Posted
The Return on Investment of any cybersecurity investment does not fall under the traditional definition of ROI. Cybersecurity is a pure cost center – in an average organization no revenue can ever be derived from it, and it represents a significant cost.
In order to calculate an ROI figure for such a cost center, we must turn the ROI calculation on its head. Which is to say, we must consider how much exposure the company will have to a cyber attack, and then look at how the likelihood of that exposure is reduced by the investment that is either being expended or considered.
As a security control, a Security Operations Center (SOC) is a component of the total security controls of the organization, and as such can be evaluated along the same lines as any other control, and in order to address this we need to understand what the SOC actually enables the organization to do.
In the best case, the SOC investigates and finds security issues, be it an attempted intrusion, or pre-emptive maintenance of infrastructure, or proactive security measures based on the information flowing through the SOC systems.
In the case where there is no SOC, the only proactive maintenance that goes on is conducted by the IT department. There are automated defense systems, some of which deploy signatures that are regularly updated, and some of which deploy heuristics and artificial intelligence. However, in this situation, there are only two possibilities – block or allow. There is no escalation route, and no capacity for further examination, meaning that the organization doesn’t have any means by which to investigate low-certainty security threats, and there is a whole swath of security measures that simply cannot be taken as they require active monitoring.
On the other side of the equation, cybersecurity threats may be broken down into two broad types: untargeted and targeted. In an untargeted attack, if a piece of malware is successful in gaining a foothold in an organization’s network, it was done through an autonomous process, exploiting a pre-determined workflow.
These untargeted attacks are the type of attack that purely automatic systems are able to handle to some extent — they look for known signatures, known behaviors and often use machine learning to extrapolate into the hypothetical. Yet, the threat of false positives and their impact on the usability of the infrastructure means that their settings are not as aggressive as may be required to pick up even some moderately advanced techniques.
The far more dangerous type of attack is the targeted attack, in which there is a team of attackers on the other side consciously investigating, moving around the network, laying the grounds for their intended action. In reality, in an increasing number of cases, this is actually a chain of attackers — one who gains access to the network, and then sells that access to another attacker who will actually perform the destructive part of the attack.
The recent ransomware attack on the Colonial Pipeline Company that took large parts of the East Coast of the U.S. back to the gasoline shortages of the 1970s has brought this into sharp relief. The attack, which took place using the DarkSide Ransomware as a Service was notable for its wide-ranging, real-world effects, but it also brought the phenomenon of credential marketplaces to prominence.
In an article published by Intel471 on May 10, 2021, they confirm:
For initial access to networks, actors usually purchased access credentials on underground forums, conducted brute-force attacks, used spam campaigns to spread malware loaders and/or bought access to popular botnets such as Dridex, TrickBot and ZLoader. As for post-exploitation tools, the arsenal usually included Cobalt Strike and Metasploit frameworks, Mimikatz and BloodHound.
An article from Krebs on Security goes even further in sharing screenshots of a conversation between DarkSide and one of their victims. A Bleeping Computer article from May 13, 2021 shares the image below, from a similar attack on Brenntag, a chemical distributor:
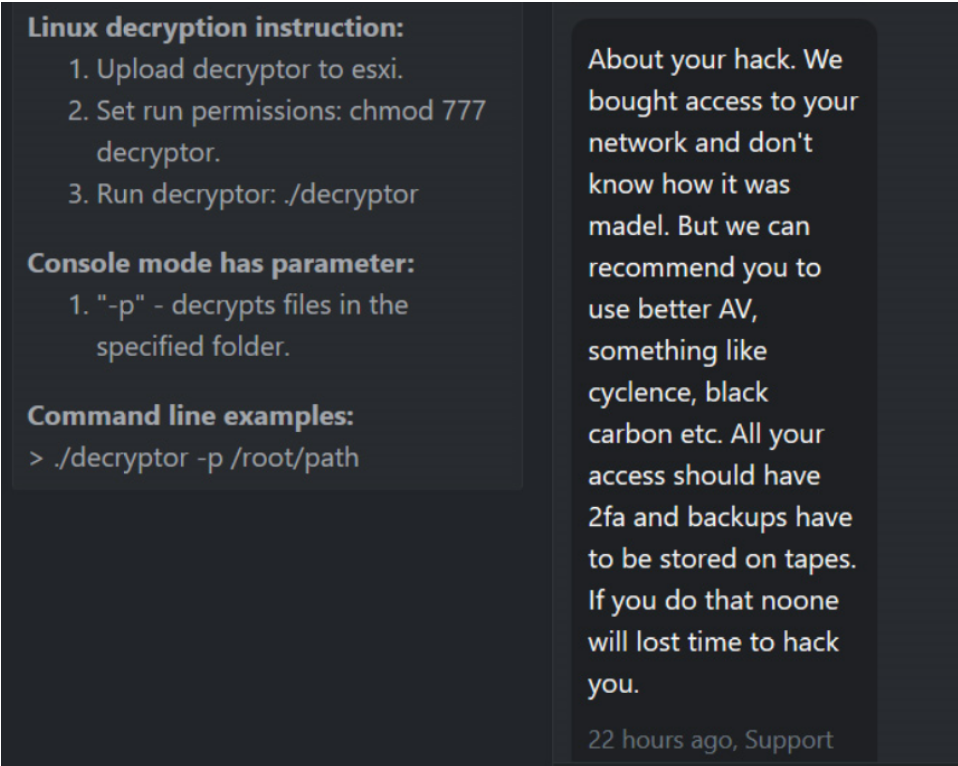
This conversation purports to be from DarkSide themselves, clearly stating that they bought access to the network, and have no idea how the intrusion was performed. In fact, some estimates have put billions of credentials available for sale on dark web marketplaces.
