Posted
ThreatConnect has built new integrations to work with Amazon’s cloud infrastructure. With these integrations, you can more easily monitor and protect your AWS environment.
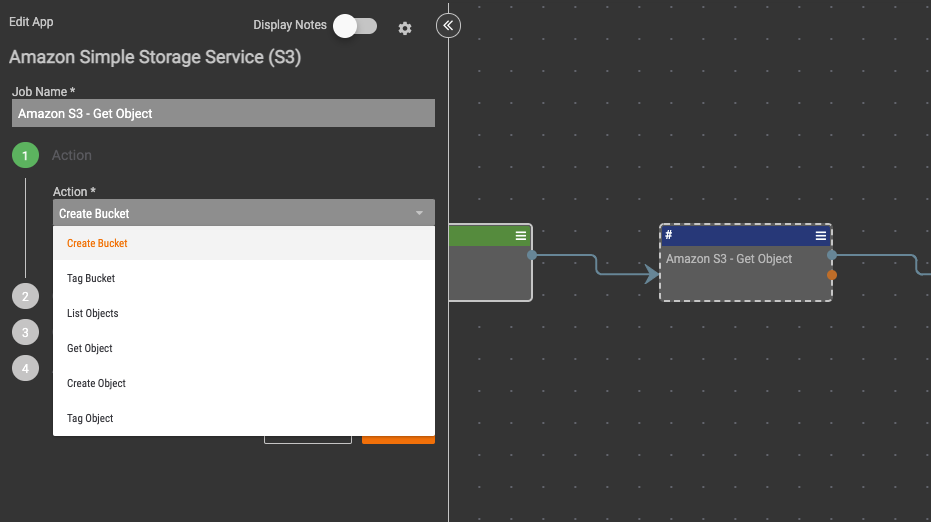
Amazon Simple Storage Service (S3) is a service offered by Amazon Web Services that provides object storage through a web service interface. Amazon S3 uses the same scalable storage infrastructure that Amazon.com uses to run its global e-commerce network. The S3 Playbook app allows you to take automated actions with Amazon S3 buckets and objects so that you can more easily manage security policies and configurations.
The following actions are available:
- Create Bucket – Creates a new S3 bucket.
- Tag Bucket – Sets the supplied tag-set to a bucket that already exists in S3.
- List Objects – Returns some or all (up to 1,000) of the objects in a bucket.
- Get Object – Retrieves objects from Amazon S3.
- Create Object – Adds an object to a bucket.
- Tag Object – Sets the supplied tag-set to an object that already exists in a bucket.
Amazon Simple Storage Service Integration
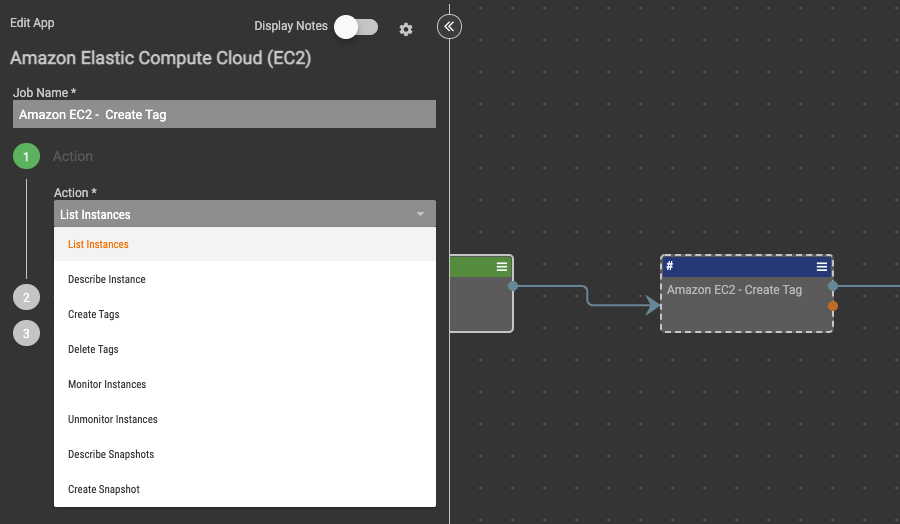
Amazon Elastic Compute Cloud (EC2) allows users to rent virtual computers to run their own computer applications. For ThreatConnect customers that leverage EC2 for the bulk of their cloud infrastructure, there’s potential exposure for malicious activity. Should there be a successful breach and remediation must take place, the EC2 Playbook App allows you to perform various Incident Response actions on your EC2 infrastructure directly from ThreatConnect.
With this App, the following actions are available:
- Describe Instances
- Create Tags
- Delete Tags
- Monitor Instances
- Unmonitor Instances
- Describe Snapshots
- Create Snapshot
- Assign Security Group
- Remove Security Group
- Add ACL
- Remove ACL
Amazon Elastic Compute Cloud
Together, ThreatConnect and Amazon help security teams to monitor for malicious activity and protect their AWS accounts and data. If you’re a ThreatConnect customer, please reach out to your dedicated Customer Success Team for more information on deploying the Amazon apps. If you’re not yet a customer and are interested in ThreatConnect and this integration, please contact us at sales@threatconnect.com.