Posted
Context is everything. The newest release from ThreatConnect helps cyber threat intelligence (CTI) teams get more context quickly, enables faster investigations, provides a more robust threat library, and has updated dashboards so that SOC/IR leaders can accelerate the team’s efficiency. The contextual enhancements available with ThreatConnect 6.4 builds upon our foundation of Intelligence-Driven Operations, empowering the workflow of threat intelligence and security operations teams. This blog focuses on the value relevant to both CTI teams and security operations teams.
More Context for IOC Investigations with Explore with CAL™
Searching through multiple systems and clicking through many sources makes the process of finding relevant threat intelligence time-consuming and cumbersome. CTI and security operations analysts need to start and continue investigations within their threat intelligence platform (TIP) to get fast conviction on an indicator and its relationships to determine if it’s an indicator of compromise (IOC) and if it’s relevant to the organization or not.
With the new Explore with CAL™ capability, you can now pivot directly within the Collective Analytics Layer (CAL™) dataset to understand the complex, bidirectional relationships that exist within a particular indicator such as :
- WHOIS registrations
- DNS resolution
- nameservers
- host data
- subdomains
- ASNs
- CIDR ranges
In addition to exploring what information CAL™ has related to a given indicator, users can also see the relationship context on the graph.
Exploring the Graph with CAL allows you to tell a meaningful, relational narrative around a particular indicator. You can even export a high-resolution image of the expanded Graph for presentations or meetings.
With Explore with CAL, you get more context and can perform faster investigations all within ThreatConnect. This is just the first phase of several graph-based iterations and we plan to add an even deeper functionality for CTI analysts to track, build, and communicate their investigations so stay tuned!
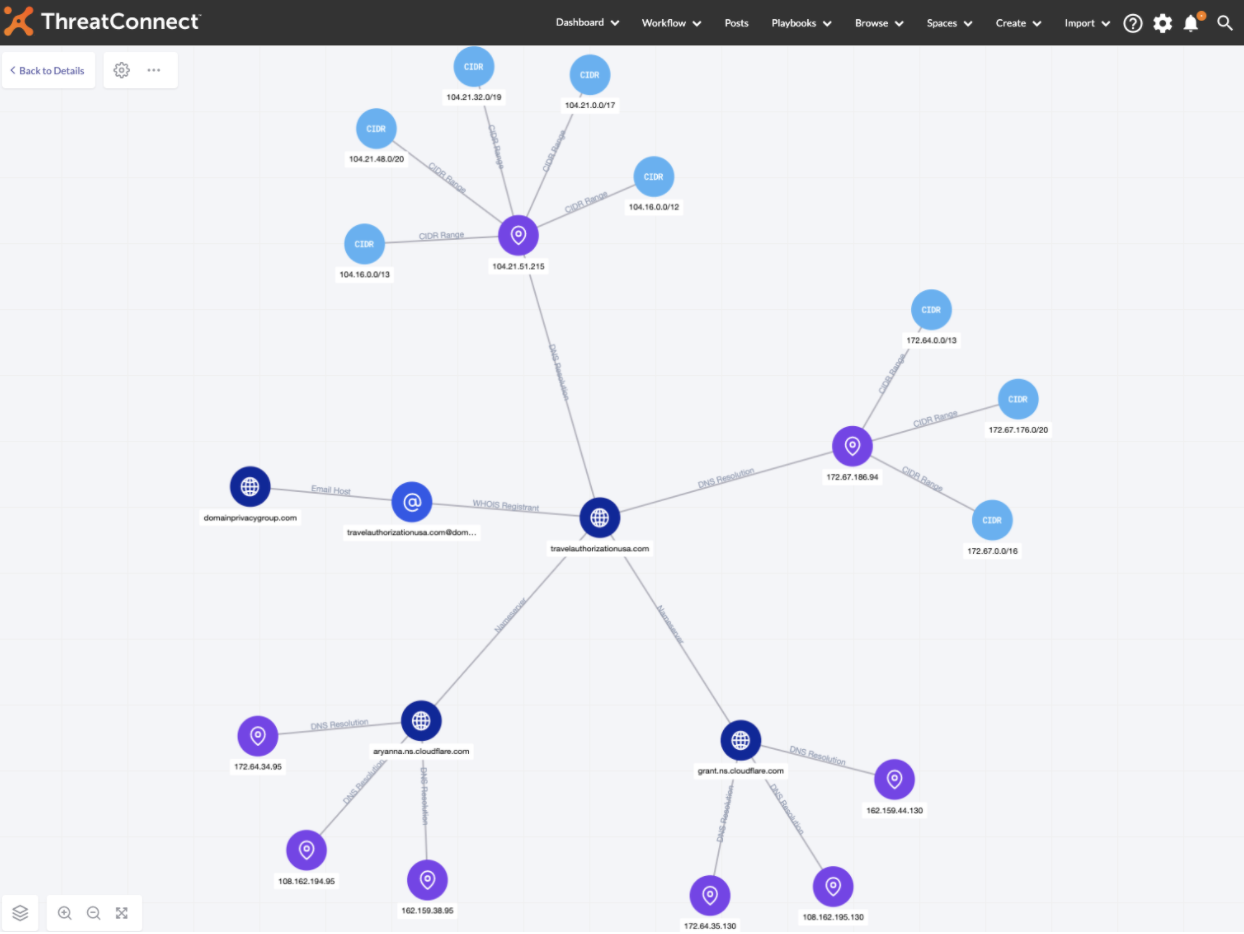
Relationship information is available on the lines connecting nodes on the new Graph
Faster Investigations with Intelligence Anywhere V2
Earlier this year we announced ThreatConnect Intelligence Anywhere and in this release, we are excited to announce version 2!
