Posted
The Shiйy ФbjЭkt?
ThreatConnect challenges Guccifer 2.0’s claimed attribution for the Democratic National Committee (DNC) breach
Read the full series of ThreatConnect posts following the DNC Breach: “Rebooting Watergate: Tapping into the Democratic National Committee“, “Shiny Object? Guccifer 2.0 and the DNC Breach“, “What’s in a Name Server?“, “Guccifer 2.0: the Man, the Myth, the Legend?“, “Guccifer 2.0: All Roads Lead to Russia“, “FANCY BEAR Has an (IT) Itch that They Can’t Scratch“, “Does a BEAR Leak in the Woods?“, and “Can a BEAR Fit Down a Rabbit Hole?“.
Since the emergence of Guccifer 2.0, researchers and journalists have been combing through his dumped files and details of the Guccifer 2.0 persona to determine whether he’s the independent hacker he claims to be or part of a hasty Russian denial and deception effort to distract focus from the FANCY BEAR and COZY BEAR breaches of the Democratic National Committee (DNC) as detailed by CrowdStrike.
We’re going to lay out the arguments for and against these two competing hypotheses. Building off of the work others have done, ThreatConnect is adding our own observations gleaned from analyzing metadata on Guccifer 2.0’s released files as well as a developing pattern of curious France-based parallels.
Although the proof is not conclusive, we assess Guccifer 2.0 most likely is a Russian denial and deception (D&D) effort that has been cast to sow doubt about the prevailing narrative of Russian perfidy. While targeting political campaigns for espionage purposes is not new, the greatest concern would be the use of the Guccifer 2.0 persona to leak documents of questionable integrity and authenticity in an effort to manipulate the outcome of the U.S. presidential election.
This outcome is not yet out of the question.
However, Russian aims may be more limited. Writing in the September 2014 issue of The Atlantic on Vladimir Putin’s use of information operations, Peter Pomerantsev said, “The point of this new propaganda is not to persuade anyone, but to keep the viewer hooked and distracted–to disrupt Western narratives rather than provide a counternarrative.” Viewed through that lens, Guccifer 2.0 is a pretender – a “false Dmitry” if you will – and a shiny object.
Key Arguments for Two Competing Hypotheses About Guccifer 2.0
| Hypothesis #1: Independent Actor | Hypothesis #2: Denial & Deception Operation | |
| For | ||
| Against |
Timeline of Leaked Document Metadata and DNC Breach-Related Events
