Posted
Today’s post continues an ongoing series on Polarity Security Operations Center (SOC) use cases; demonstrating how Polarity helps you to see the story in your data without sacrificing thoroughness or speed.
Incident Responders are often relegated to working in an environment where communication channels are compromised or non-existent. Real time information of the environment is often unavailable or lost. SOC operators continue to monitor the available infrastructure and are relegated to data sharing via Email or phones.
Capabilities:
Polarity enables real time collaboration and knowledge management between IR and SOC teams through Channels and Annotations.
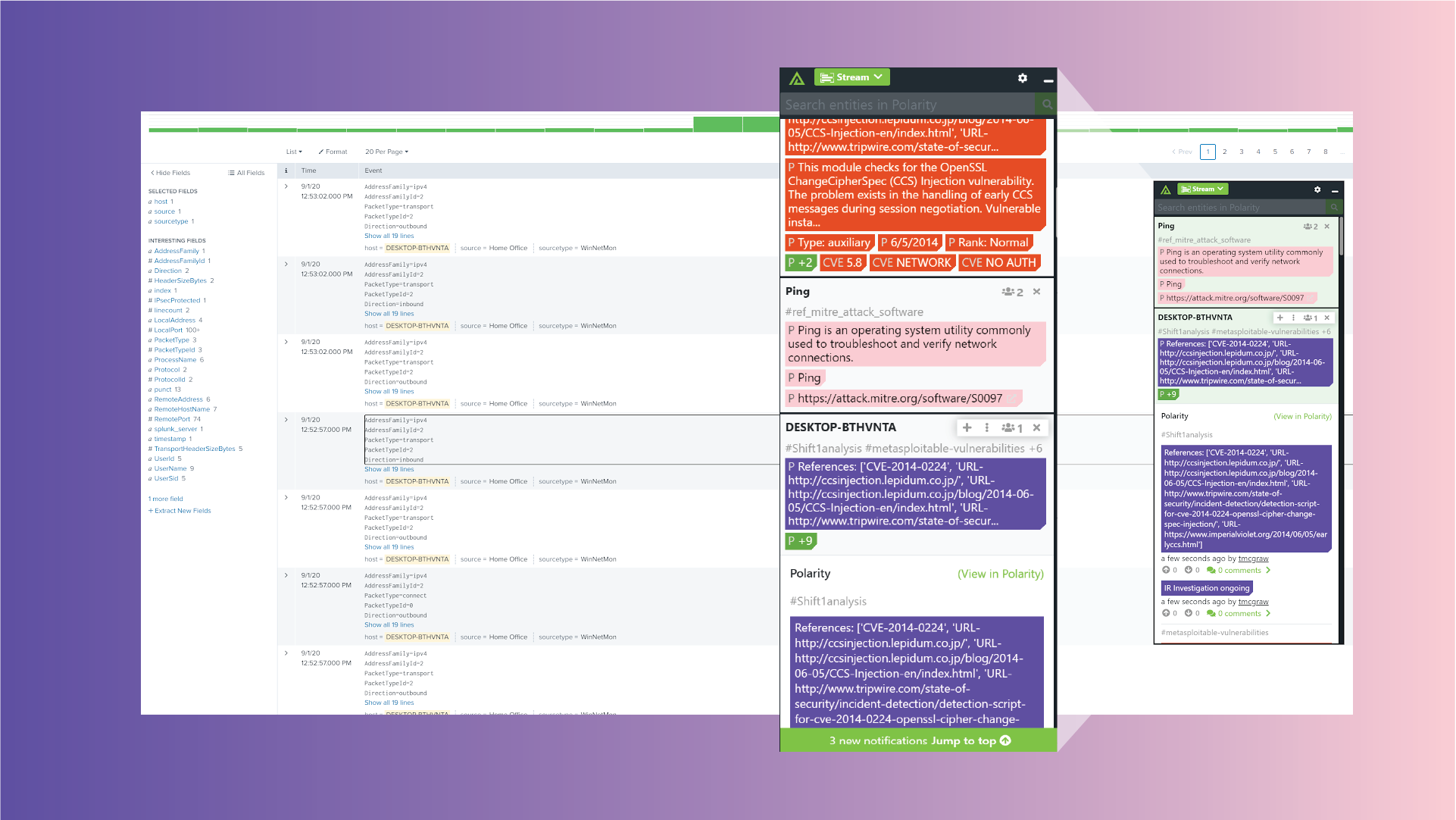
Noticed the highlighted text in the above images. You can see that Polarity’s computer vision recognized the text on screen, and in real-time while the analyst is working, it has provided contextual information for the highlighted data in the Overlay Window. This contextual information has been pulled from a variety of Polarity annotations (made by the analyst’s teammates) and reference channels (shared throughout the analysts’ team), including MITRE and Shift 1 Analysis, allowing the analyst to immediately see contextual information from both SOC and IR teams.
In this example an analyst is triaging events and the HUD alerts them to the fact that this customer and this device in particular are part of an ongoing IR investigation. Additionally, context around what is known about the exploit in question is presented immediately and all channels for other shifts have this data presented in real time should they also have event data from this customer or device.

Real time SOC and IR Team awareness and collaboration provide:
- The ability for the SOC team to know when an IR team has engaged with a customer or portion of the network architecture.
- Visibility into what actions the IR team is conducting.
- Sharing of additional SOC event and incident information with the team trying to evict the adversary and remediate the network.
- Helping the IR team to see if what they are viewing is a diversion or the main effort as the feeds in the SOC share additional event triage data.
Meet the expert: Terry McGraw

Background: Terrence “Terry” McGraw is a retired Lieutenant Colonel from the United States Army and now serves as the President and principal consultant, of Cape Endeavors, LLC, with over 20 years of providing expertise in cyber security architectural design and operations in both commercial and government sectors.
Terry previously served as the Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks and President of PC Matic Federal. He retired from the United States Army in 2014 completing 27 years of service; the last 10 years of his Army career were leading key Cyber initiatives for the Army’s Network Enterprise and Technology Command, Army Cyber Command and the National Security Agency (NSA). He has multiple combat tours with his culminating assignment, serving as the Director of Operations, Task Force Signal Afghanistan, 160th Signal Brigade (FWD), providing all strategic communications infrastructure in the theater of operations.
Education: BA in History, MSA in Information Systems Engineering, and a graduate of the prestigious US Army School of Information Technology’s Telecommunication Systems Engineering Course.
Relevant Experience: Terry’s work in the Army leading and operating some of the world’s largest and most complex networks as well as 6 years as Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks providing managed cyber security services to over 4,000 commercial clients and leading it’s six Counter Threat Operations Centers gives him a deep and broad understanding of the Cyber Threat Landscape. His entire professional career has been in designing and managing resilient network architectures ensuring the operational readiness thereof.