ThreatConnect Intelligence Anywhere V2 extends support for matching entities beyond indicators and now matches on threat actor names, tools, and malware families. Better yet, it creates a Rosetta Stone for Threat Actors, matching known industry names for the same groups, allowing you to get more context more quickly. As a result, a process that used to take several minutes multiple times a day can now be performed in seconds, saving you time and allowing you and your CTI team to make fast and informed decisions. We have also made significant UX and UI improvements to make viewing and importing known and unknown indicators more intuitive.
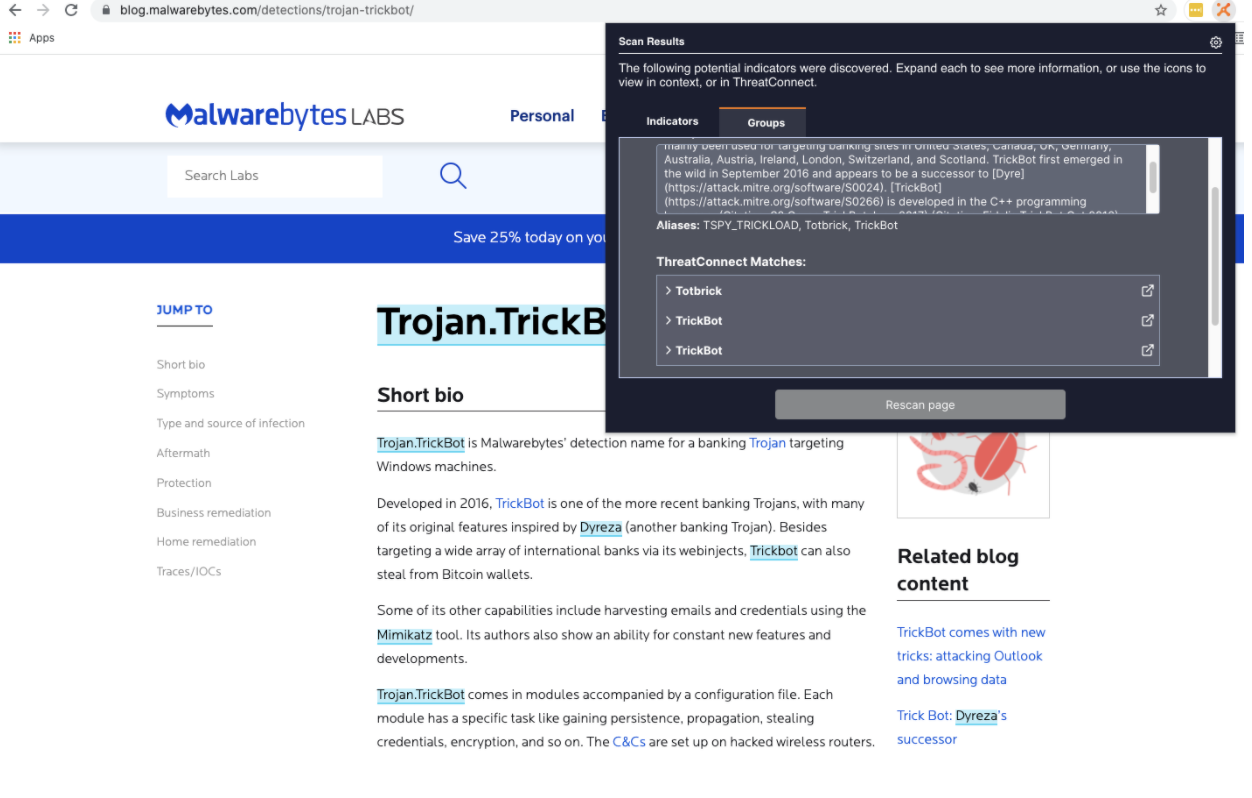
Users are presented with a list of Aliases for Groups found on any web page
Best of all, Intelligence Anywhere is available for all ThreatConnect customer users: TIP, SOAR, or our combination package and for Full Users or Comment Only Users! You can download it in Chrome or Firefox. Check out its capabilities and features here.
ThreatConnect’s risk-led, intelligence-driven approach reduces complexity, integrating processes and technologies to continually strengthen defenses, drive down risk, and revolutionize the way customers protect their organizations by turning intelligence into action. We are excited about the value that these new features will bring to CTI teams. ThreatConnect TIP allows teams to perform faster investigations and get more context quicker than ever before. For more information on these capabilities and how ThreatConnect can help your organization, please reach out to sales@threatconnect.com.