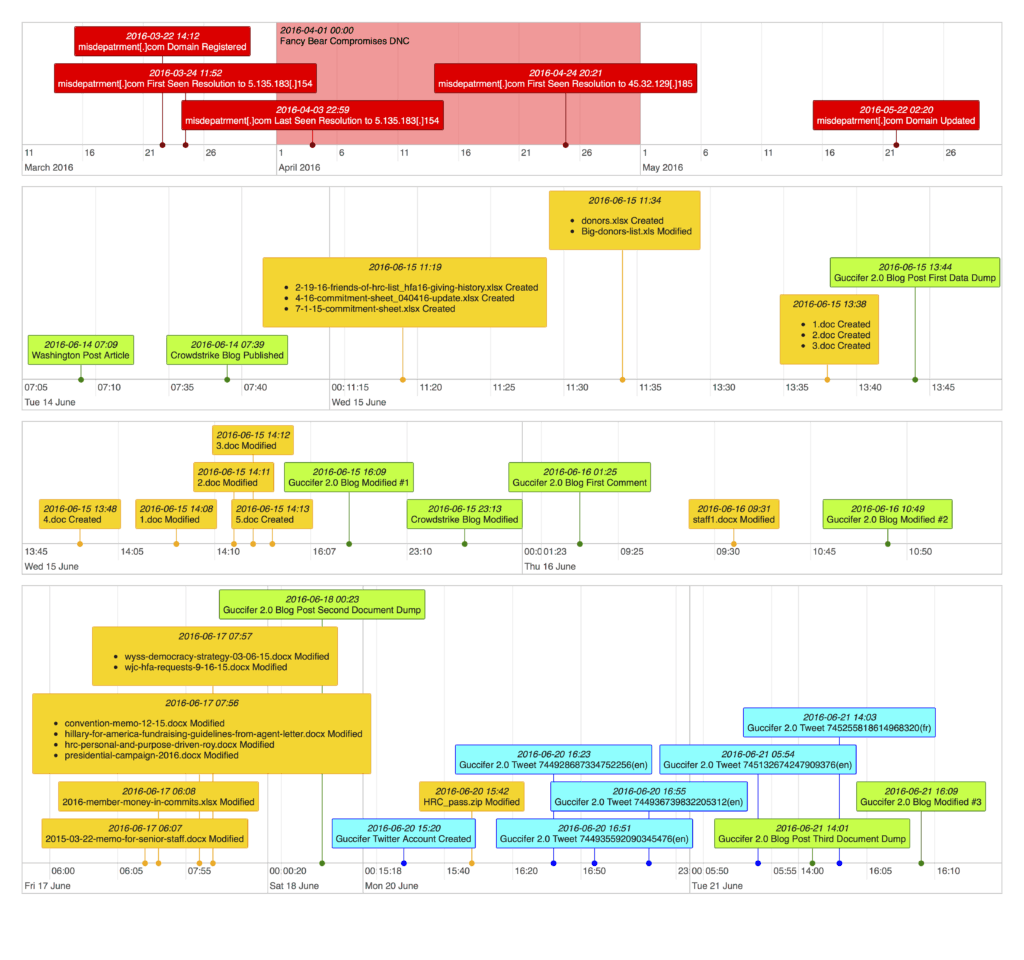
Note: To save space, we collapsed certain time periods where there was no activity. All timestamps were standardized to Coordinated Universal Time (UTC) where possible.
[av_button label=’White Paper: 6 Easy Ways to Advance Your Cybersecurity Program When You Have a Small Team’ link=’manually,http://hubs.ly/H03SMtB0′ link_target=’_blank’ size=’x-large’ position=’center’ icon_select=’yes’ icon_hover=’aviaTBicon_hover’ icon=’ue84d’ font=’entypo-fontello’ color=’theme-color’ custom_bg=’#444444′ custom_font=’#ffffff’ custom_class=” av_uid=’av-188iidh’]
Looking at events temporally helped us see patterns more clearly to inform our comparative analysis.
- All of the documents released in Guccifer 2.0’s first two dumps had file creation dates after the Washington Post article was published based on their metadata, except Big-donors-list.xls which is missing a file create timestamp. The files in the third dump had file creation dates from July 2015, more consistent with Guccifer 2.0’s professed timeline but less consistent with the other files.
- Many of the files have created and modified timestamps that cluster tightly together – some simultaneously. This suggests an unknown application or process likely interacted with the files and/or they were manually manipulated or timestomped.
- The dates within the file names of the first three .xlsx files are inconsistent with file create and modified dates.
- All of the .xlsx and .xls files appear to be created hours before the Guccifer 2.0 WordPress Blog was posted publicly at 2016-06-15T13:44:54+00:00.
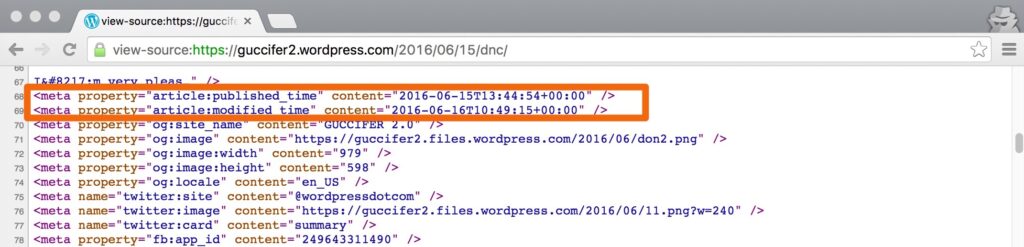
- All .doc files are actually within Rich Text Format (RTF), a legacy, non-standard file format for an organization to consistently use, and maintain file creation and modification times that actually postdate the Guccifer 2.0 blog publish time.
Hypothesis 1: Guccifer 2.0 as an Independent Actor
Key assumption: Our discussion rests on the assumption Guccifer 2.0 is a third actor breaching the DNC in addition to the FANCY BEAR and COZY BEAR breaches identified by CrowdStrike.
Guccifer 2.0 portrays himself as an ideologically-driven hacker – a “freedom fighter” seeking a world “without Illuminati.” In a chat with VICE, he claimed he breached the DNC in the summer of 2015 exploiting a zero-day vulnerability in NGP VAN, an online organizing platform used by the DNC, to hack into the DNC servers.
