Posted
Today’s post continues an ongoing series on Polarity Security Operations Center SOC) use cases; demonstrating how Polarity augments analysts for superhuman speed and thoroughness.
Hash values can help verify whether activity found within logs has already been determined as a “known-bad” and can be used to correlate activity between network devices and netflows. These are somewhat ephemeral, so it can be hard to maintain currency and consistency of correlation with them. Polarity enables real-time analysis of hashes that are present and displayed across workflow systems or captured as part of isolated information security events.
Capabilities:
- Polarity overlays information sourced from public repositories regarding the malicious or non-malicious nature of the hash.
- Polarity overlays open source and commercial threat intelligence over a hash as it is displayed on a screen. In security operations this can be access controlled to read-only.
- Polarity can overlay internal information related to the hash that an analyst might be re-reviewing. For example:
- Collisions with “known-good” hashes
- Historically reported false positives
- Procedures associated with handling the hash
- Polarity allows for immediate reference against a gold-build hash set.
- Analysts can leverage Polarity to contribute to internal databases of known hashes.
- Polarity allows for immediate retrieval of historical events associated with the hash that are present within connected logging or log consolidation / aggregation platforms.
- Polarity can initiate submissions of hashes to platforms (e.g. sandboxes) for analysis.
- Polarity will automatically query Endpoint Detection and Response platforms to determine if the hash is within an enterprise.
- Jointly with integrated SOAR platforms, Polarity will initiate pre-defined containment activities.
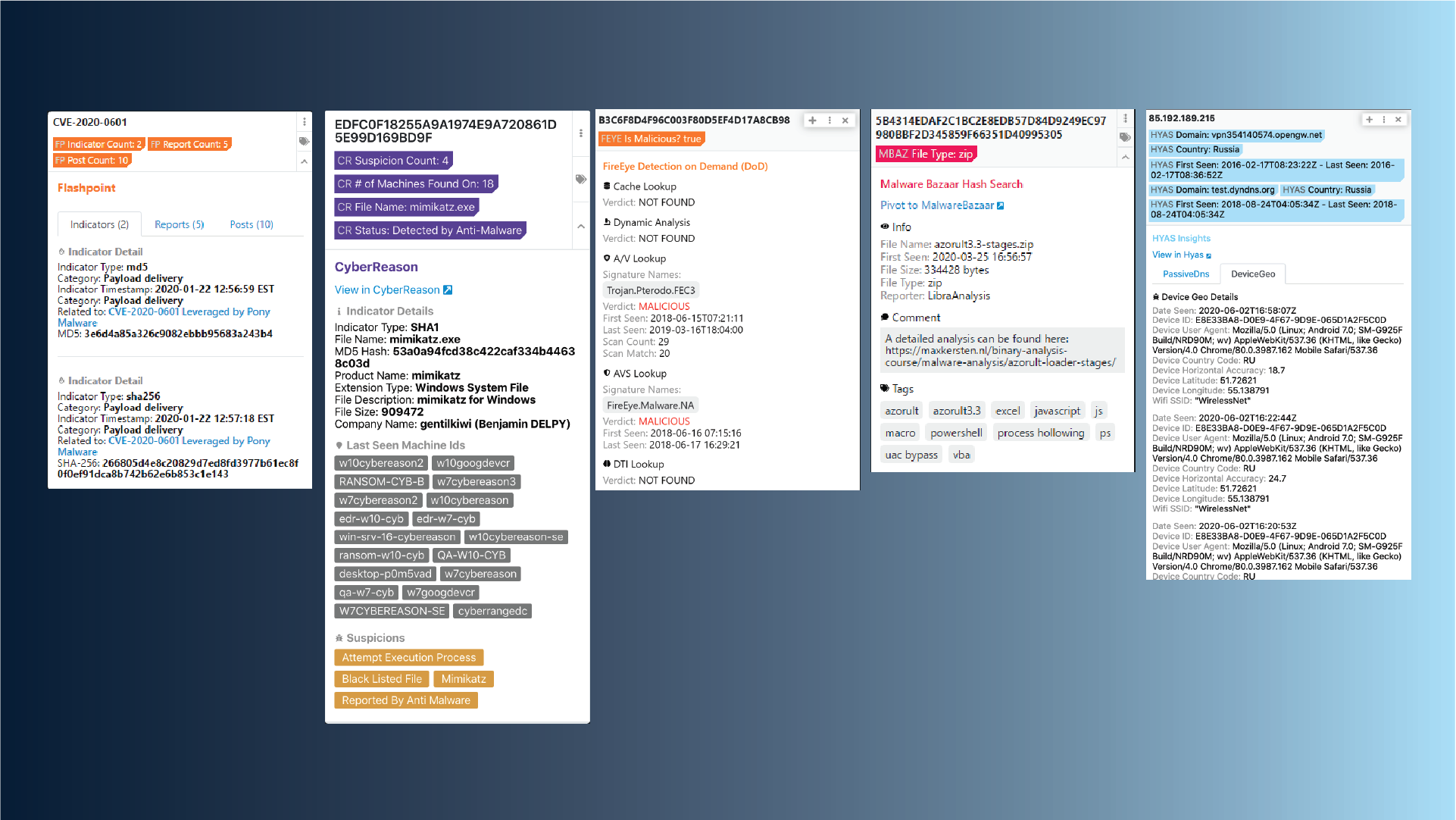
It is unrealistic to assume that a normal analyst, and by normal I mean one that doesn’t live in the Marvel Universe or has a photographic memory, can recall hash values on demand. Polarity gives analysts superpowers by providing instant recall of hash reputational data. What does this hash represent? Where has it been seen in my environment? What was the traffic associated with it? These are critical questions, and also time consuming to answer. Analysts spend much of their time gathering data to make a determination about what to do next. Polarity gives analysts data and information immediately so they can make informed decisions with speed and thoroughness.
In the example above, we show several tools common in SOCs that would normally be open in different portals, different tabs or different systems. With Polarity information is overlaid next to whatever the analyst is working on eliminating the need to swivel between screens.
Real Hash Value awareness in Polarity has several benefits including:
- Earlier identification of malicious or potentially malicious hashes
- Immediate understanding of the presence a hash or lack thereof in the enterprise
- Immediate understanding of historical events involving the observed hashes
- Avoidance of costly investigations into previously investigated or benign hashes
Meet the expert: Terry McGraw

Background: Terrence “Terry” McGraw is a retired Lieutenant Colonel from the United States Army and now serves as the President and principal consultant, of Cape Endeavors, LLC, with over 20 years of providing expertise in cyber security architectural design and operations in both commercial and government sectors.
Terry previously served as the Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks and President of PC Matic Federal. He retired from the United States Army in 2014 completing 27 years of service; the last 10 years of his Army career were leading key Cyber initiatives for the Army’s Network Enterprise and Technology Command, Army Cyber Command and the National Security Agency (NSA). He has multiple combat tours with his culminating assignment, serving as the Director of Operations, Task Force Signal Afghanistan, 160th Signal Brigade (FWD), providing all strategic communications infrastructure in the theater of operations.
Education: BA in History, MSA in Information Systems Engineering, and a graduate of the prestigious US Army School of Information Technology’s Telecommunication Systems Engineering Course.
Relevant Experience: Terry’s work in the Army leading and operating some of the world’s largest and most complex networks as well as 6 years as Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks providing managed cyber security services to over 4,000 commercial clients and leading it’s six Counter Threat Operations Centers gives him a deep and broad understanding of the Cyber Threat Landscape. His entire professional career has been in designing and managing resilient network architectures ensuring the operational readiness thereof.