Posted
ThreatConnect and Cuckoo Sandbox have partnered to deliver a new Playbook app for joint customers. This Playbook app will allow you to automatically detonate, analyze, and submit files and URLs in Cuckoo Sandbox from ThreatConnect to understand if they are malicious and return any contextualized telemetry. This all leads to more informed decision-making and more efficient remediation of malicious files through automation.
Cuckoo Sandbox
The following capabilities are available:
- Automated Malware Sandboxing
- As part of a security process, you can automatically send malware to Cuckoo Sandbox. Once sandboxed and depending on the Malware too, you can get outputs in the form of C2 communications, file hashes, registry keys, MITRE ATT&CK tags, YARA signatures, and more. You can then use these outputs to inform detection and remediation processes in the rest of your security stack.
- Enrichment
- As part of an investigation, you may come across a familiar file hash and want to see if you’ve seen it and sandboxed it before. You can use ThreatConnect to query Cuckoo Sandbox and retrieve this information as part of an enrichment process during a case or investigation.
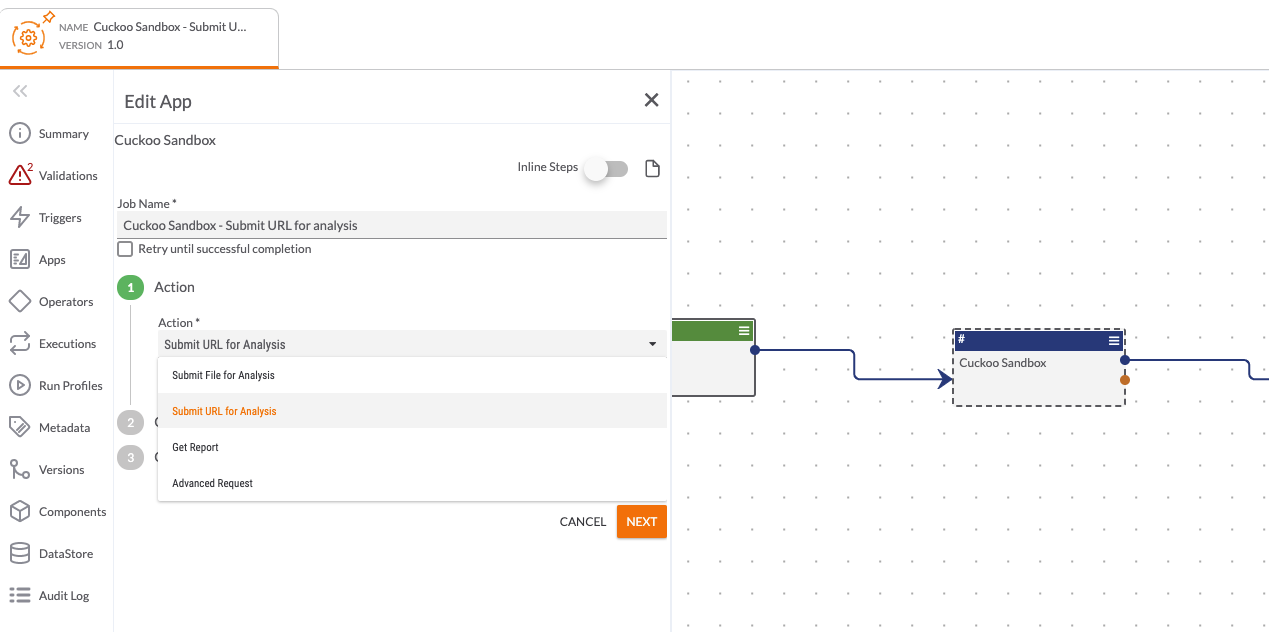
The following actions are available within the Playbook App:
- Submit File
- Submit URL
- Get File Enrichment
- Advanced Request
Together, ThreatConnect and Cuckoo Sandbox helps you to automate remediation tasks and protect your network from sophisticated attacks. If you’re a ThreatConnect customer, please reach out to your dedicated Customer Success Team for more information on how to install and use this Playbook app. If you’re not yet a customer and are interested in ThreatConnect and this integration, please contact us at sales@threatconnect.com.