The Case For Guccifer 2.0 as an Independent Actor
CrowdStrike Report Disrupted Guccifer 2.0’s Desired Timing: A hacktivist looking to have significant social impact might avoid immediately releasing compromised files. By remaining on the DNC network, Guccifer 2.0 could procure additional documents and release them at a time of his choosing closer to the election for maximum impact.
Timestamp Inconsistencies Aren’t a Big Deal: The compromised documents were likely saved in a secure, offline storage medium and not locally on his computer(s) in case he was investigated and/or arrested. The hacktivist might only have immediate access to any documents that he was using as a part of follow-on operations. This might explain why most of the released documents were seemingly altered – the actor might have been using them in unspecified secondary operations.
The Case Against Guccifer 2.0 as an Independent Actor
The NGP VAN Zero-day Attack Vector Seems Off: In the June 21, 2016 interview with VICE, Guccifer 2.0 claimed he exploited a zero-day vulnerability in NGP VAN software. NGP VAN is a software company that provides organizing software used primarily by Democratic members of Congress as well as the liberal parties within the UK and Canada. In December 2015, NGP VAN made mainstream press within reports that the Sanders campaign improperly accessed the Clinton campaign’s voter information due to a software “glitch”. NGP VAN subsequently indicated that it was an “isolated incident that was fairly short in duration” and that a software “patch” was subsequently applied.
It is important to note that within the VICE interview Guccifer 2.0 claims to have breached either the DNC or NGP VAN “last summer“. If true, that would mean that despite all of the attention and focus in December 2015, by both the Sanders and Clinton campaigns as well as the DNC and NGP VAN’s “full audit” no evidence of a breach from an external actor would be identified or reported by either campaign, the DNC, NGP VAN, or any third party such as Guccifer 2.0 for that matter.
According to the MITRE Common Vulnerabilities and Exposures (CVE) website no vulnerabilities within NGP VAN software has been reported. This might be because NGP VAN is not a widely used platform outside of the political sphere, and could be considered a niche software-as-a-service solution because of its specific nature. Rather than accessing NGP VAN platforms via software installed on a DNC computer, most of these products require a user to login via a webservice, and a threat actor would likely be more successful by simply obtaining login credentials for these products rather than attempting to develop directly or use a costly remote zero-day software vulnerability.
This incongruence between a lone ideologically bound hacker purportedly leveraging an unspecified zero-day exploit for a such a niche and specific political organization platform contrasted against evidence of an advanced Russian-based state actor simply using spear phishes with link shorteners to gather webmail credentials from the Clinton campaign stands out to us. The Guccifer 2.0 assertion that the compromise was easy would be more compelling if he claimed to use a spearphishing attack to gain entry.
Within the VICE interview Guccifer 2.0 spoke to details of the internal DNC network and lateral movement in an effort to evade CrowdStrike. References to having “heuristic algorithms” is likely a reference to an unfounded claim to maintain an ability to evade endpoint detection solutions. While the CrowdStrike blog details lateral movement, and dynamic and persistent actors who were routinely updating implants and conducting maintenance in an effort to remain undetected, this is only done in the context of COZY BEAR and FANCY BEAR, not that of a third actor.
As it stands now, none of the Guccifer 2.0 breach details can be independently verified, and if he is indeed an independent actor, he claims to have much stronger technical capabilities than that of his “BEAR” neighbors who were freely operating within the DNC, and are purportedly associated with the Russian Main Intelligence Directorate (GRU) and the Foreign Intelligence Service (FSB).
Guccifer 2.0’s Actions are Atypical Hacktivist Behaviors: Threat actors who conduct operations for political reasons – i.e. to “throw off the political elite” – typically do not stay quiet about their exploits for more than a few days. If the hack was as easy as Guccifer 2.0 claims, it follows logically that other threat actors could have compromised DNC systems easily as well. By holding onto such high profile information for nearly a year, Guccifer 2.0 was likely to be scooped. Politically motivated hackers typically disclose compromises quickly because it helps them gain publicity, followers, and attention to their cause, all of which can be exploited in future operations.