If automated security systems do not detect and prevent the initial access, then they are unlikely to prevent a potentially more sophisticated attacker from actually executing a disruptive attack.
With this in mind, the value of a SOC is to have the possibility of defending against this type of persistent threat. Each attack stage generates noise — from network traffic for command and control, to poisoned executables and libraries sitting on endpoints. If the attacker is even remotely sophisticated, the mechanics of exactly how they are controlling the intrusion, as well as how they are potentially spreading through the network or exfiltrating data may be hidden deep within intricacies of network protocols, which no automated system will be able to have sufficient certainty in its algorithms to say anything other than it should be investigated.
How to calculate an ROI figure
The first step in calculating any return on investment is to have metrics. ROI is a quantitative measure, and as such requires quantitative inputs to calculate.
The return on investment of a SOC, then, is in the ability to reduce the likelihood of this type of attack succeeding. To quantify this benefit, we need to understand two things at a quantitative level:
- The possible financial exposure to the organization
- How effective the SOC will be in defeating such attackers
Financial Exposure
There are many ways of calculating the possible loss exposure. Depending on how accurate you wish to be, there are statistical methods of calculating the maximum loss exposures that you have based on factors such as revenue, sales, cost of sales, cost of operations, number of confidential records, and many more factors that are contributory.
There are varying degrees of precision, and varying degrees of fidelity of the data input. The basic rule of thumb is that the more granular and accurate the data you input into the calculations, then the more granular and precise the output of the exposure will be.
With this information, the simplest solution to calculating the true loss exposure is to assume the worst possible outcome, and assume that the attacks will incur the maximum possible loss. This will produce the highest number, and therefore the highest ROI. There are more advanced models that look at the amount of loss triggered on a probabilistic basis.
Effectiveness
The effectiveness of a SOC in terms of quantifying its effectiveness is easier at the less precise end (every organization has a view of how well its SOC is performing, and every SOC manager should have quantitative metrics that they use in the day-to-day running of the department that they can publish for the purposes of this calculation.) The complexity comes in calculating how these metrics can be parlayed into metrics that could go into the calculation.
The best piece of advice would be, if you have no mechanism to quantitatively monitor the effectiveness of the SOC or any security control that you wish to measure the effectiveness of, start measuring the performance of the control, and then derive an effectiveness metric that can go into this calculation.
You can start at the blunt end of the metrics, and get a result that is prone to more uncertainty but is far better than no management information at all. As the need arises, the metrics can become more and more detailed, with more intricate models of effectiveness developed, until the organization is comfortable with the accuracy of the calculation.
The calculation of defense efficacy can get to be almost infinitely detailed, and the principle of diminishing returns most definitely applies. The organization will need to make the decision of ‘how much is enough.’ Understanding this efficacy (and via that the ROI), however, opens the doors for the organization to manage IT security in the same way that other business units are managed.
Conclusion
Calculating the ROI of any security control requires somewhat different thinking as it’s a cost center rather than a revenue generator, but it is absolutely possible. The SOC is no exception to this and is an important weapon in the war against the increasing cyber threats that a business faces.
In terms of operational security, listen to DarkSide. Two-factor authentication (2FA) will disarm the majority of credentials stolen and available on darknet marketplaces, and offline backups of critical data are out of reach of all but the most pernicious of attackers.
Measuring the ROI of any part of the security infrastructure is essential to effective and efficient management of the total IT security spend, and calculation is possible as long as the organization is gathering quantitative metrics.
ThreatConnnect’s product suite of TIP, SOAR, and RQ can help you with all aspects of the lifecycle of IT security, so if you need assistance in thinking about the risks that your organization faces, the threats that are testing your network security and defenses on a day-to-day basis, or the way your response to threats works, feel free to contact us.
