence Job App
- Vulnerability Reports: Offer the ability to track significant vulnerabilities to assist patch prioritization and vulnerability management based on what is being discussed, developed, bought and sold, exploited, and productized in the underground.
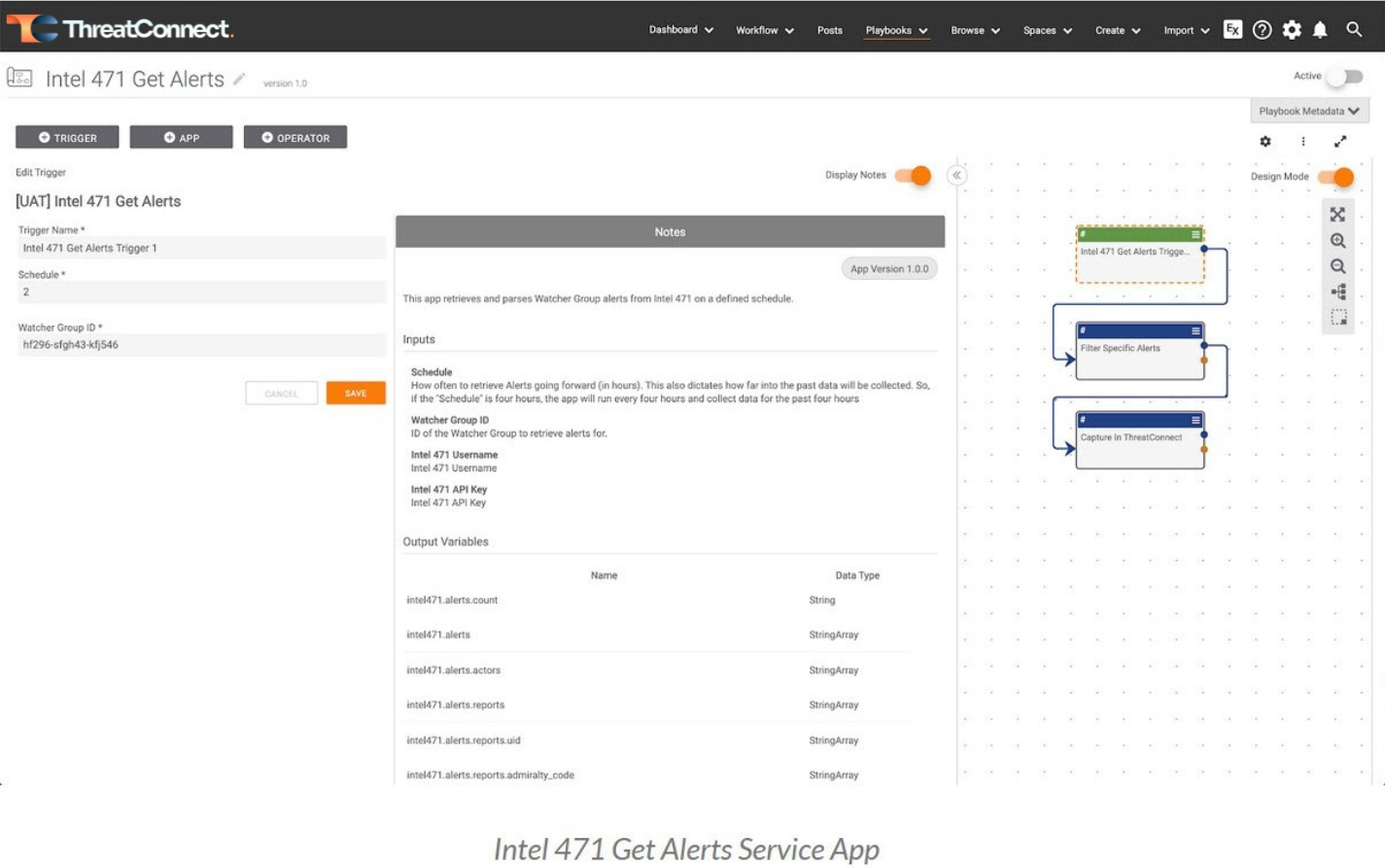
- Intel 471 Get Alerts Service App
- Alerting Functionality on Underground Collections: Intel 471 provides extensive intelligence collection and research across forums, marketplaces, and other communication channels (i.e., Telegram, Discord, etc.) in the Cyber Underground. This involves the tracking of threat actor communication and activities, along with the products, tools, services and tactics/techniques/procedures (TTPs).
Together, ThreatConnect and Intel 471 provide a comprehensive integration that consists of several apps to achieve multiple use cases. These apps all help to automate analysis, investigations, response actions, and more. If you’re a ThreatConnect customer, please reach out to your dedicated Customer Success Team for more information on utilizing the Intel 471 integrations. If you’re not yet a customer and are interested in ThreatConnect, contact sales@threatconnect.com