Inconsistencies Between Guccifer 2.0’s Statements and Actions: Guccifer 2.0’s backstory is that he self-identifies as a “freedom fighter” in two separate media engagements, once with The Smoking Gun and another with VICE. If he’s bent on exposing the truth – why alter the files in any way and risk casting any modicum of doubt? Within the VICE interview Guccifer 2.0 is also concerned with doing things that might be a waste of his time. Why consistently alter the document properties and/or modify them in any way, hence risking the integrity of the files in exposing the political elite “illuminati“.
Questionable Integrity of Leaked Docs: Guccifer 2.0’s own admission of altering watermarks on the documents is just the starting point. First and foremost, we would expect individuals in the DNC to be the ones creating and modifying documents in the metadata. We would also expect to see the word documents in a current Microsoft Office format and not a legacy format such as RTF. There are also mismatches in titles of files – where the title contains a date sequence that does not match the created timestamp or the .doc files that have a sequential number naming convention.
Questions About Guccifer 2.0’s Persona and Backstory: Guccifer 2.0’s patterns of speech cast doubt on his claim to be Romanian as well as potentially being one individual person. Phrasing and use of the English language differs slightly between the Twitter account and the blog. Within the chat VICE released, there’s internal discrepancy in the fluidity of the English responses as well as as doubts that Guccifer 2.0’s Romanian is native. Furthermore, Guccifer 2.0 says he has to Google translate Russian during the chat, while the error messages and watermarks reported by ArsTechnica show a heavy Russian language footprint.
Hypothesis #2: Guccifer 2.0 is Part of a Russian Denial & Deception Operation (The Other D&D…)
CrowdStrike announces the breach…and it’s embarrassing to have a perfectly good espionage operation blown during a sensitive political period due to bureaucratic turf wars. So the Russians concoct Guccifer 2.0 to inject doubt into the prevailing narrative that FANCY BEAR and COZY BEAR are behind the DNC breach.
Note: In discussing this hypothesis, we will not focus on whether Guccifer 2.0 is a real, co-opted hacker selected to be the outlet for leaked documents or whether the persona is linked specifically to FANCY BEAR or COZY BEAR.
The Case For the D&D Operation
Precedent and Doctrine: Post-breach denial and deception is not without precedent – particularly for FANCY BEAR. In June 2015, FireEye analysis of an attack targeting France’s TV5 Monde linked the operation to the Russia-based group, despite claims that a hacktivist collective called the CyberCaliphate was responsible. In that denial and deception effort, the supposed CyberCaliphate website was created and hosted on an IP address previously linked to FANCY BEAR, establishing a relatively strong connection between the two groups. On a broader level, this hypothesis is consistent with full-spectrum Information Operations in Russian doctrine.
Inconsistencies and Weak Backstory are Evidence of Haste: VICE’s work researching Guccifer 2.0’s linguistic patterns raises questions about whether he is a native Romanian speaker. We find it odd Guccifer 2.0 seems to have such a weak backstory and underdeveloped persona, and that he leaked the documents only after the CrowdStrike revelations; an unusual practice for an ideologically-driven hacker. However, these traits seem logical for a hastily constructed deception effort.
FANCY BEAR and Guccifer 2.0 both Leveraging France-based parallels: ThreatConnect identified a French theme within both FANCY BEAR’s command and control (C2) infrastructure as well as Guccifer 2.0’s Twitter and reported email account. While the France-based parallels theme is insufficient to link the two, we find it noteworthy.
