Posted
What’s in a Name… Server?
That which we call an APT. By any other name would smell as foul.
Read the full series of ThreatConnect posts following the DNC Breach: “Rebooting Watergate: Tapping into the Democratic National Committee“, “Shiny Object? Guccifer 2.0 and the DNC Breach“, “What’s in a Name Server?“, “Guccifer 2.0: the Man, the Myth, the Legend?“, “Guccifer 2.0: All Roads Lead to Russia“, “FANCY BEAR Has an (IT) Itch that They Can’t Scratch“, “Does a BEAR Leak in the Woods?“, “Russian Cyber Operations on Steroids“, and “Can a BEAR Fit Down a Rabbit Hole?“.
Following the lead from CrowdStrike, ThreatConnect expanded on the DNC Breach research looking at the name server hosting information for the misdepatrment[.]com spoofed domain.
Internet Contact Books
Name servers are the contact books of the Internet. A cell phone’s contact book gives someone the opportunity to forget their mom’s phone number because it automatically associates her name with her ten digit phone number. This way, after her information is in the contact book, they only have to remember her name to call her. Name servers provide a similar function – they translate domain names into difficult-to-remember IP addresses so we only have to remember the domain name. Note: the purpose of this post is not to be a DNS primer – you can learn more about DNS and how it works in this article.
Hosting services usually have their own name servers that they use for any websites that are registered through them. Also, hosting services generally use multiple name servers for their accounts to provide continuity in case one of their name servers goes down. For example, if five domains are registered through GoDaddy, all five of those domains by default will use GoDaddy name servers like NS1.GODADDY[.]COM and NS2.GODADDY[.]COM. Individuals can also choose to configure or transfer their domains so that they use other service providers’ name servers if they choose.
So What and Why You Care:
Hundreds of thousands of domains might use a single name server, but in some cases, especially for smaller hosting services, a name server may only be used for a couple of hundred domains. This can prove to be useful information as threats of all shapes and sizes – including advanced persistent threats (APTs) – will sometimes use boutique or smaller hosting services to register the domains that are used as malicious infrastructure in support of their operations. This name server information is contained in the WHOIS record for a domain and can potentially be used to identify other malicious domains that organizations may encounter related to a specific incident.
Name Servers, Bitcoins, and Bears. Oh My!
Following the lead from our friends at CrowdStrike, we expanded on the research we did into FANCY BEAR’s efforts against the DNC, where we took a look at the name server hosting information for the misdepatrment[.]com spoofed domain. Leveraging DomainTool‘s capabilities, we were able to identify that this domain was registered through the domains4bitcoins[.]com hosting service that allows customers to buy domain names with Bitcoins.
A hosting service like this is attractive to malicious actors that want to minimize the amount of attributable information that they are required to supply when purchasing domains. This service mitigates the need to supply credit cards and legitimate billing names and addresses, as the customer can simply pay from their Bitcoin wallet and use fictitious names and addresses that ultimately obfuscate their true ownership.
[av_button label=’White Paper: 6 Easy Ways to Advance Your Cybersecurity Program When You Have a Small Team’ link=’manually,http://hubs.ly/H03SMtB0′ link_target=’_blank’ size=’x-large’ position=’center’ icon_select=’yes’ icon_hover=’aviaTBicon_hover’ icon=’ue84d’ font=’entypo-fontello’ color=’theme-color’ custom_bg=’#444444′ custom_font=’#ffffff’ custom_class=” av_uid=’av-114dtyt’]
Some of the domains registered through this service, including misdepatrment[.]com, use multiple *.bitcoin-dns[.]hosting name servers. Using DomainTools’ Reverse NS lookup, we were able to identify about 1600 domains that also used the same name servers as misdepatrment[.]com. This set contains a wealth of domains that were previously identified as malicious, spoof or typosquat legitimate companies or organizations, or are otherwise suspicious.
