Posted
Howdy, and welcome to the ThreatConnect Research Roundup, a collection of recent findings by our Research Team and items from open source publications that have resulted in Observations of related indicators across ThreatConnect’s CAL™ (Collective Analytics Layer).
Note: Viewing the pages linked in this blog post requires a ThreatConnect account.
In this edition, we cover:
- APT35 / Charming Kitten / Phosphorus
- Mustang Panda PlugX
- TAIDOOR
- Emotet
- WastedLocker
- WordPress Vulnerabilities
Roundup Highlight: Recent Probable Charming Kitten Infrastructure
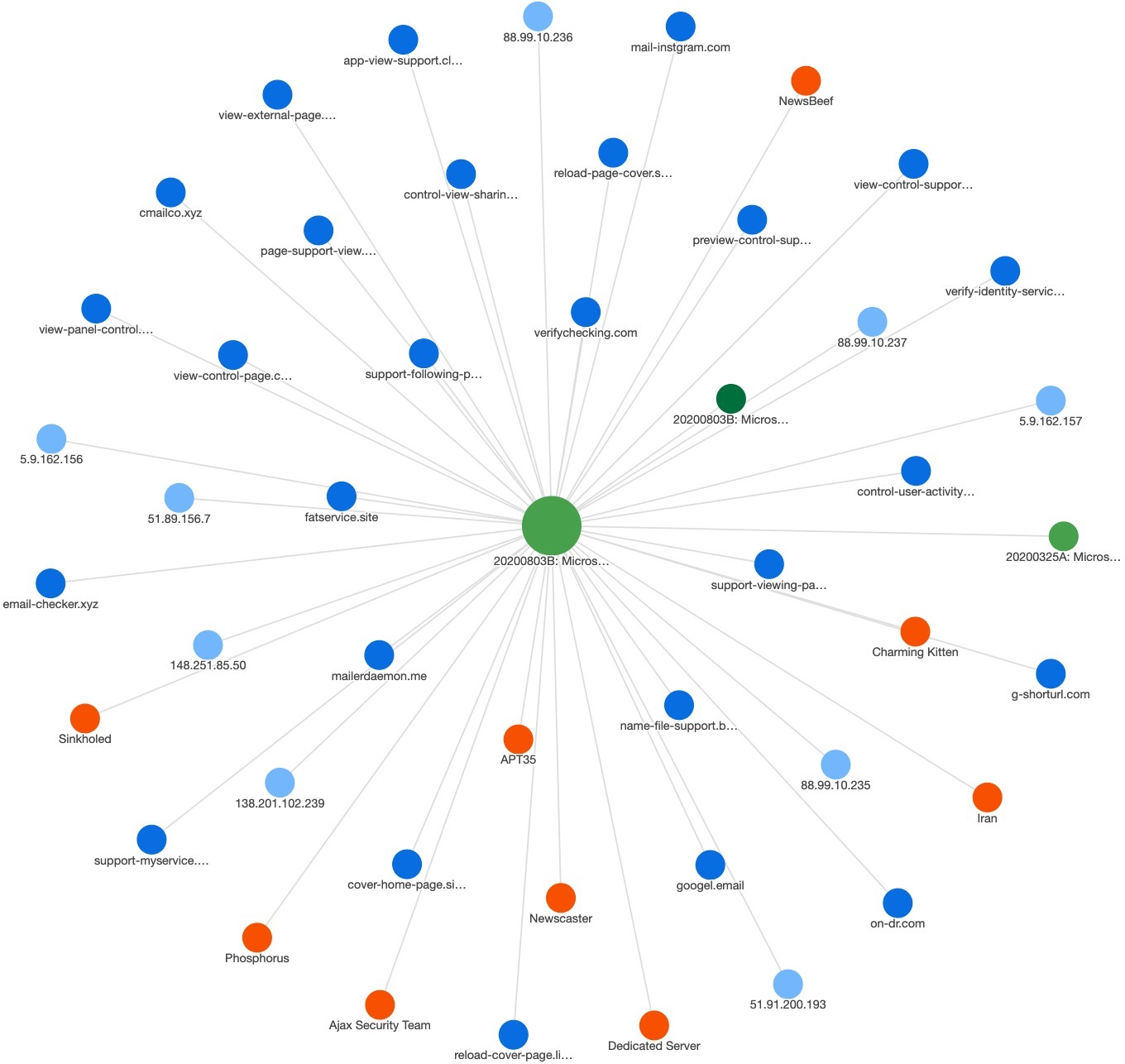
20200803B: Microsoft Phosphorus Sinkhole Domain Siblings
Our highlight in this Roundup is Incident 20200803B: Microsoft Phosphorus Sinkhole Domain Siblings. ThreatConnect Research reviewed the following domains (and the notable IPs that previously hosted them) that began resolving to Microsoft’s Phosphorus sinkhole in late July 2020:
app-view-support.club (5.9.162.156)
mailerdaemon.me (138.201.102.239)
mail-instgram.com (51.91.200.193)
verifychecking.com (148.251.85.50)
support-myservice.com (148.251.85.50)
cmailco.xyz (148.251.85.50)
We identified several additional domains that probably are related to Phosphorus / APT35 / Charming Kitten based on co-locations with the aforementioned domains on likely dedicated servers. The relevant IPs, the additional domains, and other notable IPs hosting those domains include the following:
148.251.85.50
5.9.162.156
view-external-page.best (5.9.162.157, 88.99.10.237, 88.99.10.236, 88.99.10.235)
name-file-support.best (5.9.162.157)
Finally, we reviewed those additional, likely dedicated IPs identified from the hosting history for the co-located domains. This identified another set of domains that probably are associated with Phosphorus based on those co-locations and naming convention reuse:
88.99.10.237
88.99.10.236
88.99.10.235
fatservice.site (prev 51.89.156.7)
5.9.162.157
ThreatConnect Research Team Intelligence: Items recently created or updated in the ThreatConnect Common Community by our Research Team.
