Posted
Introduction to Threat Intelligence and Risk Management
Several of us at ThreatConnect attended the Gartner Security & Risk Management Summit last week, which, conveniently took place right across the river from our home offices. I’m not sure if it’s the Summit, the summer, or something else, but I’ve been thinking quite a lot lately about the relationship of threat intelligence and risk analysis. Whatever the reason, it seems like a good time to kick off a couple blog posts exploring these two disciplines that are very important to the domain of information security management.
“Interesting…but so what?”
Years ago, I joined TruSecure’s Risk Intelligence Team. It was a great group of professionals, and those first few years shaped much of my thinking about how security works. It never occurred to me that the team’s name combined two concepts (“risk” and “intelligence”) that many see as completely different disciplines. More than one person asked me if we did something like business intelligence, and more than once I gave the answer I thought was obvious – our mission was to collect, analyze, and distribute information about security threats, vulnerabilities, and impact (risk).
I think this highlights an issue that runs much deeper than just the name of a team. One of the common complaints I hear about threat intelligence – especially from infosec leaders and executives – boils down to “so what?” Though every intelligence reference I can remember identifies decision support as a primary deliverable, practice seems to fall short of expectations in the eyes of many. I think many associate threat intelligence only with things like tracking bad guys, reversing malware, and collecting indicators – all interesting and useful in their own right, but far removed from the C-Suite. And I readily admit that the cyber intelligence community/industry has intensified (intentionally or unintentionally) that perception over the last several years. The result has been that, for many at least, threat intelligence seems more about driving headlines and taglines than actual decisions.
So what’s the “so what?”
I hope to convince you that there is indeed a “so what” for threat intelligence when it comes to managing information risk. I will also attempt to clarify what that role is and where it fits within the risk management process.
The main point I’ll be unpacking during this series is this: threat intelligence is like food for malnourished risk models. The standard fare for risk models is input like high-medium-low and red-yellow-green, so we shouldn’t be surprised when they don’t mature and perform as well as we need them to. Good intelligence makes smarter models; smarter models inform decisions; informed decisions drive better practice; better practice improves risk posture…and that, done efficiently, makes a successful security program.
The intelligence process
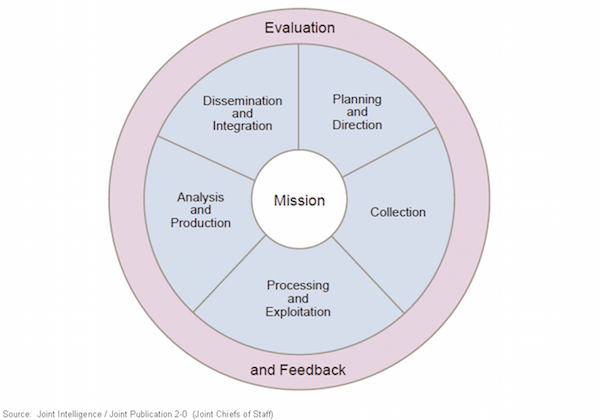
We’re going to talk about how threat intelligence relates to the risk management process, but first it’s helpful to remember that intelligence is itself a process. That basic process is traditionally described as a cycle that includes direction, collection, processing, analysis, dissemination, and feedback. Several proposed variations exist, but our goal here isn’t to build a more precise diagram of the intel hamster wheel. We just need a baseline that lets us segue to risk management, and the above ticks that box.
Intelligence within the risk management process
The risk management process also has quite a few variations over the years. The recent Cybersecurity Framework, born of Executive Order 13636, proffers the simple definition of identifying, assessing, and responding to risk. I’m a simple man, so I kinda like that one. But it isn’t a big help to figuring out how threat intelligence fits within that triad other than “yep; I can see how intel could help me identify risks.”
The stated purpose of the Cybersecurity Framework is to complement rather than replace an organization’s risk management process and, as such, doesn’t get too prescriptive about the process itself. Thus, our goal of identifying where intelligence fits within that process is better served by examining a dedicated risk management framework. NIST SP 800-39 (Managing Information Security Risk) and ISO/IEC 27005 (Information Security Risk Management) are two widely used examples referenced by the Cybersecurity Framework that we’ll review in follow-up posts.
So what’s next?
I originally intended to cover this topic in one post, but I realized after diving in that it wasn’t going to happen. Here’s what I plan to hit over the next few weeks:
- Threat Intelligence and Risk Management: An Introduction (check)
- Threat Intelligence within the Risk Management Process
- Threat Intelligence-Driven Risk Analysis
- Threat Intelligence within Third Party Risk Management
Thanks for reading and I hope you’ll hang with me as I explore this further.