Posted
Today’s post continues an ongoing series on Polarity Security Operations Center (SOC) use cases; demonstrating how Polarity helps you to see the story in your data without sacrificing thoroughness or speed.
According to IBM’s X-Force and Dell Secureworks, Phishing attacks have been the top initial compromise of all breach vectors (i.e. approximately 30%) for the last few years.
Triaging phishing attacks is time-consuming and tedious, but Polarity makes it a snap.
The first step in analyzing if an email is legitimate, spam, or malicious, begins with examining the header data for source information by inspecting IP addresses and domains.
Once an analyst has pulled the email header data they must scan the header for IPs and domains to complete a reputational analysis by searching external data repositories for a reputational score or data provenance (e.g. from which country did the email originate, who owns the URL, and has it been associated with any malicious activity).
A considerable amount of time is spent searching data before a decision can be made. Once all of the header data has been examined, the analyst can finally make a determination on whether the email is malicious as well as its degree of maliciousness. Because an analyst has the obligation to be as thorough as possible, several searches against different data repositories must be undertaken to make a truly informed decision.
If the email is determined to be a true security incident requiring an actual Incident Response, an analyst’s first reaction is very likely to conduct a further assessment of battle damage before blocking the associated activity. The analyst will attempt to answer questions including: is this a targeted campaign, who are the actors, what was affected? Each of these questions require varying degrees of data lookups from numerous sources.
Polarity has multiple resources to help analysts determine the reputational value of email header data when conducting a phishing triage.
Capabilities
- Polarity can augment the analyst view with information sourced directly from several domain intelligence platforms. Examples of integrations with free sources include:
- URLScan
- URLHaus
- VirusTotal
- Shodan
- MaxMind
- Majestic Millions
- Polarity can also overlay open-source and commercial threat intelligence that is specific to the domain.
- Polarity can provide a quick snapshot of the URL in question from URLScan and share it in the Heads Up Display (HUD).
- Polarity ensures that the most recent information is pulled, not just the information that was pulled at the time of ingestion.
- Polarity automatically demonstrates historical relationships between the enterprise and the domain (e.g. via an immediate query to proxy logs).
- Polarity highlights whether the IP addresses associated with the domain have been observed from enterprise firewalls.