Associations to Previous Activity
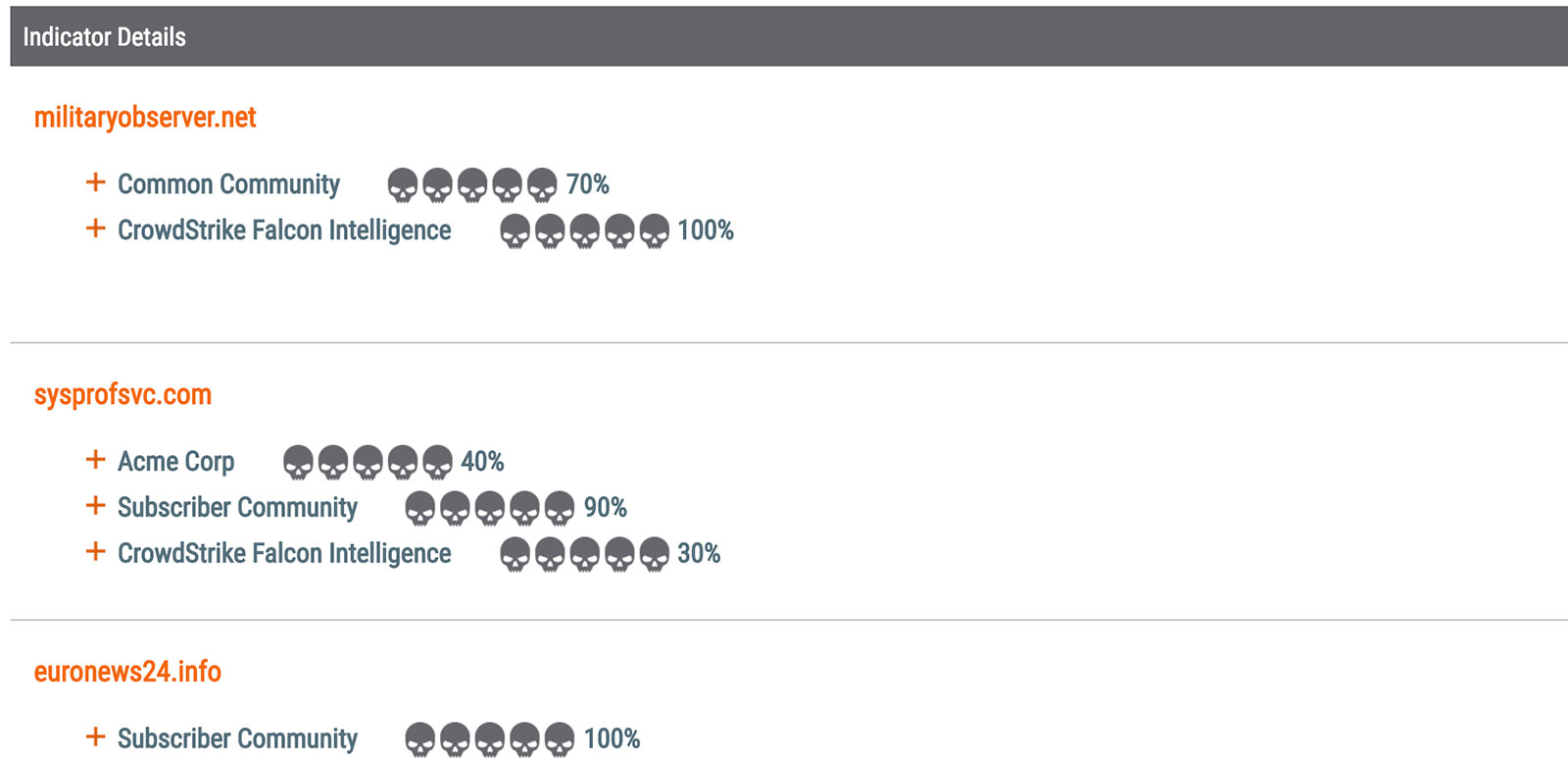
Leveraging ThreatConnect’s Analyze function, we were able to quickly identify the below domains that use domains4bitcoins[.]com’s name servers had been attributed to FANCY BEAR (aka APT28 and SOFACY) activity:
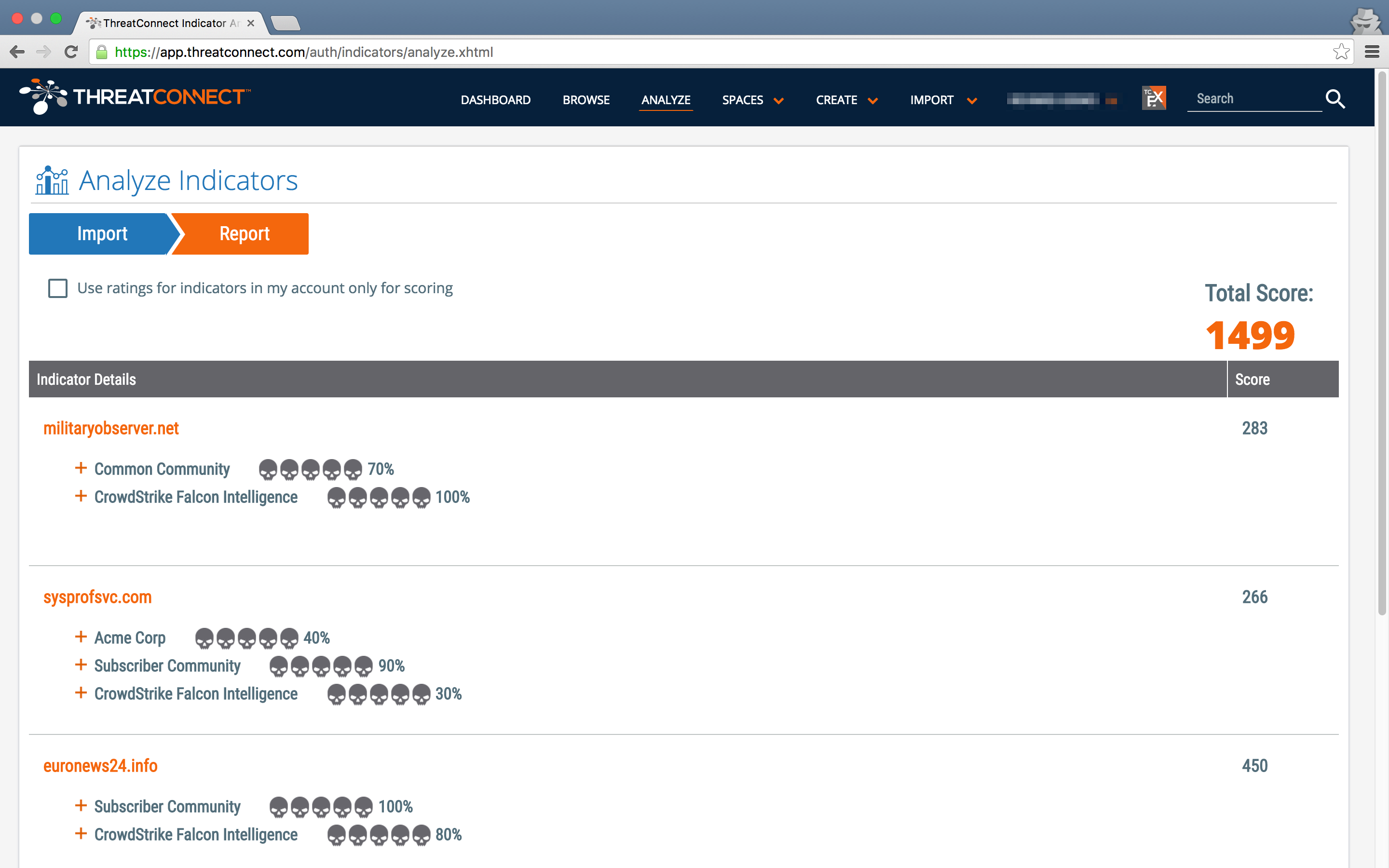
Analyze results for domains using the bitcoin-dns[.]hosting name server. Specific attributes below.
| Domain | Attributes |
| militaryobserver[.]net | FANCY BEAR related domains. From a PWC Threat Intelligence Bulletin. |
| sysprofsvc[.]com | Likely malicious FANCY BEAR C2 domain that overlaps with the domain winsyscheck[.]com at IP 69.90.132[.]194. |
| euronews24[.]info | Likely FANCY BEAR domain registered by leila77@cock[.]li |
| naoasch[.]com | FANCY BEAR callback found in DLL MD5: 2045EFB4DA99B3AF154814888BE43390 |
The presence of multiple domains attributed to an APT group on this relatively small Bitcoin name server underscores the fact that using such services is likely a common tactic for malicious actors who want avoid attribution and hosting services that mitigate abusive activity. Paying in bitcoins also lessens any hassles an APT might experience in trying to register domains using foreign currency.
