Posted
Today’s post continues an ongoing series on Polarity Security Operations Center (SOC) use cases; demonstrating how Polarity enables you to see the story in your data without sacrificing thoroughness or speed.
To understand the operational impact of malicious activity on the network, a SOC analyst must be able to determine not only what function an affected device(s) plays in the architecture, but who has access to it and when they last accessed it. Containment, Incident Response Actions and Battle Damage Assessments, all require an understanding of who accessed a device, and when. Were user privileges escalated and if so, when, and for what user? Polarity enables visibility into user profiles and other attributes commonly viewed within log analysis tools, SIEMs, SOARs or other workflow events – well beyond what is included in existing workflow platforms.
Capabilities
- Polarity can overlay user information sourced from LDAP platforms.
- Polarity can provide insights into historical user tickets (e.g. user deprovisioning requests overlaid on a successful authentication event).
- Polarity can overlay the risk exposure of a user. This can be sourced from either:
- Public sources that associate the user’s information to data loss events (e.g. immediate references against https://haveibeenpwned.com).
- Data Loss Prevention (DLP) event logs.
- Insider threat management systems “base risk” scores.
- Insider threat management system baselines.
- Polarity can overlay VPN log events to allow the analyst to determine the region the user has logged in from.
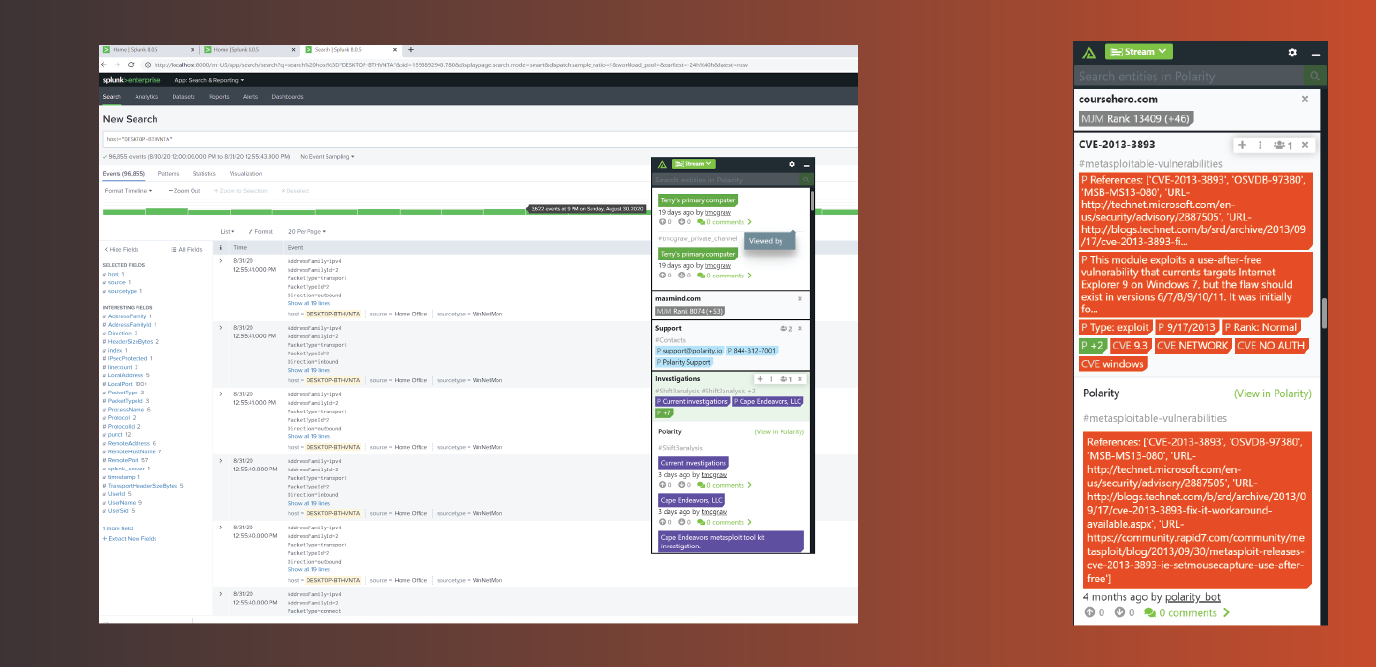
Screenshot from the Polarity platform’s Heads Up Display (HUD).
As shown in the above diagram, the Polarity platform provides real time user and object identity data derived from sources such as Active Directory, a SIEM or Access logs. In this constructed example you can see that my computer hostname immediately populates the Polarity HUD identifying this as my primary work computer. It belongs to Cape Endeavors, LLC and it has been part of an active metasploit toolkit investigation.
Identity information can come from integrations such as Splunk, Phantom, Cortex xSOAR, LDAP, Windows logs, and ticketing services such as ServiceNow, Zen, Service Desk Plus, Zen Desk, etc. If the integration you need isn’t already available our GitHub page, you can build your own or ask for our assistance. All of our integrations are open source under MIT license, customizable and shareable.

Real time user identity and object awareness in Polarity has several benefits including:
- Analysts can make much more informed decisions regarding the true severity of an event based on the contextual user information that is overlaid on their screen.
- Correlations that might not have otherwise been possible, or possible only with significant ETL, development, and more mouse clicks, are now available on the fly.
Meet the expert: Terry McGraw

Background: Terrence “Terry” McGraw is a retired Lieutenant Colonel from the United States Army and now serves as the President and principal consultant, of Cape Endeavors, LLC, with over 20 years of providing expertise in cyber security architectural design and operations in both commercial and government sectors.
Terry previously served as the Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks and President of PC Matic Federal. He retired from the United States Army in 2014 completing 27 years of service; the last 10 years of his Army career were leading key Cyber initiatives for the Army’s Network Enterprise and Technology Command, Army Cyber Command and the National Security Agency (NSA). He has multiple combat tours with his culminating assignment, serving as the Director of Operations, Task Force Signal Afghanistan, 160th Signal Brigade (FWD), providing all strategic communications infrastructure in the theater of operations.
Education: BA in History, MSA in Information Systems Engineering, and a graduate of the prestigious US Army School of Information Technology’s Telecommunication Systems Engineering Course.
Relevant Experience: Terry’s work in the Army leading and operating some of the world’s largest and most complex networks as well as 6 years as Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks providing managed cyber security services to over 4,000 commercial clients and leading it’s six Counter Threat Operations Centers gives him a deep and broad understanding of the Cyber Threat Landscape. His entire professional career has been in designing and managing resilient network architectures ensuring the operational readiness thereof.

