Cisco
Cisco (Nasdaq: CSCO) is the worldwide technology leader that has been making the Internet work since 1984. Our people, products and partners help society securely connect and seize tomorrow’s digital opportunity today.
Integration(s)
Built By ThreatConnect
Built By ThreatConnect
Related Resources
Built By ThreatConnect
Built By ThreatConnect
Built By ThreatConnect
Related Resources
Built By Polarity
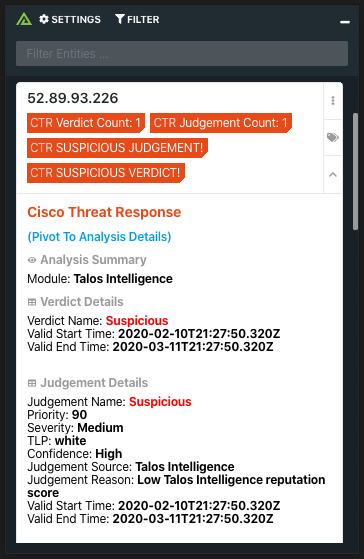
Cisco Threat Response with Polarity
Keep ReadingRelated Resources
Built By Polarity


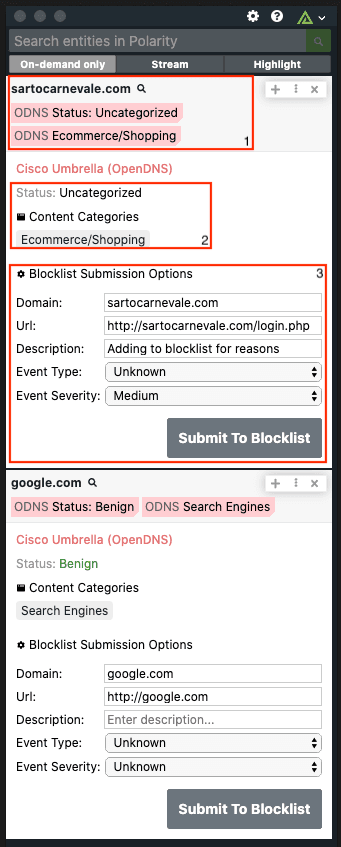
 Polarity
Polarity