Criminal actors leveraging recent ransomware variants, including Locky and SamSam, request ransom payments in Bitcoins from their victims. The malicious actors can then use these Bitcoin hosting services to easily procure additional anonymous infrastructure using their ransom money. Several of the domains registered through domains4bitcoins[.]com spoof Bitcoin-related websites. For example, blockichain[.]info spoofs the Bitcoin wallet site blockchain[.]info, which has previously been spoofed in multiple phishing efforts. One possibility is that the individuals behind these operations may be using stolen Bitcoins to “feed the beast” and use stolen digital currency to procure digital infrastructure in support of future operations.
Additional Shadiness
We further reviewed the domains using domains4bitcoins[.]com’s name servers and are sharing over 400 of them in 20160616B: Suspicious Domains on Bitcoin DNS Nameservers. Some of the more notable domains mirror government organizations, media outlets, and technology companies or tools. Many of these organizations are ubiquitous and domains spoofing them could be used against a variety of targets:
| Domain | Possible Spoofed Organization |
Create/Update Date |
Expiration Date |
SOA Email | Registrant Email |
| adobeflashdownload[.]de | Adobe | 11/16/15 | N/A | j.wang@uymail.com | N/A |
| adobeflashplayer[.]me | Adobe | 2/18/16 | 2/18/17 | play@xtcmail.com | contact@privacyprotect.org |
| adobeflashplayer[.]space | Adobe | 2/18/16 | 2/18/17 | play@xtcmail.com | contact@privacyprotect.org |
| adobeupdater[.]org | Adobe | 8/10/15 | 8/10/16 | vrickson@mail.com | vrickson@mail.com |
| adobeupdatetechnology[.]com | Adobe | 5/30/16 | 5/30/17 | best.cameron@mail.com | best.cameron@mail.com |
| adoble[.]net | Adobe | 4/22/16 | 4/22/21 | surleoborden@gmail.com | contact@privacyprotect.org |
| flashplayer2015[.]xyz | Adobe | 12/17/15 | 12/17/16 | N/A | josiekilbyav@aol.com |
| newflashplayer2015[.]xyz | Adobe | 12/18/15 | 12/18/16 | N/A | josiekilbyav@aol.com |
| pdf-online-viewer[.]com | Adobe | 12/11/15 | 12/11/16 | weronika76@hotmail.com | weronika76@hotmail.com |
| yourflashplayer[.]xyz | Adobe | 12/19/15 | 12/19/16 | josiekilbyav@aol.com | josiekilbyav@aol.com |
| akamaitechnologysupport[.]com | Akamai | 5/27/16 | 5/27/17 | bergers3008@usa.com | bergers3008@usa.com |
| akamaitechupdate[.]com | Akamai | 6/21/16 | 6/21/17 | guiromolly@mail.com | guiromolly@mail.com |
| helper-akamai[.]com | Akamai | 5/25/16 | 5/25/17 | N/A | 8yhi4xqycpzm@mail.ru |
| cdncloudflare[.]com | Cloudflare | 1/16/16 | 1/16/19 | loots@tuta.io | loots@tuta.io |
| cloudfiare[.]com | Cloudflare | 11/3/15 | 11/3/16 | mia.konzet99@ok.de | mia.konzet99@ok.de |
| egypressoffice[.]com | Egy Press | 9/7/15 | 9/7/16 | dana.raphaela@chewiemail.com | dana.raphaela@chewiemail.com |
| access-google[.]com | 6/22/15 | 6/22/16 | abuse@opticaljungle.com | v9sa2cml@instancemail.net | |
| cdn-google[.]com | 5/2/16 | 5/2/17 | issacgolden@hmamail.com | contact@privacyprotect.org | |
| marshmallow-google[.]com | 5/19/16 | 5/19/17 | gregorio.oconnor@hmamail.com | contact@privacyprotect.org | |
| terms-google[.]com | 12/22/15 | 12/22/16 | artur.klimenkov@gmail.com | artur.klimenkov@gmail.com | |
| honeyvvell[.]co | Honeywell | 2/17/16 | 2/16/17 | pinfiangtw@gmail.com | pinfiangtw@gmail.com |
| thehufflngtonpost[.]com | Huffington Post | 11/10/15 | 11/10/16 | mattew.barnes@aol.com | contact@privacyprotect.org |