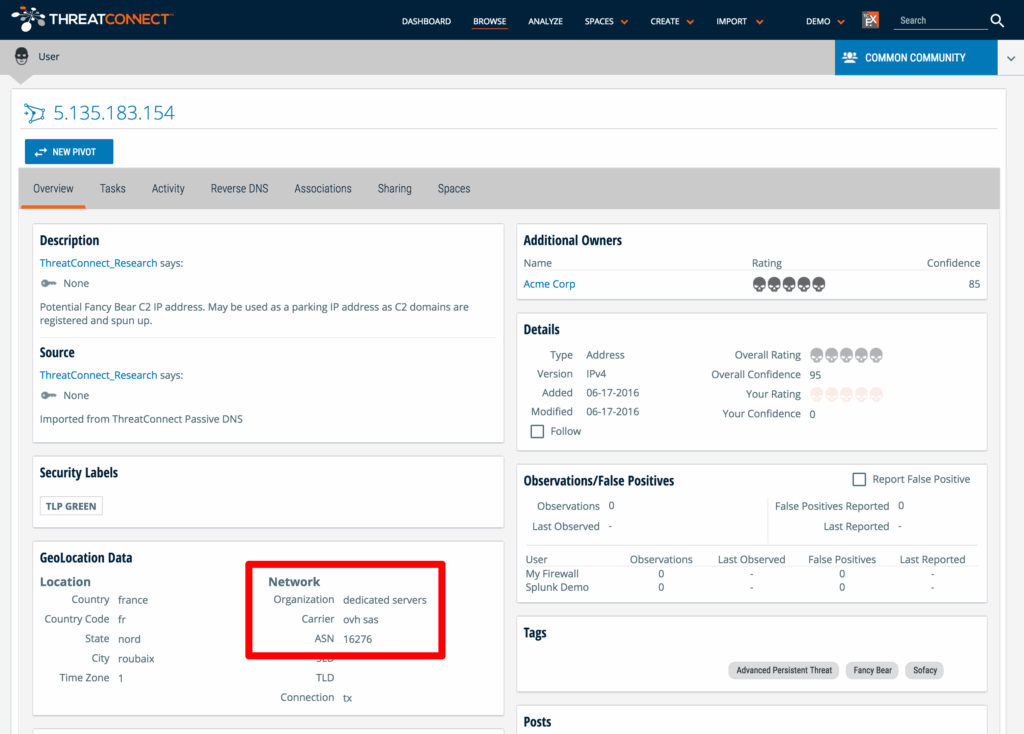
ThreatConnect started with 5.135.183[.]154 (OVH SAS France – ns3290077.ip-5-135-183.eu) the name server used by domains4bitcoins[.]com that FANCY BEAR used to originate or park the new suspicious domain misdepatrment[.]com (detailed in our previous post) as well as the domain windowsupdater[.]net previously identified as FANCY BEAR / Sofacy within ThreatConnect Common Community Incident 20160616A: Additional Fancy Bear Infrastructure.
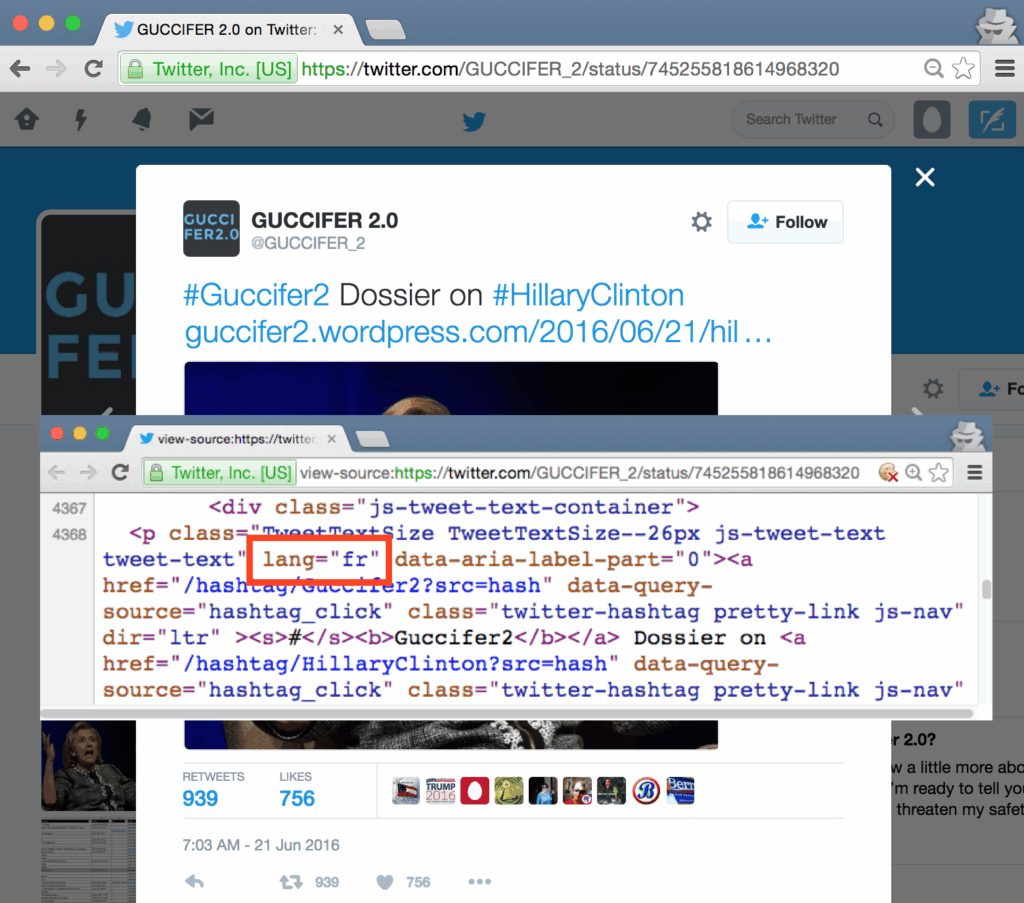
The @GUCCIFER_2 Twitter account also displays some French themes. One of @GUCCIFER_2’s seven tweets (ID #745255818614968320) has the language set to French. Of the 40 accounts @GUCCIFER_2 follows, most are U.S.-based and/or prominent reporters or infosec researchers. Nine of them, however, are French.
