Posted
Today’s post continues an ongoing series on Polarity Security Operations Center (SOC) use cases; demonstrating how Polarity helps you to see the story in your data without sacrificing thoroughness or speed.
Understanding asset criticality, function, and location are absolutely critical when triaging an event to determine whether or not it is an actual incident requiring immediate response. All too often this requires an analyst to pivot from their investigation platform into an asset database, spreadsheet, or some other knowledge repository to make this determination and then pivot back into the investigation platform to take next steps.
Polarity obviates this challenge by either integrating directly to your asset database store or one can simply upload critical assets right into Polarity from a .csv file. We can do this in 4 easy steps.
First a word about how the data in the .csv file is presented. The first column in your .csv file will be designated as the “entity” or the text to be searched on your screen, and all additional columns will be added as annotations.
Step 1
Open the Polarity Main page and click the large green rectangular button labeled “Annotate’.
Step 2
Click the .csv hyperlink at the top of the window and select the .csv file you wish to upload.
Step 3
Select a channel you wish to subscribe the data to, or create a new Channel on the fly under the Channels Dropdown menu and then finish with the Green “Annotate” button and if everything looks alright, click “Finish” Now that we have the data on the server we can move to the final step.
Choosing a color for critical asset data.
Select the color drop-down menu, and by convention, we recommend that you use the color orange. This of course can be any color you choose; orange is simply a recommendation that we use frequently across the Polarity Community.
Now that we have the asset data stored, let’s see it in action.
We have a demo alert email that I have been assigned to triage as a SOC analyst.
Immediately you see that all the relevant data I need to determine if it is a True or False Positive, asset criticality, and function of the affected asset are immediately populated. No clicking, pivoting, hunting or distractions. Just the data I need where and when I need it.
Capabilities:
- Polarity can connect to your asset data stores or be uploaded directly to the Polarity Server for instant recall during triage.
- Adding other enrichment sources makes triage extremely fast and exceptionally thorough, no need for an analyst to make a “gut call”.
- Polarity ensures that the most recent information is pulled, not only the information that was pulled at the time of ingestion.
- Via channels or integrations, Polarity can create awareness as to the business relationships between the domain and the enterprise (e.g. Entity: “Polarity.io” Annotation: “Is a trusted partner.”).
- Analysts can move immediately from triage to confident action with full understanding of what assets have been affected by an attack and their criticality within the infrastructure.
- If SOAR playbooks exist, drive by simulations may be initiated.
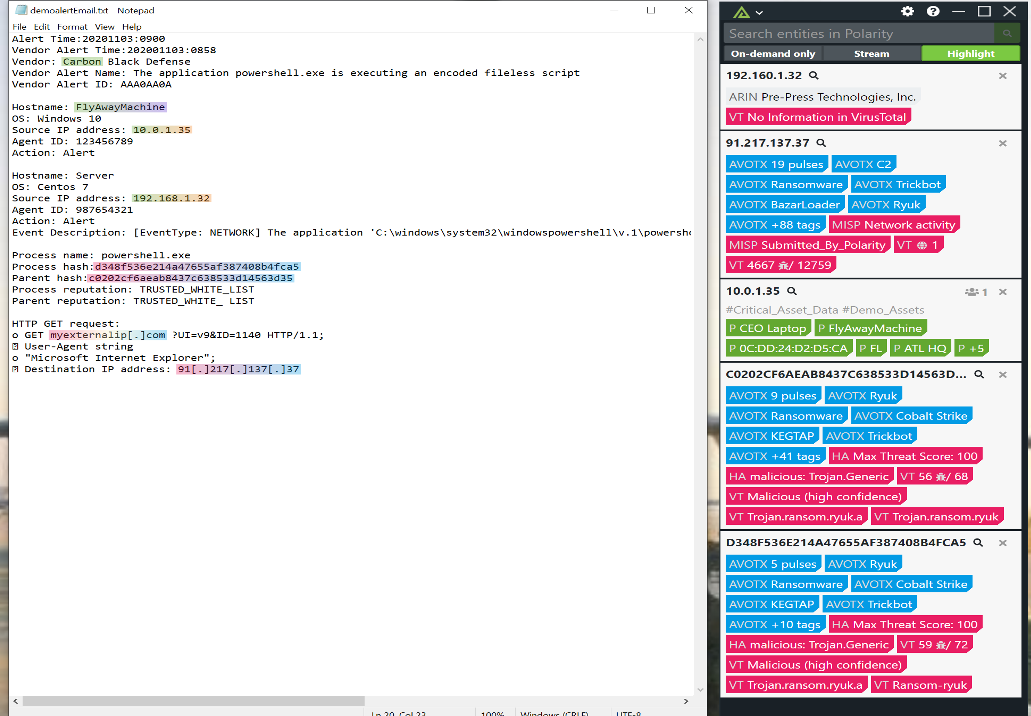
As shown in the above diagram, the Polarity platform provides real-time asset data, including criticality, location, and function. Here we show information provided by the creation of an Asset Channel, AlienVault OTX, Hybrid Analysis, MISP, Virus Total, and Polarity’s OSINT Pivot. You are certainly not limited to these repositories, any data feed to which you are subscribed or use frequently can be provided to your analysts in real-time, no lookups, no clicking around, no shifting tabs, and no cut and pasting. Information when you need it and where you need it. When you are threat hunting, you shouldn’t have to hunt for your data as well.

Real-time domain awareness in Polarity has several benefits including:
- Higher quality, more informed decisions as a direct result of available context sourced from multiple sources.
- Increased efficiencies as the effort to perform desperate searches no longer monopolizes opportunities for more scrutiny and detail-oriented analysis.
- Analysts can immediately determine the criticality of an affected asset within the architecture.
Meet the expert: Terry McGraw

Background: Terry is Head of Customer Success for Polarity and serves as our resident expert in Security Operations and Cyber Threat Analysis. He is a retired Lieutenant Colonel from the United States Army and has over 20 years of providing expertise in cyber security architectural design and operations in both commercial and government sectors.
Terry previously served as the Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks and President of PC Matic Federal. He retired from the United States Army in 2014 completing 27 years of service; the last 10 years of his Army career were leading key Cyber initiatives for the Army’s Network Enterprise and Technology Command, Army Cyber Command and the National Security Agency (NSA). He has multiple combat tours with his culminating assignment, serving as the Director of Operations, Task Force Signal Afghanistan, 160th Signal Brigade (FWD), providing all strategic communications infrastructure in the theater of operations.
Education: BA in History, MSA in Information Systems Engineering, and a graduate of the prestigious US Army School of Information Technology’s Telecommunication Systems Engineering Course.
Relevant Experience: Terry’s work in the Army leading and operating some of the world’s largest and most complex networks as well as 6 years as Vice President of Global Cyber Threat Research and Analysis for Dell SecureWorks providing managed cyber security services to over 4,000 commercial clients and leading it’s six Counter Threat Operations Centers gives him a deep and broad understanding of the Cyber Threat Landscape. His entire professional career has been in designing and managing resilient network architectures ensuring the operational readiness thereof.