| intelintelligence[.]org | Intel | 2/11/16 | 2/11/17 | petkrist@myself.com | petkrist@myself.com |
| intelsupportcenter[.]com | Intel | 2/17/16 | 2/17/17 | fisterboks@email.com | fisterboks@email.com |
| intelsupportcenter[.]net | Intel | 2/17/16 | 2/17/17 | fisterboks@email.com | fisterboks@email.com |
| micoft[.]com | Microsoft | 8/8/15 | 8/8/16 | syst.soul@mail.com | syst.soul@mail.com |
| microsoft-updates[.]me | Microsoft | 10/7/15 | 10/7/17 | m8r-abrn11@mailinator.com | contacts@up57893.in |
| ms-drivadptrwin[.]com | Microsoft | 2/24/16 | 2/24/17 | mr.michoverton@mail.com | mr.michoverton@mail.com |
| ms-sus6[.]com | Microsoft | 4/14/16 | 4/14/17 | ken.tanaka@mail.com | contact@privacyprotect.org |
| ms-updates[.]com | Microsoft | 12/17/15 | 12/17/16 | sandra.rafaela@chewiemail.com | sandra.rafaela@chewiemail.com |
| securesystemwin[.]com | Microsoft | 5/22/15 | 5/22/17 | bkopfer7101@mail.com | contact@privacyprotect.org |
| win-wnigarden[.]com | Microsoft | 11/25/15 | 11/25/16 | pinfiangtw@gmail.com | pinfiangtw@gmail.com |
| wincodec[.]com | Microsoft | 12/14/15 | 12/14/16 | elfreda.pollie@chewiemail.com | elfreda.pollie@chewiemail.com |
| windowsnewupdated[.]com | Microsoft | 7/2/15 | 7/2/16 | ruzeedomeon@gmail.com | contact@privacyprotect.org |
| winliveupdate[.]top | Microsoft | 2/24/16 | 2/24/17 | agnasirahmedd@gmail.com | agnasirahmedd@gmail.com |
| winninggroup-sg[.]com | Microsoft | 4/21/16 | 4/21/17 | s.penn.254@gmail.com | s.penn.254@gmail.com |
| wm-z[.]biz | Microsoft | 2/20/10 | 2/19/17 | j.holmberg@dr.com | admin@wm-z.biz |
| wmepadtech[.]com | Microsoft | 7/22/15 | 7/22/16 | shawanda.kirlin37@mail.com | shawanda.kirlin37@mail.com |
| nato-org[.]com | NATO | 2/18/16 | 2/18/17 | barry.smith2004@yandex.com | barry.smith2004@yandex.com |
| natoadviser[.]com | NATO | 5/24/16 | 5/24/17 | leo.link@email.com | leo.link@email.com |
| sec-verified[.]com | SEC | 8/3/15 | 8/3/16 | cjgr8hm@gmail.com | cjgr8hm@gmail.com |
| theguardiannews[.]org | The Guardian | 12/10/15 | 12/10/16 | idolbreaker@mail.com | idolbreaker@mail.com |
| theguardianpress[.]com | The Guardian | 12/9/15 | 12/9/16 | paulbecker@cock.li | paulbecker@cock.li |
| services-gov[.]co[.]uk | UK Govt | 1/17/16 | 1/17/17 | saira.samosa@gmail.com | N/A |
| goaarmy[.]org | US Army | 8/16/05 | 8/16/16 | owen@kehoe.org | owen@kehoe.org |
| govsh[.]net | US Govt | 8/5/15 | 8/5/16 | noshare1024@gmail.com | contact@privacyprotect.org |
| wsjworld[.]com | WSJ | 3/16/16 | 3/16/17 |
mishel_corp@mail.com | mishel_corp@mail.com |
Some notable patterns stick out from the above list with respect to previously-attributed activity. Theguardianpress[.]com domain was registered using the same email domain, cock[.]li, as the naoasch[.]com and euronews24[.]info domains that were previously attributed to FANCY BEAR activity. This domain was also registered in the same timeframe as another domain, theguardiannews[.]org, which also spoofs The Guardian. Leveraging the Reverse DNS capability within the ThreatConnect platform, we are also able to quickly identify that four of the domains–adoble[.]net, wincodec[.]com, theguardiannews[.]org, and theguardianpress[.]com–previously resolved to the 5.135.183[.]154 IP address. These domains are now hosted elsewhere, with The Guardian-spoofing domains being hosted on dedicated servers. The 5.135.183[.]154 IP also hosted the misdepatrment[.]com domain before it was potentially used in the DNC attack from a dedicated server at the FANCY BEAR 45.32.129[.]185 IP identified by CrowdStrike.