- With channels or integrations, Polarity can show linkage of the business relationships between the domain and the enterprise (e.g. Entity: “Polarity.io” Annotation: “Is a trusted partner.”).
- Polarity can also initiate actions against domains. For example:
- If integrations support scan requests (e.g. URLScan), scans can be kicked off.
- If SOAR playbooks exist, drive-by simulations may be initiated.
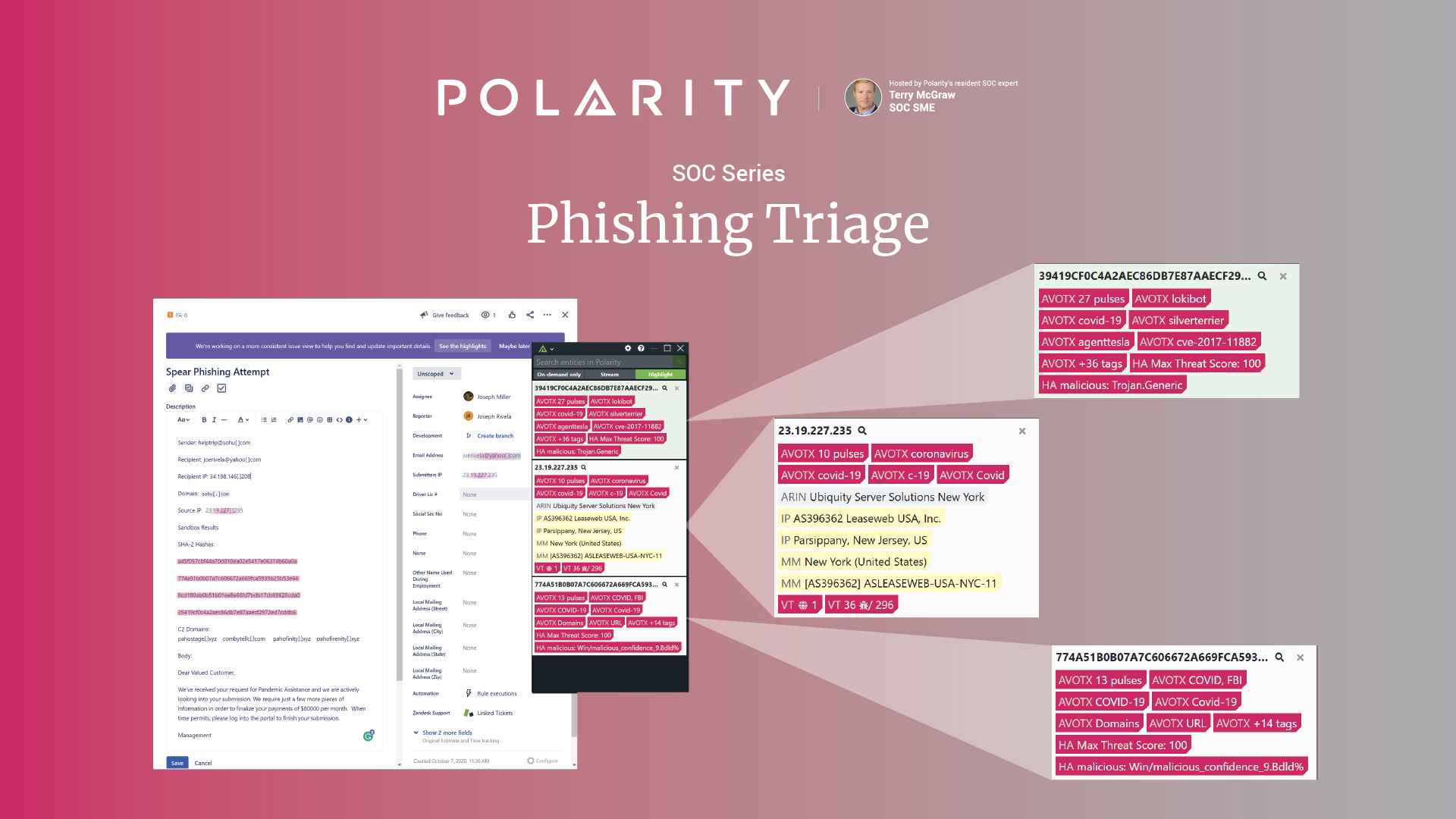
As shown in the images above, Polarity shares real-time reputational data derived from a number of authoritative IP and domain provenance services. Here we show information provided by Shodan, Virus Total, URLhaus, and MaxMind. These repositories and any other data feed you are subscribed to or use frequently can be provided to your analysts in real-time, with no lookups, no clicking around, no shifting tabs, and no cutting and pasting. Polarity provides information when you need it and where you need it. You are threat hunting – you shouldn’t have to hunt for your data too.
Meet the expert: Terry McGraw

Background: Terry is Head of Customer Success for Polarity and serves as our resident expert in Security Operations and Cyber Threat Analysis. He is a retired Lieutenant Colonel from the United States Army and has over 20 years of providing expertise in cyber security architectural design and operations in both commercial and government sectors.
Terry previously served as the Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks and President of PC Matic Federal. He retired from the United States Army in 2014 completing 27 years of service; the last 10 years of his Army career were leading key Cyber initiatives for the Army’s Network Enterprise and Technology Command, Army Cyber Command and the National Security Agency (NSA). He has multiple combat tours with his culminating assignment, serving as the Director of Operations, Task Force Signal Afghanistan, 160th Signal Brigade (FWD), providing all strategic communications infrastructure in the theater of operations.
Education: BA in History, MSA in Information Systems Engineering, and a graduate of the prestigious US Army School of Information Technology’s Telecommunication Systems Engineering Course.
Relevant Experience: Terry’s work in the Army leading and operating some of the world’s largest and most complex networks as well as 6 years as Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks providing managed cybersecurity services to over 4,000 commercial clients and leading it’s six Counter Threat Operations Centers gives him a deep and broad understanding of the Cyber Threat Landscape. His entire professional career has been in designing and managing resilient network architectures ensuring the operational readiness thereof.