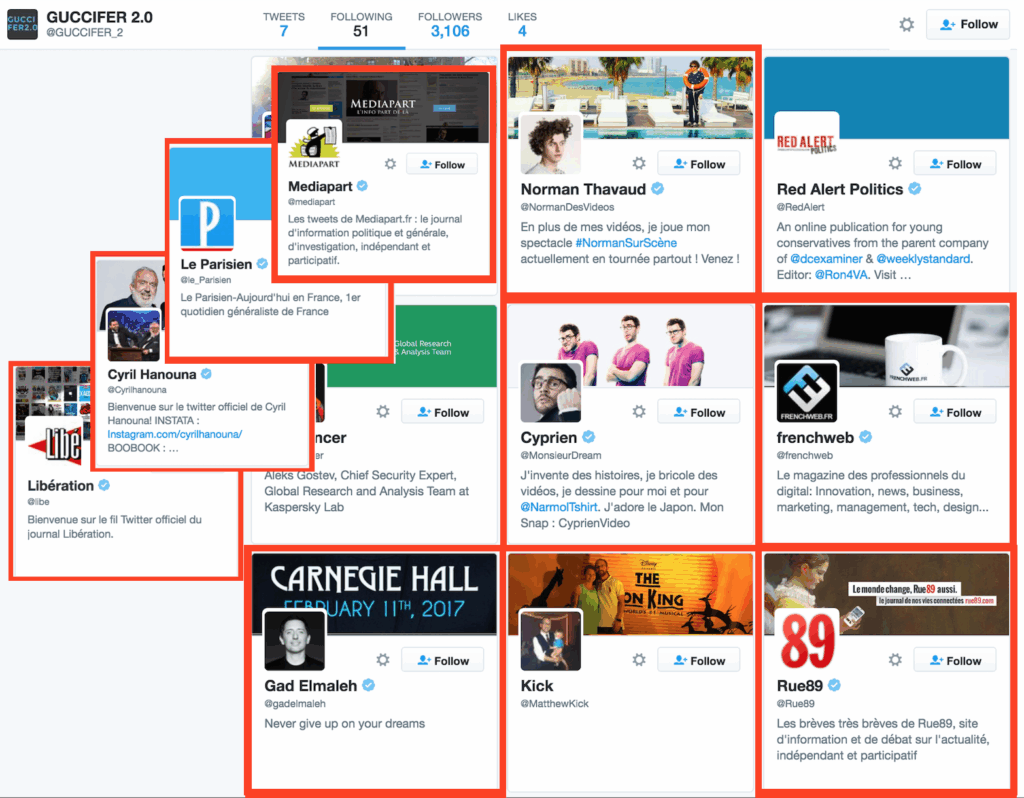
When you create a Twitter account, Twitter recommends a set of accounts to follow based on the geographic IP used to create the new account. We used a VPN in Paris, France to create a new Twitter account, and followed all of the accounts that Twitter suggests during the initial account set up stage. When we compared that set of Twitter IDs to the set of Twitter IDs @GUCCIFER_2 has followed, we found a 24% overlap. However, when we compare only the set of nine French Twitter accounts that @GUCCIFER_2 has followed with our new French Twitter accounts we find an overlap of five out of these original nine Twitter IDs that the Guccifer 2.0 Twitter account is following, suggesting the Twitter handle was created from a French IP. When we also examine a recent TheSmokingGun article, authors who have been in contact with Guccifer 2.0 state “in recent correspondence, [Guccifer 2.0] has used an AOL France e-mail account.” Meaning, if Guccifer 2.0 was to have leveraged French infrastructure (perhaps from OVH or others) to establish accounts secondary specifically for engagement with journalists and social media perhaps this is why we are seeing this underlying French theme across multiple sources.