The adobeupdater[.]org domain was registered by the same email, vrickson@mail[.]com, that was used to register the FANCY BEAR-attributed domain ssl-icloud[.]com. Finally, two domains spoofing Intel and one spoofing Honeywell were all registered on February 17, 2016.
[av_button label=’White Paper: Maturing a Threat Intelligence Program’ link=’manually,http://hubs.ly/H03SNJh0′ link_target=’_blank’ size=’x-large’ position=’center’ icon_select=’yes’ icon_hover=’aviaTBicon_hover’ icon=’ue84d’ font=’entypo-fontello’ color=’theme-color’ custom_bg=’#444444′ custom_font=’#ffffff’ custom_class=” av_uid=’av-i7znud’]
It is important to note that we cannot immediately confirm that these domains are hosting malware or are otherwise attributable to malicious APT activity; however, they deserve additional scrutiny due to the patterns identified above, the fact that they use a Bitcoin name server, and that they emulate legitimate organizations. The Start of Authority (SOA) and WHOIS records for these domains confirm that they were not registered by the spoofed organization. Setting alerting capabilities to identify domains that use a bitcoin name server AND were registered using a free webmail account (such as chewiemail[.]com or mail[.]com) may provide an organization with more specific alerts that are useful for both analytic and defensive efforts.
Many of these domain squats are consistent with those that APT actors leverage in their operations, including those targeting NATO, news websites, or Intel. After registering domains like these, APTs can quickly use them in multiple phases of their operation ranging from delivery to command and control.
Previous FANCY BEAR Name Server Activity
This isn’t the first time that various FANCY BEAR infrastructure has leveraged the same technique and used smaller name servers. We reviewed a report from Trend Micro that detailed some domains that had been used in previous FANCY BEAR attacks. Four of the eight domains detailed in the report were likely registered using the same hosting services. These domains initially used the same XtraOrbit name server and later transferred to another XtraOrbit name server before they were published in the report:
| Domain | Initial Name Server | Second Name Server |
| vice-news[.]com | xtraorbit[.]com | xo.earth.orderbox-dns.com |
| eurosatory2014[.]com | xtraorbit[.]com | xo.earth.orderbox-dns.com |
| webmail-saic[.]com | xtraorbit[.]com | xo.earth.orderbox-dns.com |
| natoexhibitionff14[.]com | xtraorbit[.]com | xo.earth.orderbox-dns.com |
| tolonevvs[.]com | carbon2u[.]com | Parked after report |
| mail.hm.qov[.]hu | N/A | N/A |
| log-in-osce[.]org | N/A | N/A |
| academl[.]com | trademarkarea[.]com | Parked after report |
Leveraging DomainTools, we were able to identify that only 466 domains currently use the xtraorbit[.]com name server. Then using ThreatConnect’s Analyze function, we were able to identify that at least 17 of those domains had been attributed to FANCY BEAR. The concentration of malicious domains on this name server again demonstrates that analysis of name servers can facilitate analytic efforts against such APT groups.
Conclusion
Bitcoin hosting services and name servers are not limited to what we showed here. In the course of our research, we identified at least three other distinct name servers that were dedicated to bitcoin hosting services: domains4bitcoins.*.orderbox-dns[.]com, *.domains4bitcoins[.]com, and *.domains4bitcoins-parking[.]com. Some domains associated with these name servers were also incorporated into 20160616B: Suspicious Domains on Bitcoin DNS Nameservers.
Also, shady name server activity isn’t restricted to bitcoin services. We identified other name servers hosting a concentration of malicious APT domains. And, as more domains are registered through services like these or transferred to these name servers on a daily basis, it is worthwhile to monitor such activity and incorporate it into your organization’s analytic and defensive efforts.
Read the full series of ThreatConnect posts following the DNC Breach: “Rebooting Watergate: Tapping into the Democratic National Committee“, “Shiny Object? Guccifer 2.0 and the DNC Breach“, “What’s in a Name Server?“, “Guccifer 2.0: the Man, the Myth, the Legend?“, “Guccifer 2.0: All Roads Lead to Russia“, “FANCY BEAR Has an (IT) Itch that They Can’t Scratch“, “Does a BEAR Leak in the Woods?“, “Russian Cyber Operations on Steroids“, and “Can a BEAR Fit Down a Rabbit Hole?“.