Posted
Salt Typhoon—also known in industry and U.S. government reporting as OPERATOR PANDA, RedMike, UNC5807, or GhostEmperor — is a sophisticated, state-sponsored Chinese cyber-espionage group expected to operate under the Ministry of State Security. Active since at least 2019, Salt Typhoon has executed one of the most expansive and consequential global hacking campaigns in modern history.
Salt Typhoon has exploited vulnerabilities in telecommunications infrastructure—particularly routers and core systems—to penetrate networks globally. According to a report in The Wall Street Journal on August 27, 2025, the campaign has affected over 80 countries and 600 organizations, including telecom operators, government agencies, and military infrastructure. Notably, it allowed access to over 1 million call records, including metadata and wiretap-related systems, raising profound national security concerns.
A Joint Cybersecurity Advisory issued by the FBI, CISA, NSA, and numerous international partners categorizes Salt Typhoon’s activity as unprecedented in scale and targeting. FBI Cyber Division Assistant Director Brett Leatherman underscored that Salt Typhoon’s “global indiscriminate targeting isn’t just espionage—it exceeds norms of cyberspace operations.”
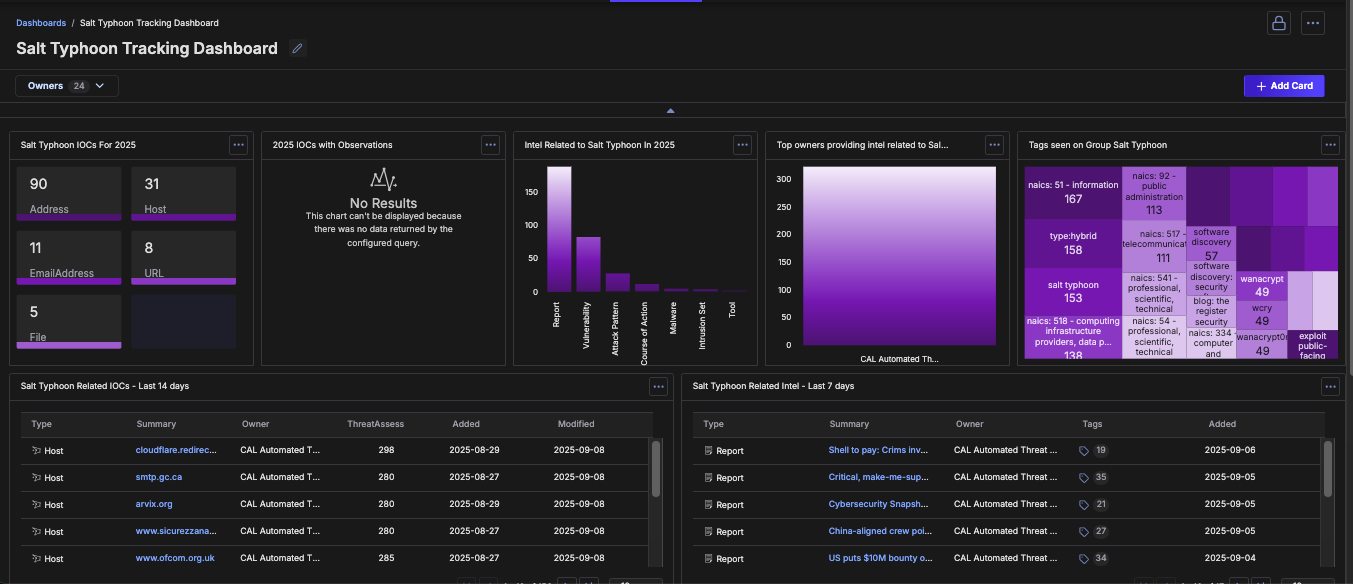
The new Salt Typhoon Dashboard in ThreatConnect offers security teams powerful, centralized visibility into this critical threat.
Key Benefits:
- Centralized Intelligence: Aggregates Salt Typhoon-related IOCs, TTPs, intrusion sets, and telemetry from open sources, commercial feeds, and internal data.
- Continuous Threat Tracking: Monitors real-time updates on actor infrastructure, victimology, exploitation methods, and global trends.
- Accelerated Incident Response: Provides contextualized, enriched intelligence to compress time from detection to response.
- Visual Reporting & Executive Insights: Interactive charts, campaign timelines, and executive-tailored dashboards streamline communication and prioritization.
- Automated Correlation: Leverages ThreatConnect’s automation engine to align Salt Typhoon indicators across adversary profiles, aiding triage and escalation.
With Salt Typhoon’s intrusion into critical networks, including those of major telecom carriers, adversaries now hold the capability to map communications, track movements, and infiltrate high-impact infrastructures.
The Salt Typhoon Dashboard equips defenders with the means to visualize these threats, integrate global context, and act decisively—right within the ThreatConnect platform.
Note: In order to realize the full value of this dashboard, customers may require integration with premium or commercial threat intelligence sources such as those provided by Mandiant, Recorded Future, or CrowdStrike.

Lead Contributor – Andy Smith, Customer Success Engineer
To gain access to the Salt Typhoon Dashboard, please connect with your Customer Success team or reach out to us through our contact form.
Further Resources
For more detailed information and resources on Salt Typhoon, please refer to the following:
| Resource | Description | Link |
| The Wall Street Journal | Per their website, The Wall Street Journal was founded in July 1889. Ever since, the Journal has led the way in chronicling the rise of industries in America and around the world. | WSJ Article |
| Reuters | Reuters is a leading global news organization, recognized for its fast, accurate, and impartial reporting on international business, politics, technology, and current events. | Reuters Article |
| Joint Cyber Security Advisory | The National Security Agency (NSA) and other U.S. and foreign organizations have released a joint Cybersecurity Advisory to expose advanced persistent threat (APT) actors sponsored by the Chinese government targeting telecommunications, government, transportation, lodging, and military infrastructure networks globally and outline appropriate mitigation guidance. | Cybersecurity Advisory |
We urge all organizations to remain vigilant and proactive in their cybersecurity efforts. By implementing these recommendations, you can significantly reduce your risk and protect your critical assets.