- 20200802E: File Matching YARA Rule Associated to Mustang Panda PlugX File d600dff981e3367df19382837972d7b9cf2c20d7cbc4fd4b3856f46472c28da1 was identified via a YARA rule as a Mustang Panda PlugX binary.
- 20200806A: File Matching YARA Rule Associated to Mustang Panda PlugX File f631e8f0c723cccbc5b26387f4100351de2e158b6770e962733734be6ca119d5 was identified via a YARA rule as a Mustang Panda PlugX binary.
Technical Blogs and Reports Incidents with Active and Observed Indicators: Incidents associated to one or more Indicators with an Active status and at least one global Observation across the ThreatConnect community. These analytics are provided by ThreatConnect’s CAL™ (Collective Analytics Layer).
- Daily Emotet IoCs and Notes for 07/29/20 (Source: https://paste.cryptolaemus.com/emotet/2020/07/29/emotet-malware-IoCs_07-29-20.html)
- Daily Emotet IoCs and Notes for 07/30/20 (Source: https://paste.cryptolaemus.com/emotet/2020/07/30/emotet-malware-IoCs_07-30-20.html)
- Investigate | COVID-19 Cybercrime Weekly Update (Source: https://www.riskiq.com/blog/analyst/covid19-cybercrime-update/)
- Threat Roundup for July 24 to July 31 (Source: https://blog.talosintelligence.com/2020/07/threat-roundup-0724-0731.html)
- Threat Assessment: WastedLocker Ransomware Activities (Source: https://unit42.paloaltonetworks.com/wastedlocker/)
- Cybercriminals Targeting Multiple Vulnerabilities in WordPress Plugins (Source: https://www.zscaler.com/blogs/research/cybercriminals-targeting-multiple-vulnerabilities-wordpress-plugins)
- Vulnerabilities Digest: July 2020 (Source: https://blog.sucuri.net/2020/08/vulnerabilities-digest-july-2020.html)
- AR20-216A: MAR-10292089-1.v1 – Chinese Remote Access Trojan: TAIDOOR (Source: https://us-cert.cisa.gov/ncas/analysis-reports/ar20-216a)
- Daily Emotet IoCs and Notes for 08/05/20 (Source: https://paste.cryptolaemus.com/emotet/2020/08/05/emotet-malware-IoCs_08-05-20.html)
To receive ThreatConnect notifications about any of the above, remember to check the “Follow Item” box on that item’s Details page.