[av_button label=’White Paper: Maturing a Threat Intelligence Program’ link=’manually,http://hubs.ly/H03SNJh0′ link_target=’_blank’ size=’x-large’ position=’center’ icon_select=’yes’ icon_hover=’aviaTBicon_hover’ icon=’ue84d’ font=’entypo-fontello’ color=’theme-color’ custom_bg=’#444444′ custom_font=’#ffffff’ custom_class=” av_uid=’av-mp7uf9′]
The use of French infrastructure by both FANCY BEAR and Guccifer 2.0 is suspicious, and raises additional questions regarding a potential link between the two. It is possible FANCY BEAR is leveraging French infrastructure not only host the C2 infrastructure but also to host network egress for the @GUCCIFER_2 Twitter account and quite possibly the AOL account used for interaction with TheSmokingGun.
The Case Against a D&D Operation
Why inject so much doubt about the documents? If Guccifer 2.0 was created by FANCY BEAR or COZY BEAR, they would have access to the original, unaltered documents. Posting the original, unaltered documents would make a more compelling case and cause more confusion about attribution.
Actively influencing the American election changes the cost/benefit analysis: Espionage operations against presidential campaigns are not new – even in the digital realm. However, by creating the Guccifer 2.0 persona and leaking documents, Russia would be changing the scope of the original operation. Documents could continue to be leaked in the run-up to the election, and, of course, the integrity of the documents is questionable. Manipulating the election, as opposed to spying on it, runs the risk of retaliation and confrontation with the U.S. for coming after the critical infrastructure of our democratic processes.
Conclusion
Our competing hypotheses review revealed compelling information regarding Guccifer 2.0’s role in this operation: There appears to be strong, yet still circumstantial, evidence supporting the assertions that Guccifer 2.0 is part of a D&D campaign, and not an independent actor. The most compelling arguments for this conclusion are the previously identified Russian D&D campaigns, coupled with remaining questions related to Guccifer 2.0’s persona and backstory.
Conversely, during our analysis we identified inconsistencies in all of the Guccifer 2.0 hypotheses. These inconsistencies may provide Guccifer 2.0 with some “wiggle room” to be able to explain away his actions in a way that continues to divert attention away from Russia. There are still many questions related to this issue that, if answered, may ultimately elicit an update to this analysis. These would include, but are not limited to, the following:
- Was the DNC compromised by three threat actors – COZY BEAR, FANCY BEAR, and Guccifer 2.0 – rather than the two initially publicized?
- If Guccifer 2.0 is in fact an independent actor, what specific infrastructure and capabilities did he use to compromise the DNC?
- Did the publicity surrounding the DNC compromise and remediation efforts undertaken mitigate Guccifer 2.0’s access?
- Have the documents released by Guccifer 2.0 been used in any follow-on operations? If so, against whom?
- What will Guccifer 2.0 do with the entirety of the documents that they claim to have accessed?
Given our conclusion that Guccifer 2.0 likely is part of a D&D campaign, it’s accurate to say that the campaign has, in part, succeeded. Guccifer 2.0’s efforts to become a shiny object have accomplished the goal of keeping some viewers distracted from the main story. Furthermore, Guccifer 2.0 has complicated analysis and established an alternative theory for the DNC compromise. With the U.S. presidential election only five months away, the fact that an external entity has managed to divert attention away from the DNC compromise is concerning. It begs the question, if an external cyber threat actor (independent or otherwise) is trying to impact political discourse in this way, what are they trying to keep us from discussing?
Read the full series of ThreatConnect posts following the DNC Breach: “Rebooting Watergate: Tapping into the Democratic National Committee“, “Shiny Object? Guccifer 2.0 and the DNC Breach“, “What’s in a Name Server?“, “Guccifer 2.0: the Man, the Myth, the Legend?“, “Guccifer 2.0: All Roads Lead to Russia“, “FANCY BEAR Has an (IT) Itch that They Can’t Scratch“, “Does a BEAR Leak in the Woods?“, and “Can a BEAR Fit Down a Rabbit Hole?“.
