Posted
The Analyst’s Dilemma: Too Much Noise, Too Little Time
Let’s be honest—being a security analyst is a constant race against time. You’re bombarded with alerts, threat feeds, intelligence reports, and SOC escalations while trying to correlate data, determine risk, and take action—before a breach occurs.
The challenge isn’t just getting intelligence; it’s getting the right intelligence in the right place, at the right time, without switching between countless tools.
That’s where ThreatConnect and Polarity come in. By combining automated intelligence ingestion, contextual overlays, and workflow integration, your team can move faster, prioritize better, and respond confidently.
And now, with the launch of Recorded Future Intelligence Engine 2.0.0 integrated into ThreatConnect, your security operations have become even smarter, faster, and more efficient.
Expanding Threat Intelligence with Recorded Future 2.0.0 and ThreatConnect
ThreatConnect combines intelligence enrichment, automation, and threat prioritization in one powerful platform. Now, the Recorded Future Intelligence Engine 2.0.0 integration takes it to the next level by offering:
Standard Alerts: Act Faster with Real-Time Intelligence
Instead of manually checking for threats, ThreatConnect now ingests Recorded Future’s critical alerts, automatically bringing high-risk indicators into your workflows. Whether it’s a new malware campaign, a surge in phishing activity, or an emerging zero-day exploit, your team is alerted instantly, reducing response time.
Threat Map: Prioritize the Most Relevant Threats
Not every threat is created equal. The new Threat Map helps analysts:
- Identify the Intrusion Sets and Malware groups most relevant to their organization.
- Prioritize threats based on Intent (who’s behind the attack), Prevalence (how common it is), and Opportunity (how likely it is to impact your environment).
- Automatically create and associate related threat entities to speed up investigations.
Threat Intelligence Engine Dashboard: Better Visibility, Better Decisions
A revamped user experience gives analysts a clear, centralized view of Recorded Future’s intelligence inside ThreatConnect, making it easier to:
- Track data ingestion progress and monitor intelligence feeds.
- Download job files to inspect and analyze threats in greater depth.
- Gain deeper insight into threat relationships, risk scores, and attack patterns.
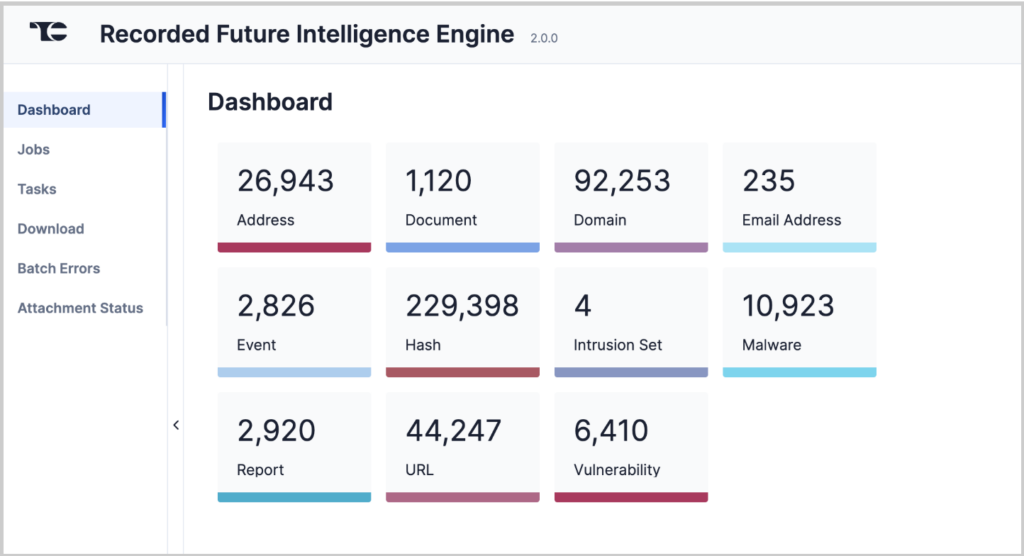
With these capabilities, security teams can filter out the noise, focus on relevant threats, and streamline intelligence workflows—all within ThreatConnect.
Example Scenario: Proactively Responding to Emerging Threats
Imagine a financial services company using ThreatConnect and Recorded Future for threat intelligence operations.
Detection: A High-Risk Malware Alert Appears
- Recorded Future’s Standard Alerts detect a new malware campaign targeting banking infrastructure.
- The malware, linked to a known financial threat actor, has compromised institutions in multiple regions.
- The alert is automatically ingested into ThreatConnect, triggering an intelligence correlation process.
Prioritization: Assessing the Threat Impact
- The Threat Map reveals that this malware is highly prevalent in the financial sector, making it a priority.
- Recorded Future’s risk scoring and ThreatConnect’s AI-driven intelligence summaries provide context on how this malware is delivered, its common TTPs, and its connection to previous campaigns.
Response: Automating Mitigation Actions
- ThreatConnect Playbooks automatically enrich the malware indicators, checking against existing threat data and known network activity.
- The SOC team receives an automated alert, and an analyst quickly cross-references intelligence using Polarity’s overlay inside their SIEM.
- With confirmed intelligence, the security team blacklists the malicious domains, hashes, and IPs across their security stack—stopping the attack before it can spread.
Continuous Intelligence: Learning & Refinement
- The incident is logged, and new intelligence from this attack is fed back into ThreatConnect, improving future detection and automation capabilities.
- ThreatConnect’s CAL provides community-driven insights, showing if similar attacks have been detected across other organizations.
With ThreatConnect and Recorded Future, the company stops a high-risk attack before it can cause damage, reducing manual effort and investigation time.
More Ways ThreatConnect and Polarity Accelerate Investigations
Beyond the Recorded Future Intelligence Engine, ThreatConnect and Polarity, provide even more capabilities to speed up investigations, enrich intelligence, and reduce alert fatigue.
Coupling ThreatConnect Clear Context with Polarity delivers real-time threat intelligence overlays inside your existing workflows without switching screens. More capabilities include:
- AI-Driven Intelligence Summaries – Instantly summarize threat reports and intelligence data with AI-powered analysis.
- Automated Playbooks – Respond automatically to threats by enriching data, triggering alerts, and applying defensive actions.
- Unified Threat Intelligence View – See all intelligence sources, risk scores, and relationships in one place.
- CAL-Powered Collective Insights – Use ThreatConnect’s CAL to identify patterns and common indicators across the security community.
With ThreatConnect and Polarity, security teams gain faster investigations, less manual effort, and more actionable intelligence—right when they need it most.
Security Teams, It’s Time to Work Smarter
Threat intelligence shouldn’t slow you down—it should help you move faster, with confidence. With ThreatConnect’s integrations, automation, and contextual overlays from Polarity, your team can stop chasing alerts and start making decisions with the right intelligence at the right time.
Want to see it in action? Get a demo today and start working smarter, not harder.

